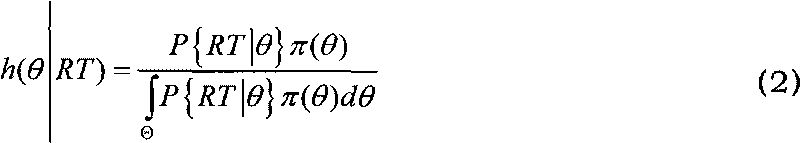System based on Bayesian estimation for evaluating credibility of countermeasure information of computer network
A computer network and Bayesian estimation technology, applied in computer security devices, calculations, instruments, etc., can solve the problems that the evaluation method of CNO intelligence information credibility has not yet appeared
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
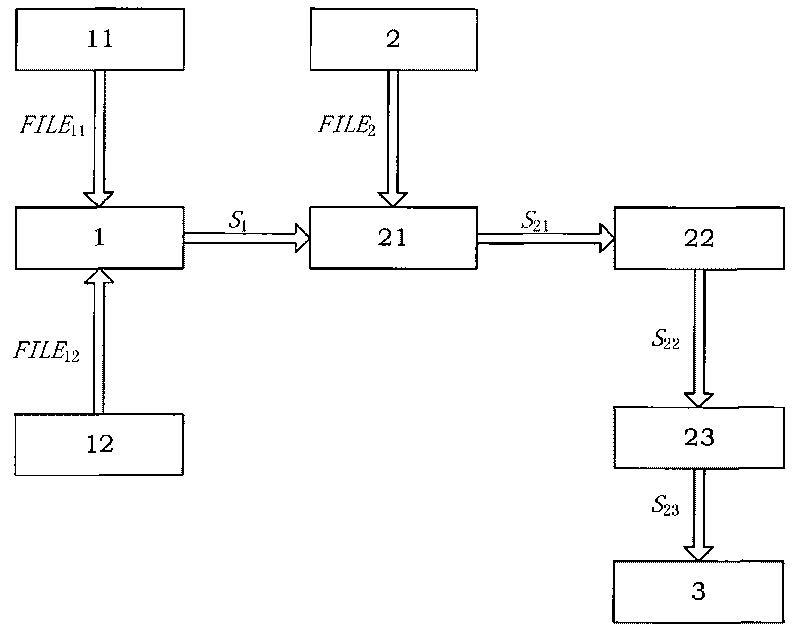
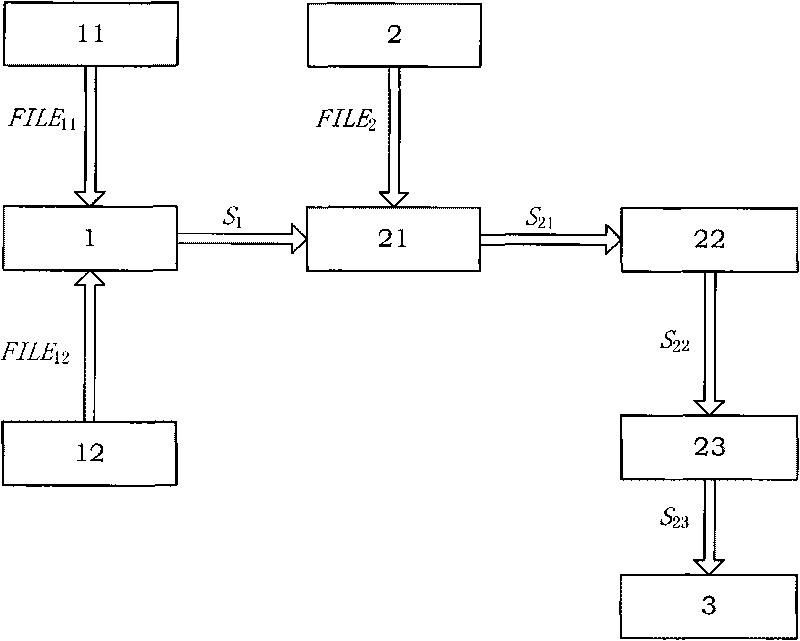
[0051] The target of the CNO in this experiment is the Beihang website server, and the credibility evaluation object is the response time of the Beihang homepage, so it is necessary to establish the prior distribution of the Beihang homepage response time. In the experiment, Wireshark [10] network protocol analyzer was used to intercept the network data packets when visiting the Beihang homepage each time, and the response time was calculated from it. The definition of response time in this experiment is as follows.
[0052] Response time of the home page: The interception time of the server's response to the user's first HTTP message after the TCP three-way handshake connection is established. Generally, it is the fifth packet intercepted by Wireshark for each access packet.
[0053] Considering the impact of network traffic conditions in different time periods of the day on the test results, the experimental data established by the response time prior distribution is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com