Safe input method and system for notebook computer
A notebook computer and security input technology, applied in the input field, can solve the problem that input security cannot be effectively guaranteed, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
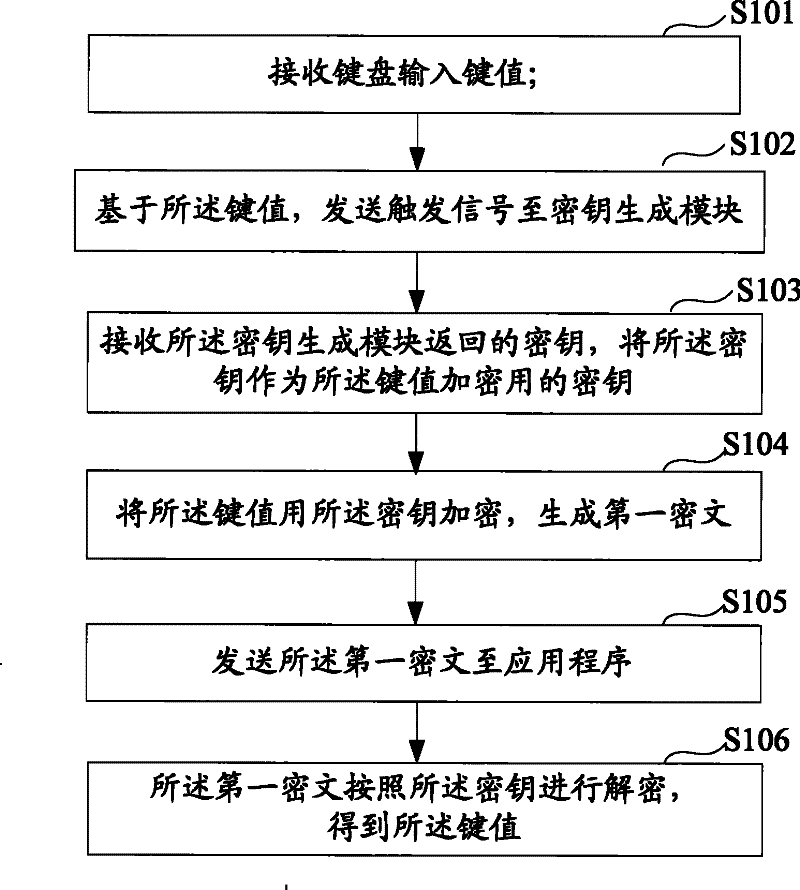
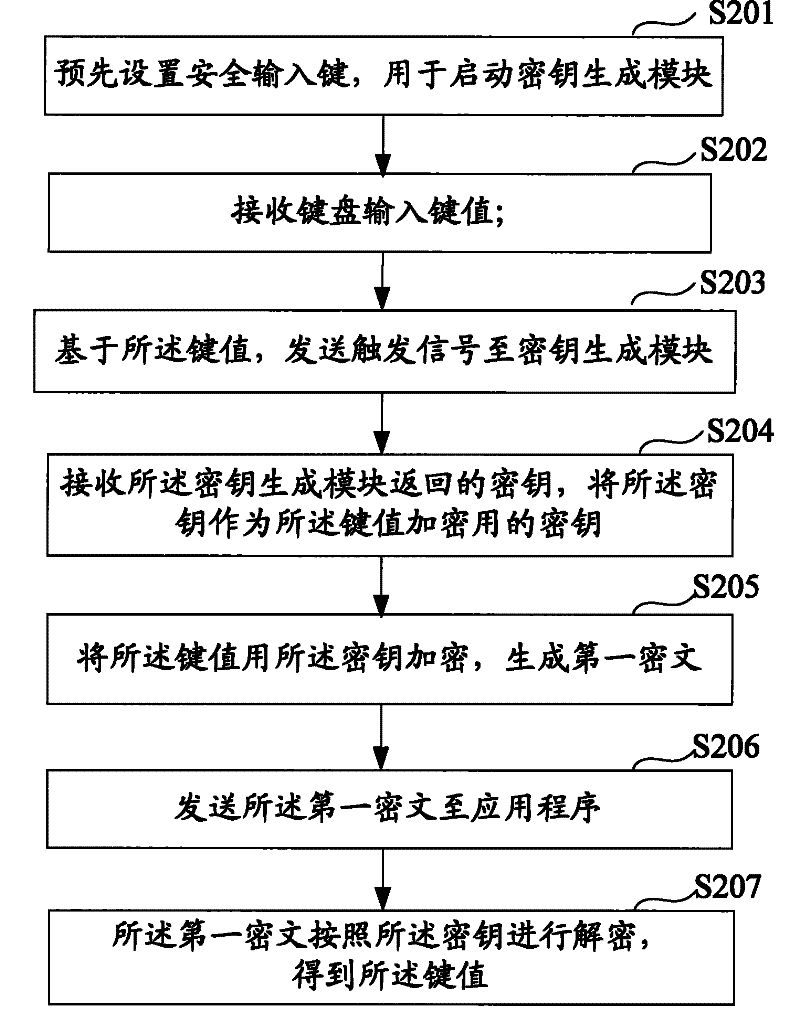
[0050] The embodiment of the present invention provides a notebook computer security input method, which can effectively ensure the security of computer keyboard input.
[0051] In order to more clearly illustrate the notebook computer security input method and the working principle and working process of the system, the following will be described in detail in conjunction with the accompanying drawings.
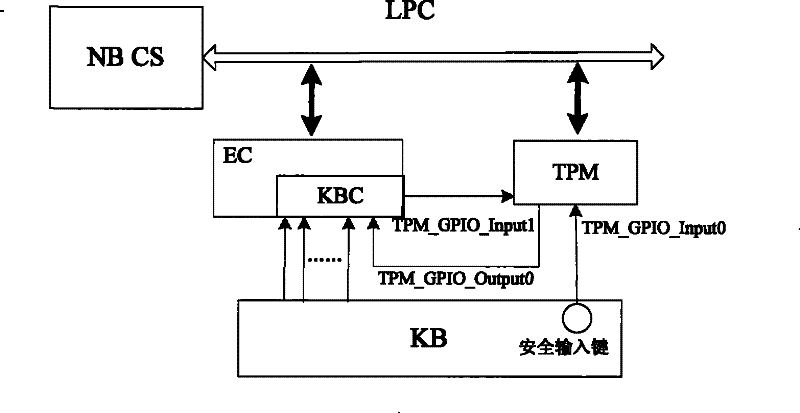
[0052] In order to facilitate the understanding of the notebook computer secure input method and system described in the embodiments of the present invention, firstly, the existing notebook computer hardware is introduced.
[0053] A chipset (Chipset, CS for short) is a core component of a motherboard of an X86 architecture PC in the prior art. According to the different arrangement positions on the motherboard, it is usually divided into North Bridge Chip (NB CS) and South Bridge Chip (SB CS).
[0054] The north bridge chip provides support for CPU type and main frequency,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com