Software defect based method for quantificationally estimating software credibility
A quantitative evaluation and software defect technology, applied in platform integrity maintenance, instruments, electrical digital data processing, etc., can solve problems that are difficult to quantify, and achieve the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
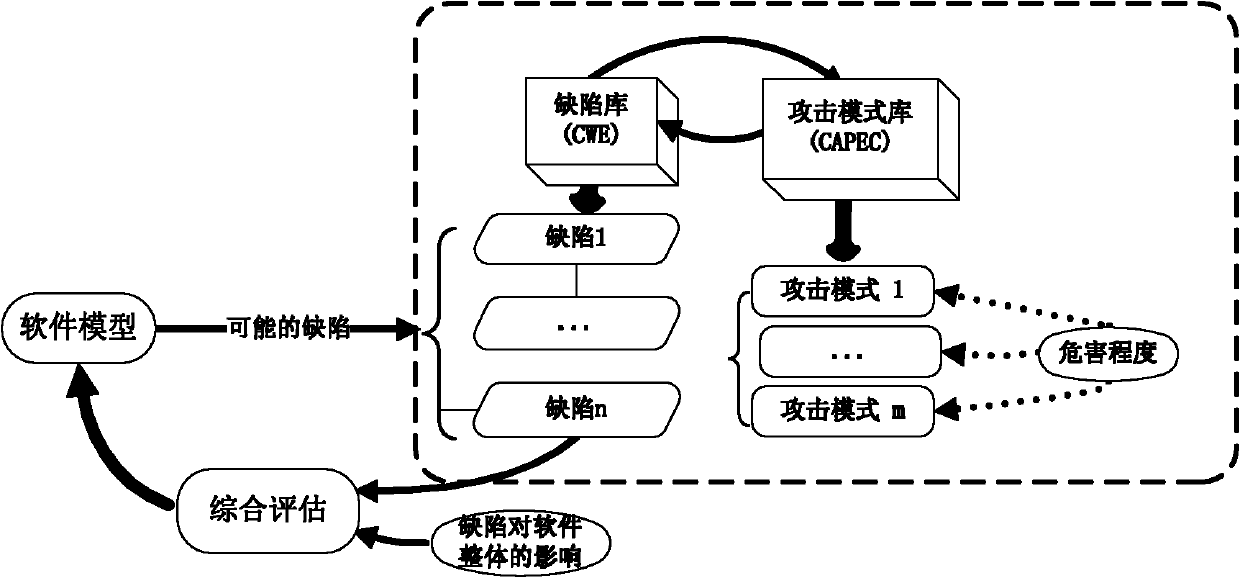
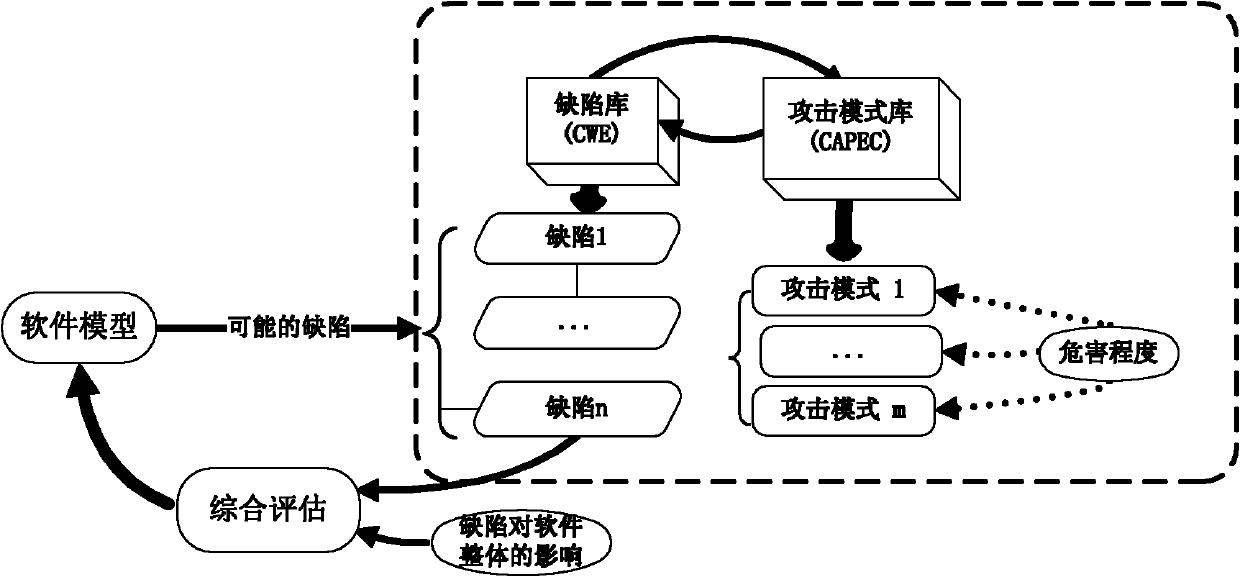
[0024] 1. The exact positioning of the problem:
[0025] Although there is no consensus on the precise definition of trustworthiness, conceptually, trustworthiness can be positioned as a guarantee that a system should be trusted: whether it is due to environmental interference, human error, malicious attack or design and implementation errors. In all cases, the system behaves as expected. Properties covered by this definition include: correctness, reliability, security (secrecy, confidentiality, integrity, availability), privacy security, and fault tolerance [3] Wait. The precise definition of the above concepts can be found in the literature [3], and the hierarchical relationship between them is as follows: figure 1 shown.
[0026] Correctness is a property closely related to software attacks, which can be evaluated through model checking and functional testing; reliability refers to the ability of software to provide stable services, and can be evaluated through performan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com