Access control method based on attribute and rule
An access control and attribute technology, applied in the field of access control of information resources, can solve problems such as inability to meet system needs, achieve the effect of enhancing flexibility and convenience, strong practicability, and simplifying security management issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
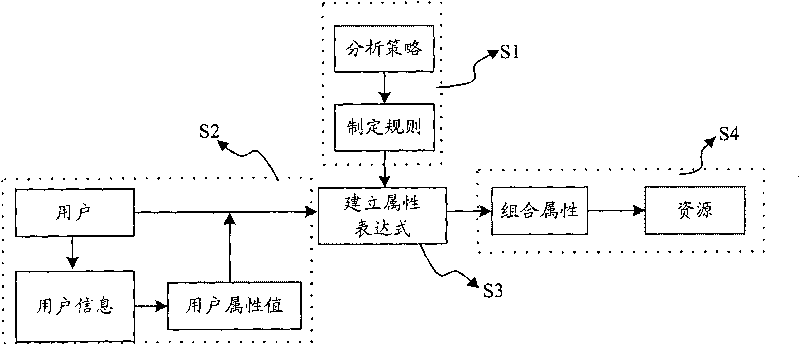
[0029] Some basic concepts and definitions used in this method are as follows:
[0030] 1. User (User) is an entity that operates on resources.
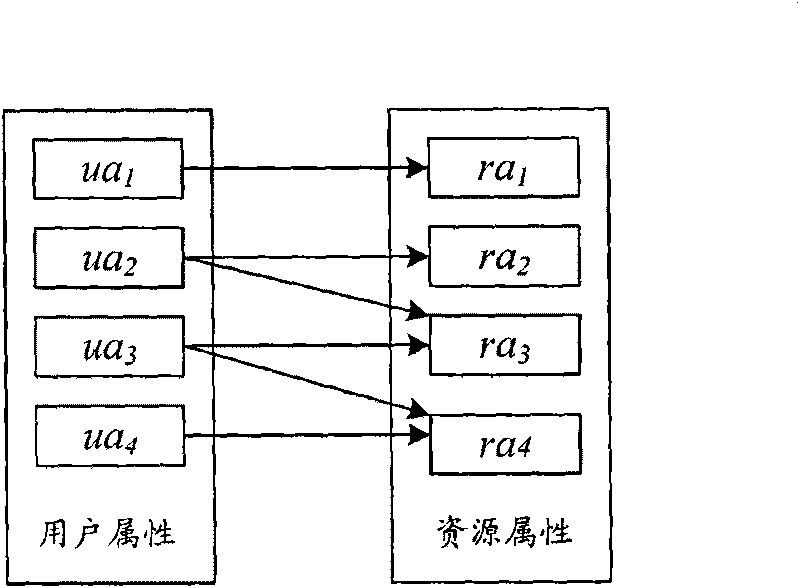
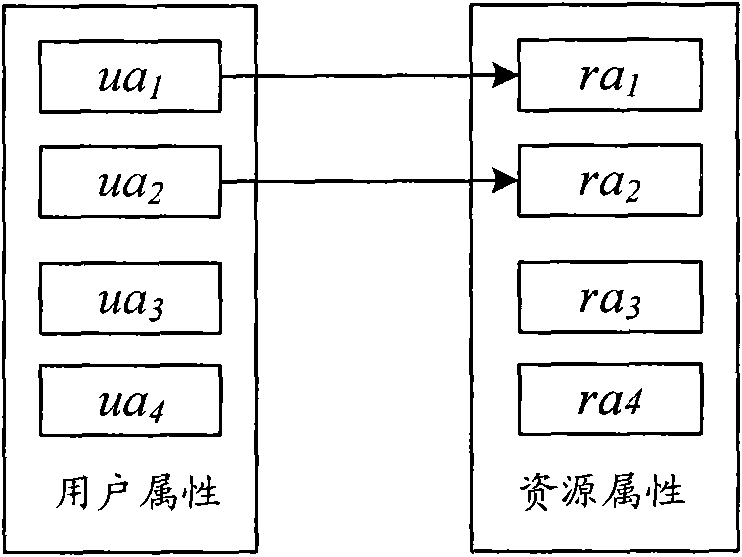
[0031] 2. User Attribute (User Attribute, ua), indicating the identity and characteristics of the user. Such as user nationality (User-Country), user age (User-Age).
[0032] 3. Resource. An entity that is manipulated by a user.
[0033] 4. Resource Attribute (Resource Attribute, ra), which represents information about resource characteristics. Different resources have different corresponding attributes, and the same resource has a variety of different attribute information, such as: movie resources include movie name (Movie-Title), movie content (Movie-Content), movie language (Movie-Language) and movie release time (Movie-ReleaseDate) and other attributes.
[0034] 5. Combined attribute expression (cae), when the access strategy for a certain resource attribute is formulated by certain attributes of the user, the combination o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com