Message forwarding method based on forwarding table of medium access control and system
A message forwarding and forwarding table technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as network storms, network broadcast storms, and operators' telecommunication network oscillations, improve forwarding efficiency, and save network resources, and the effect of improving search efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
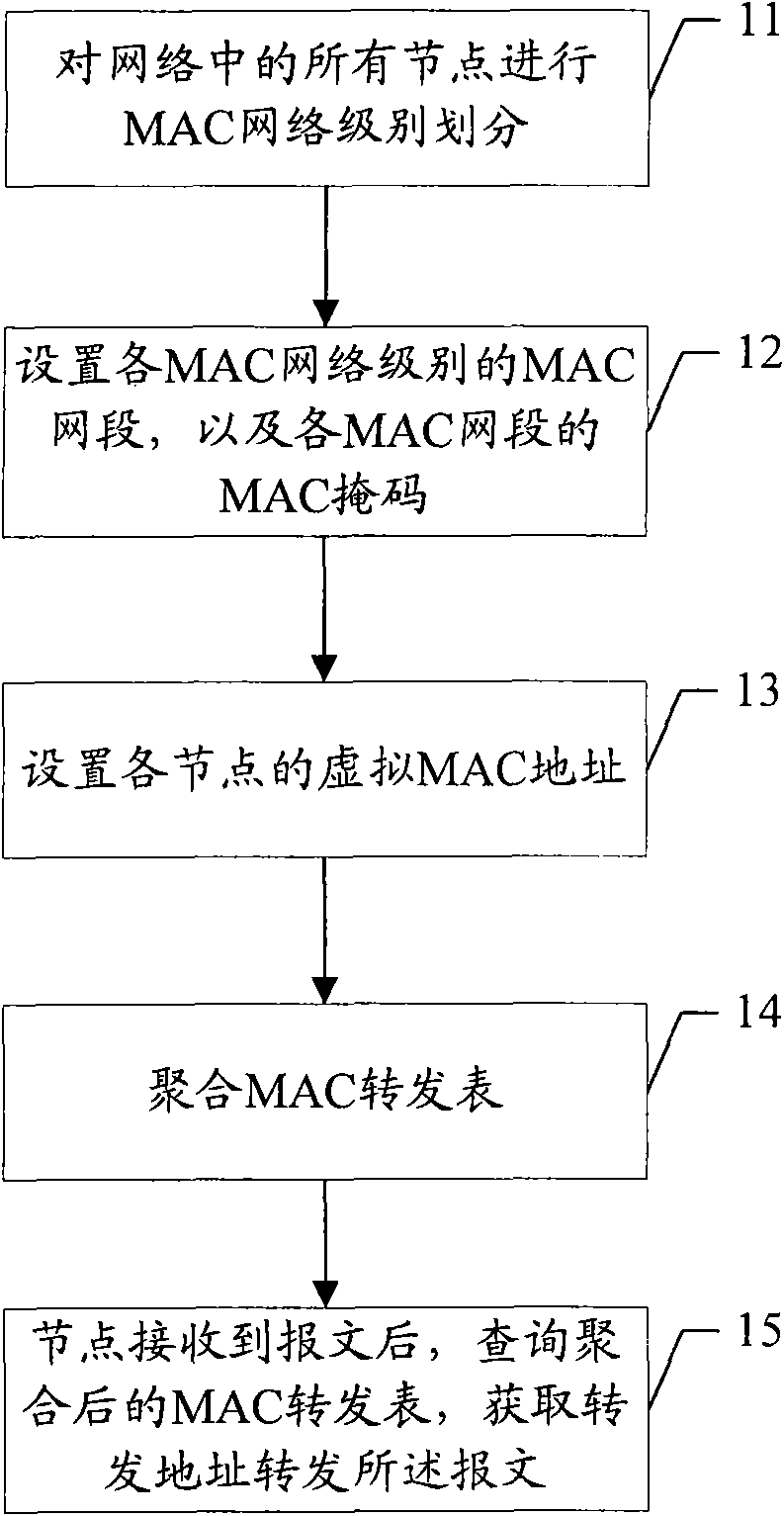
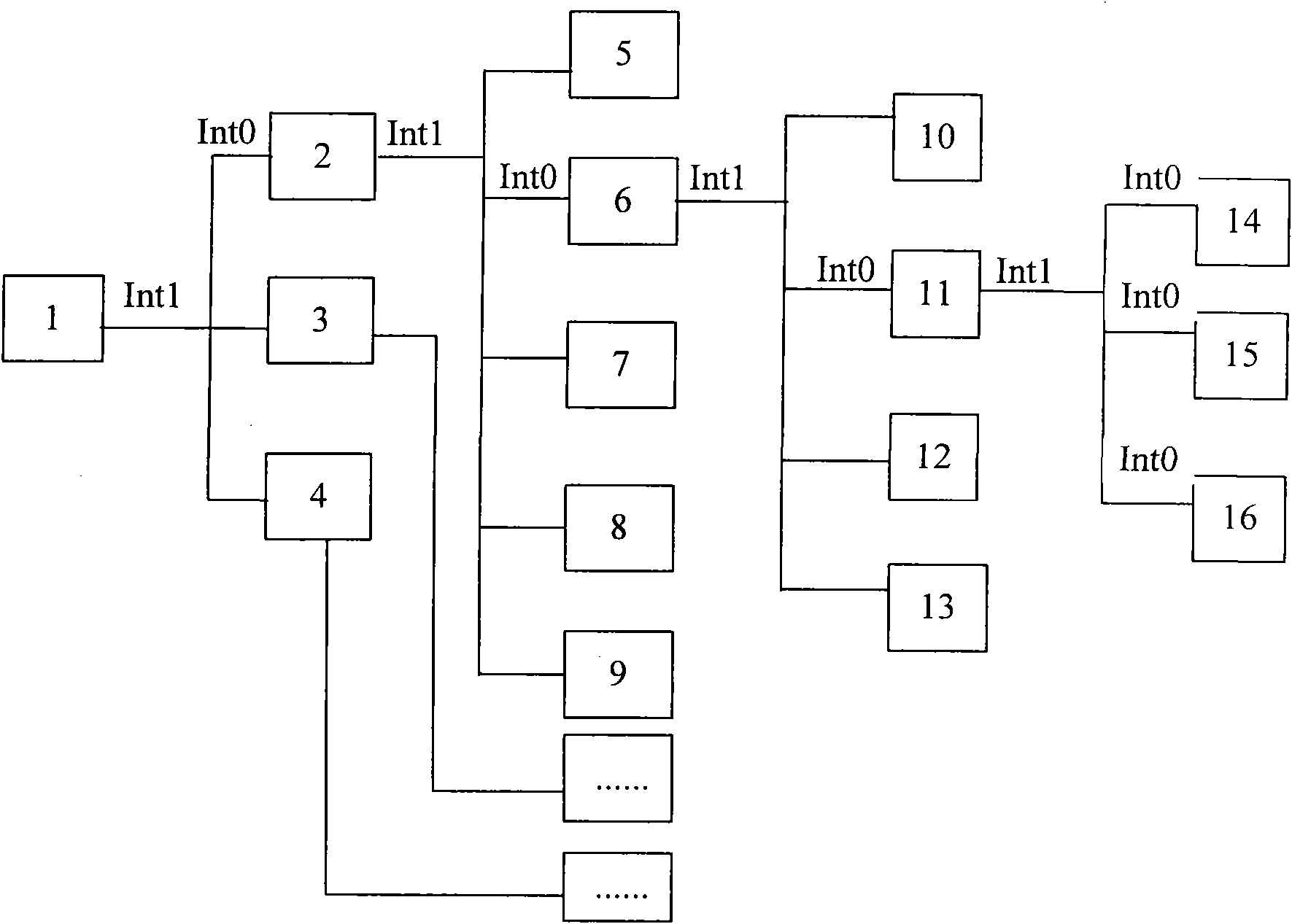
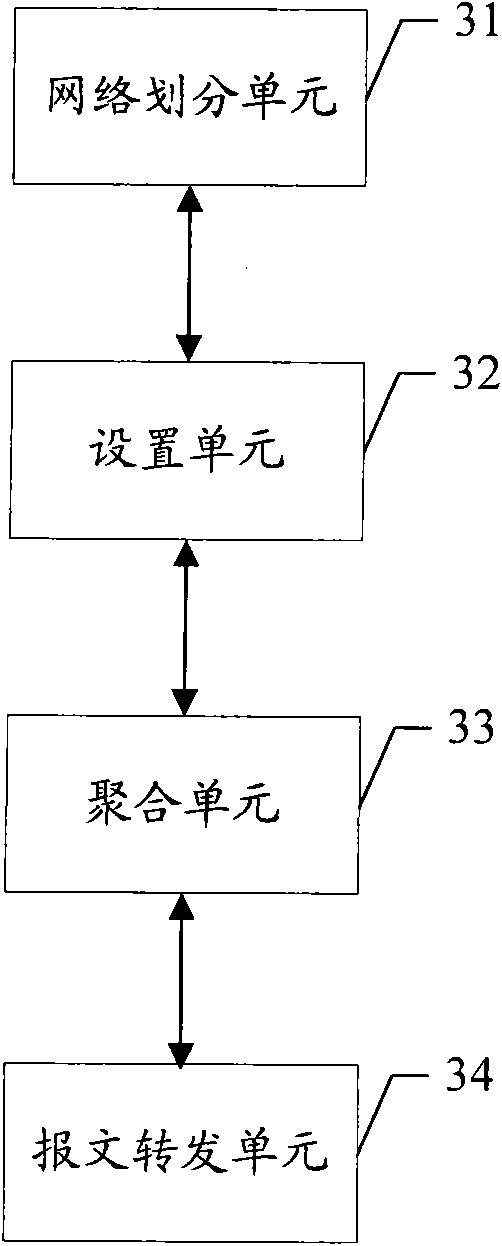
[0022] The basic idea of the present invention is to divide all nodes in the network by MAC network level, and according to the division of MAC network levels, set the MAC network segment of each MAC network level, the MAC mask of each MAC network segment, and each node Then aggregate all the MAC entries in each network segment into one entry to build a MAC forwarding table aggregated by network segment; after receiving the message, the node queries the aggregated MAC forwarding table to obtain the forwarding Address forwarding the received message.
[0023] The implementation of the technical solution will be further described in detail below in conjunction with the drawings.
[0024] figure 1 It is a schematic flow chart of the method for forwarding messages based on the MAC forwarding table of the present invention, such as figure 1 As shown, the message forwarding method based on the MAC forwarding table of the present invention includes the following steps:
[0025] Step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com