Wide area network endpoint access domination (EAD) authentication method, system and terminal
A terminal access and authentication method technology, which is applied in the field of WAN terminal access control authentication, can solve the problems of small WAN link bandwidth, occupying WAN bandwidth, instability, etc., and achieve the effect of saving WAN bandwidth and improving download speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
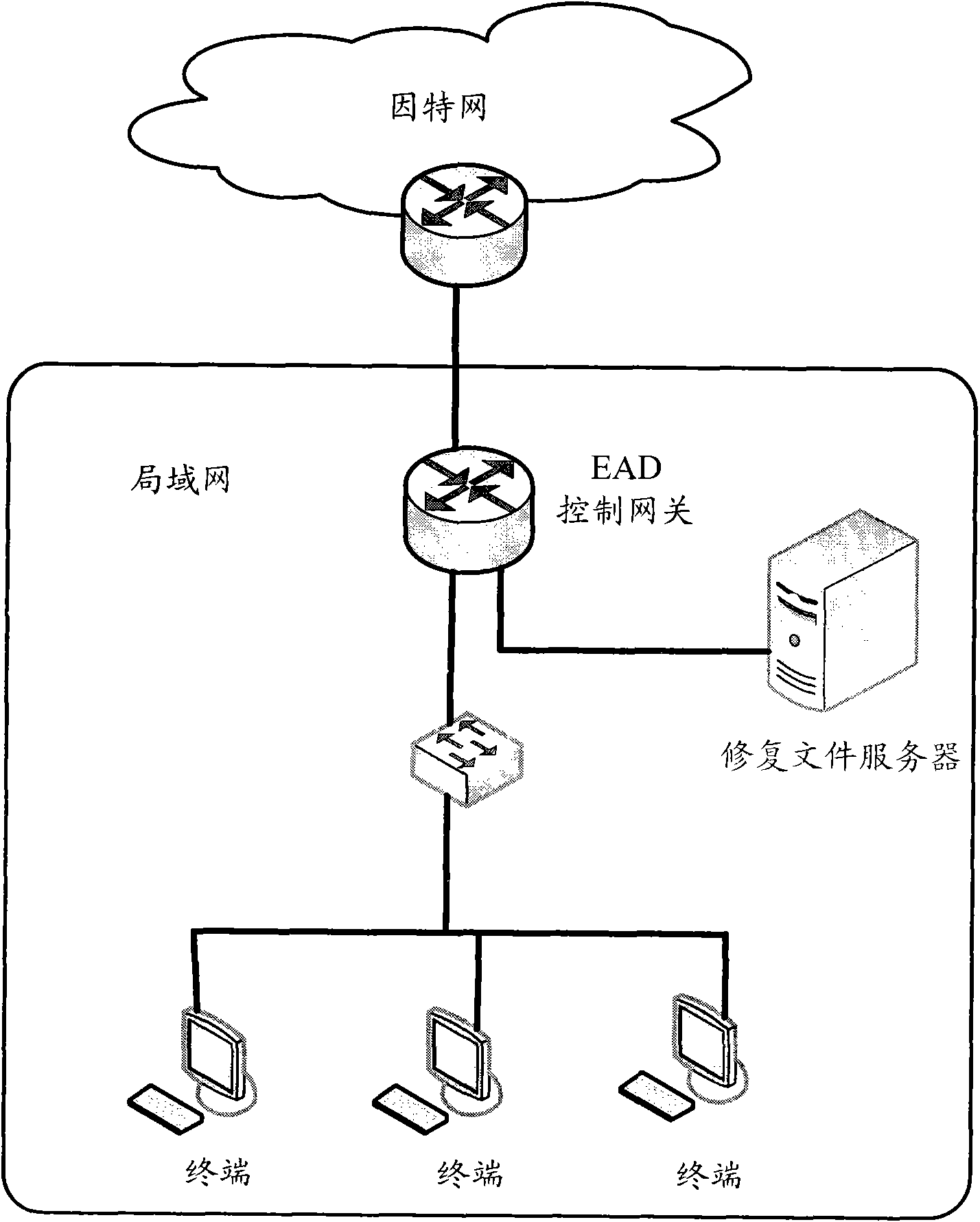
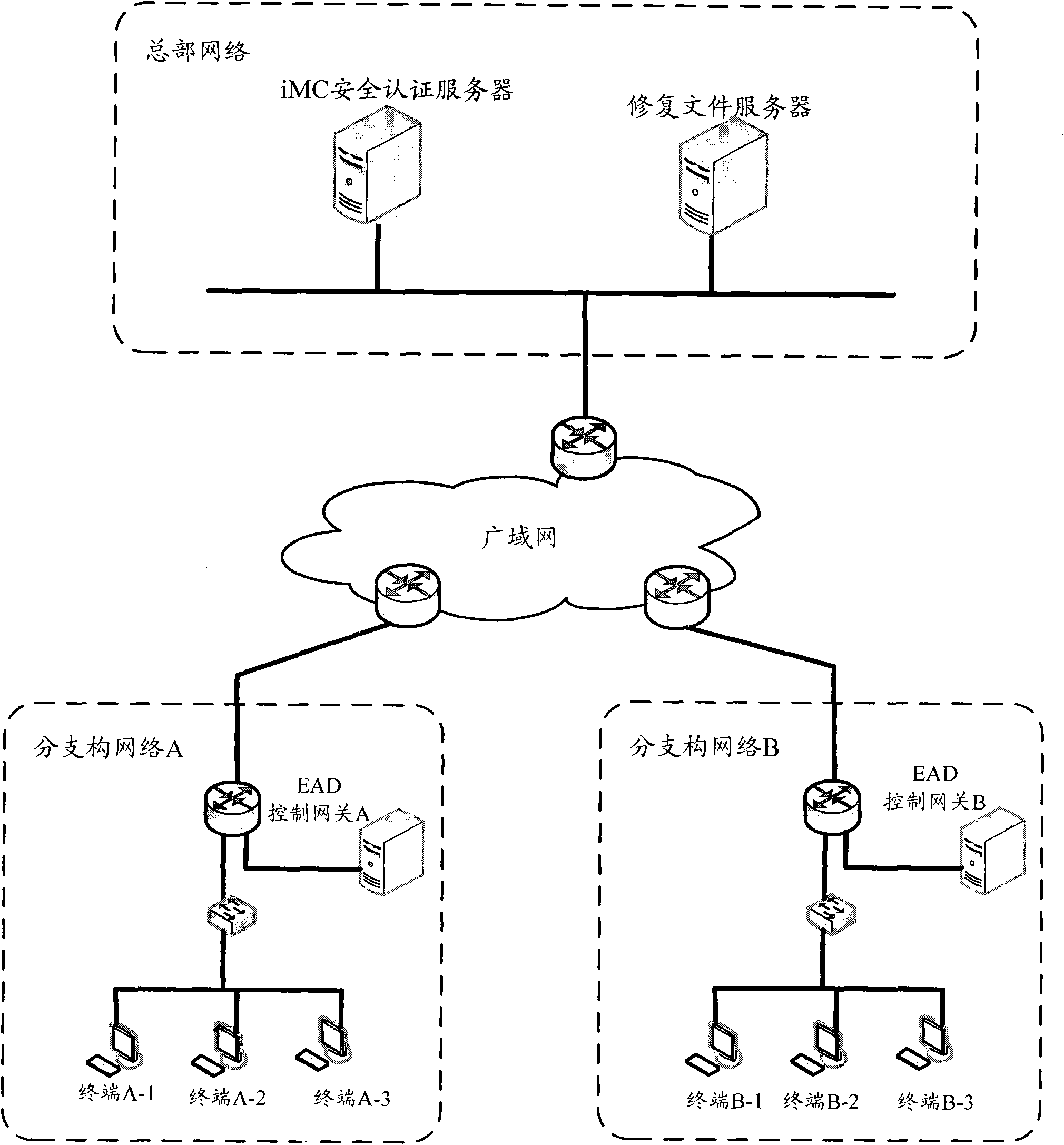
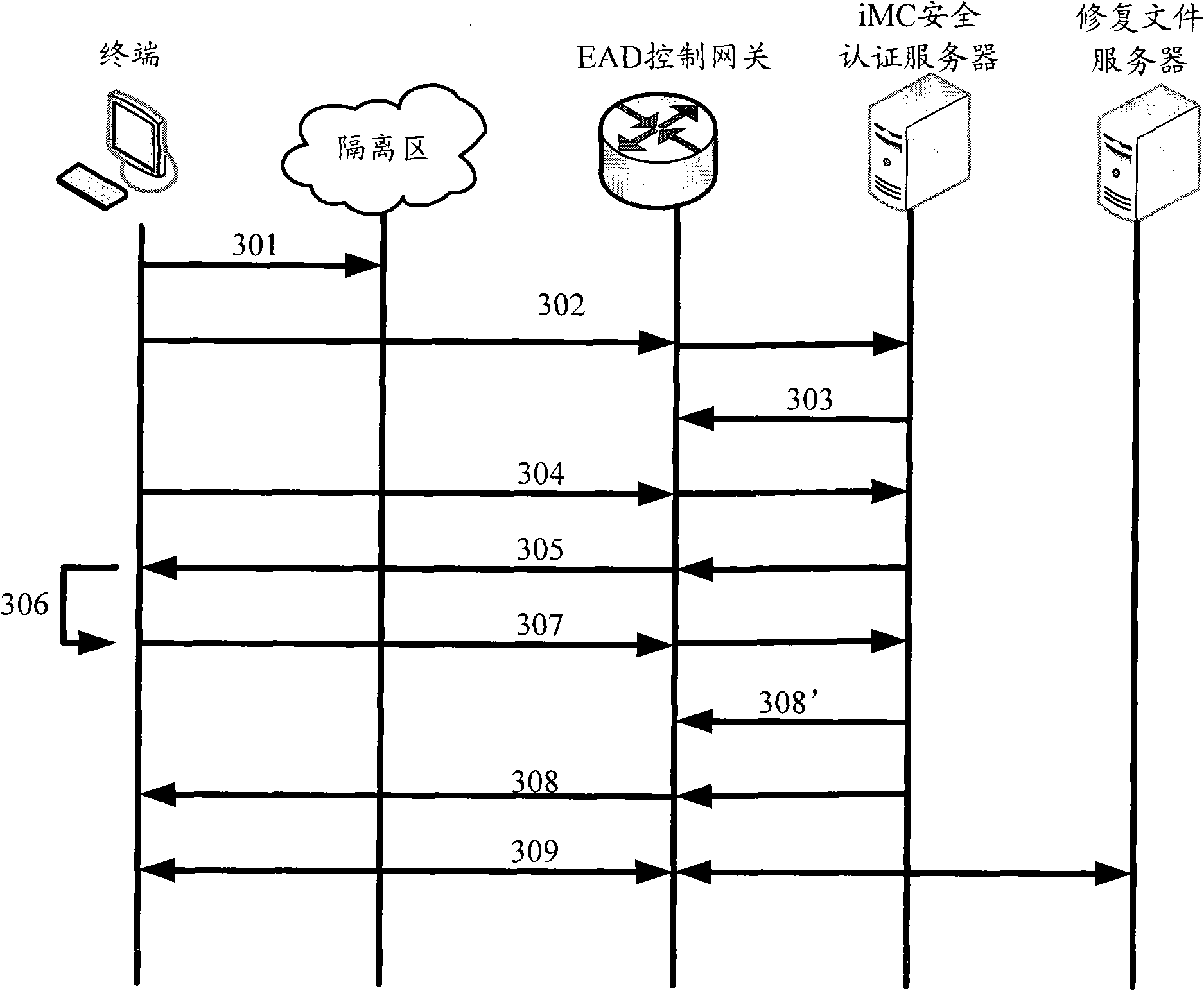
[0052] Figure 4 It is a flowchart of a wide area network EAD authentication method according to an embodiment of the present invention. This method is applied when the iMC security authentication server in the headquarters network performs EAD security checks on the terminals in the branch network, and the iMC security authentication server records the identifiers of each repair file and the corresponding username, such as Figure 4 As shown, the method includes:
[0053] Step 401, the iMC security authentication server receives the security check result reported by the terminal in the branch office network, and when it is determined that the security check result does not match the preset security policy, and the terminal needs to download a specified repair file, it sends a message to the terminal Sending a point-to-point P2P user information table; the P2P user information table includes the user name corresponding to the terminal that has downloaded the specified repair...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com