Network attack detection method
A detection method and network attack technology, applied in the field of network security, can solve problems such as false positives, lowering the quality of alarms, and inability to accurately describe attack behaviors.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The core technical content of the present invention will be described in further detail below through embodiments in conjunction with the accompanying drawings.
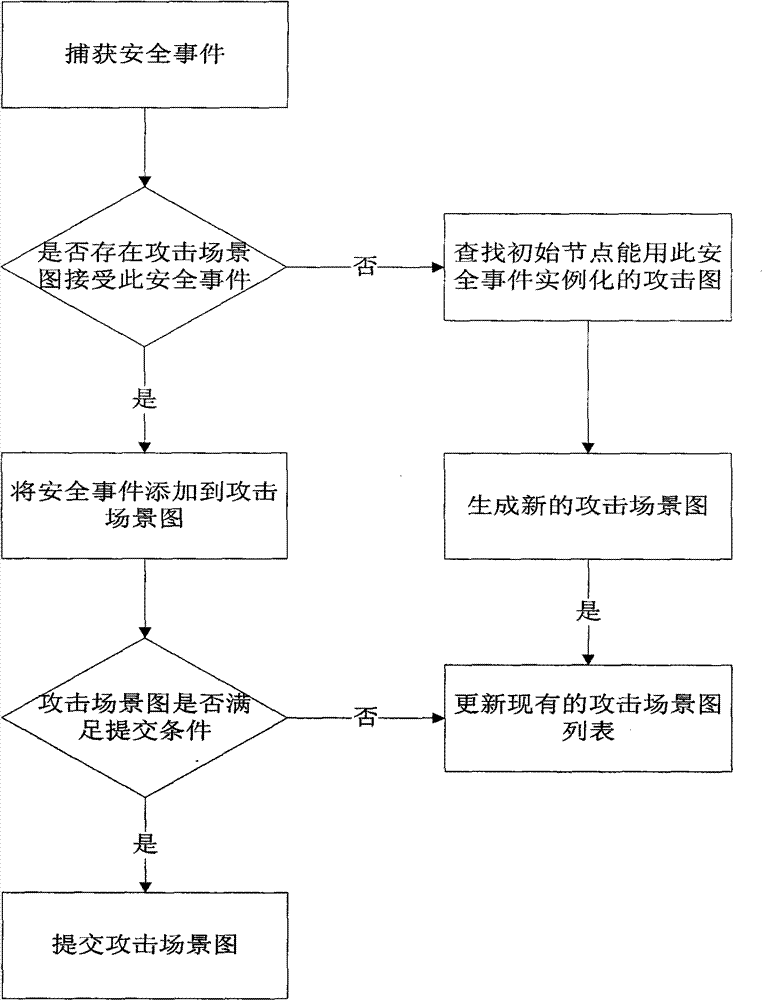
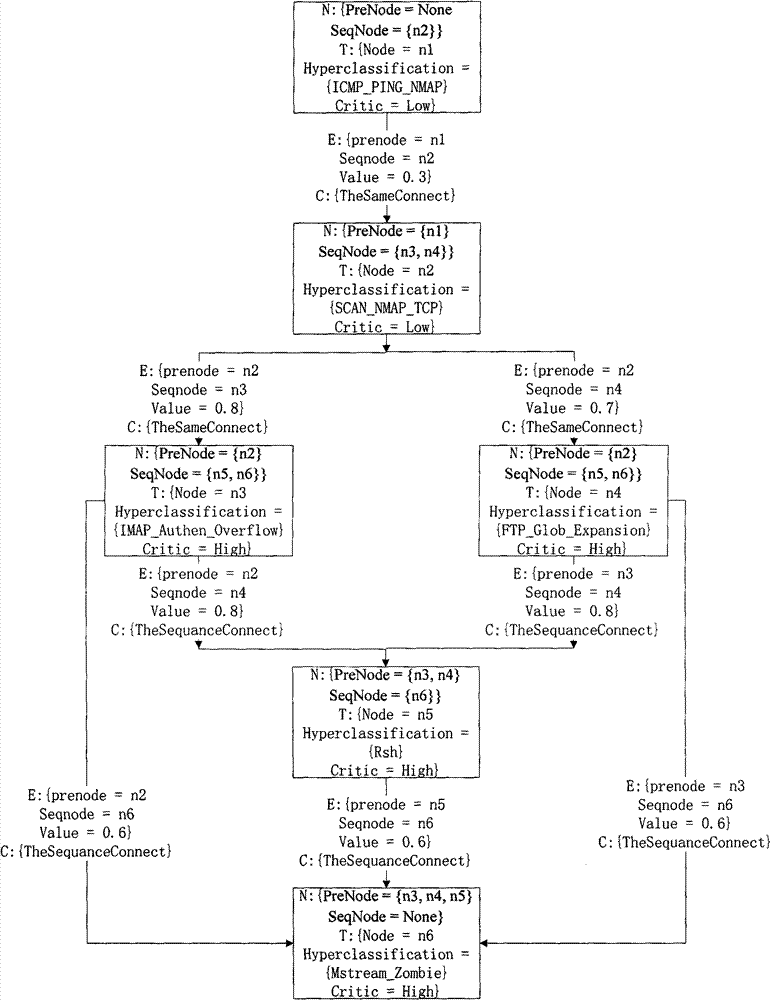
[0062] This embodiment describes a specific network attack detection method based on the attack graph method.
[0063] 1) Implementation details of step 1):
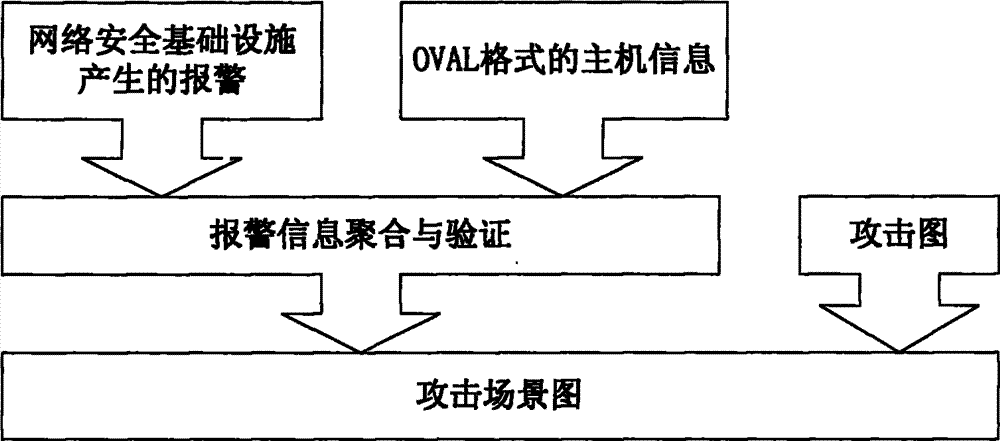
[0064] The network security infrastructure used in the present invention may be a firewall or an intrusion detection system. Taking Snort as an example, Snort is an open source and free network intrusion detection system (NIDS), which can be deployed on the network boundary to detect misuse of all data passing through this boundary. Snort provides interfaces, and users can use these interfaces to develop their own plug-ins and generate alarm information in a custom format. Step 1) The alarm in IDMEF format can be generated by adding a plug-in in Snort.
[0065] 2) Obtain the host status associated with the alarm behavior and use it to judge the validi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com