Enhanced encryption and integrity protection method
An integrity protection and algorithm technology, applied in the field of communication, can solve problems such as the inability to meet the security strength, and achieve the effects of small changes, improved security strength, and increased flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
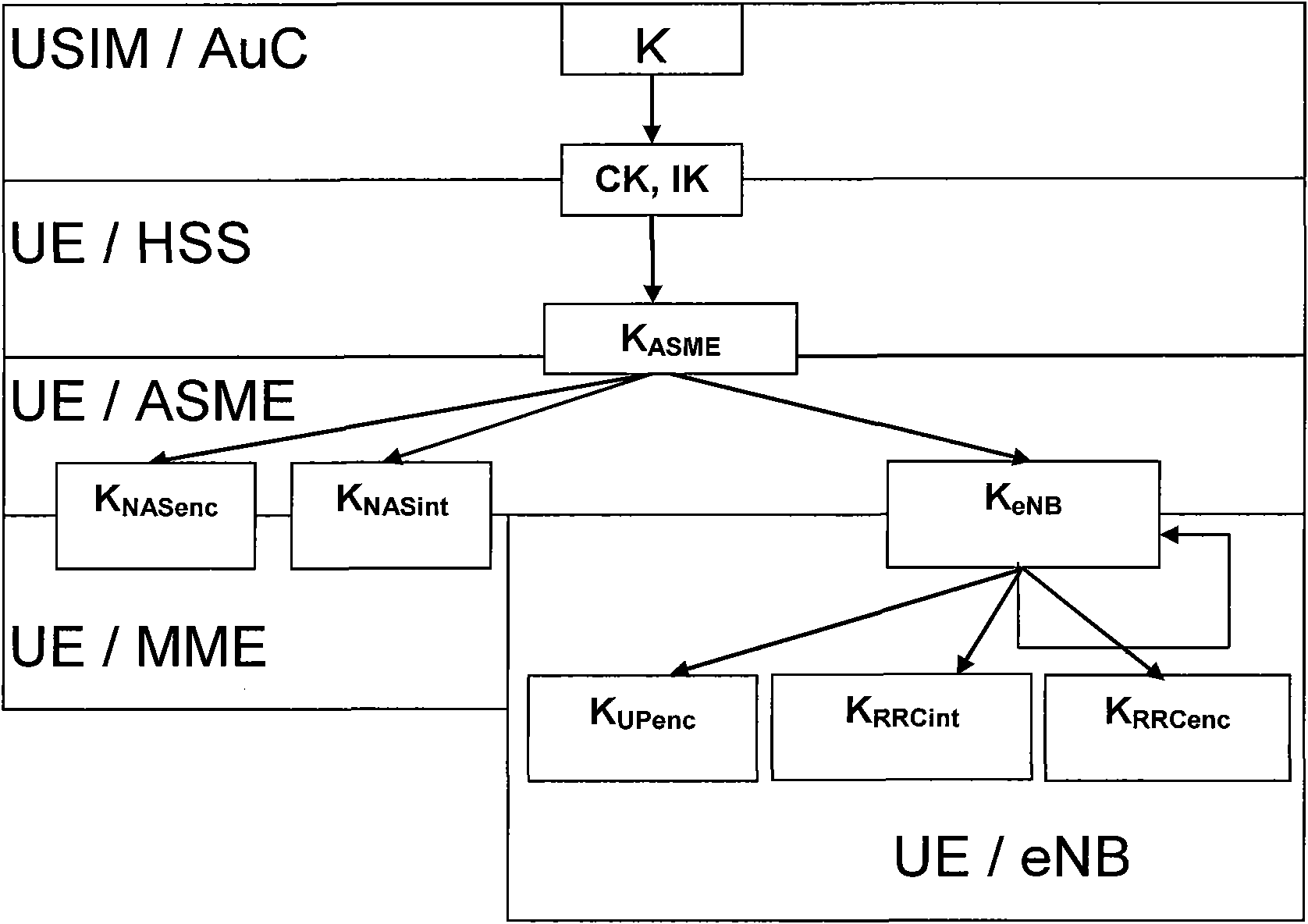
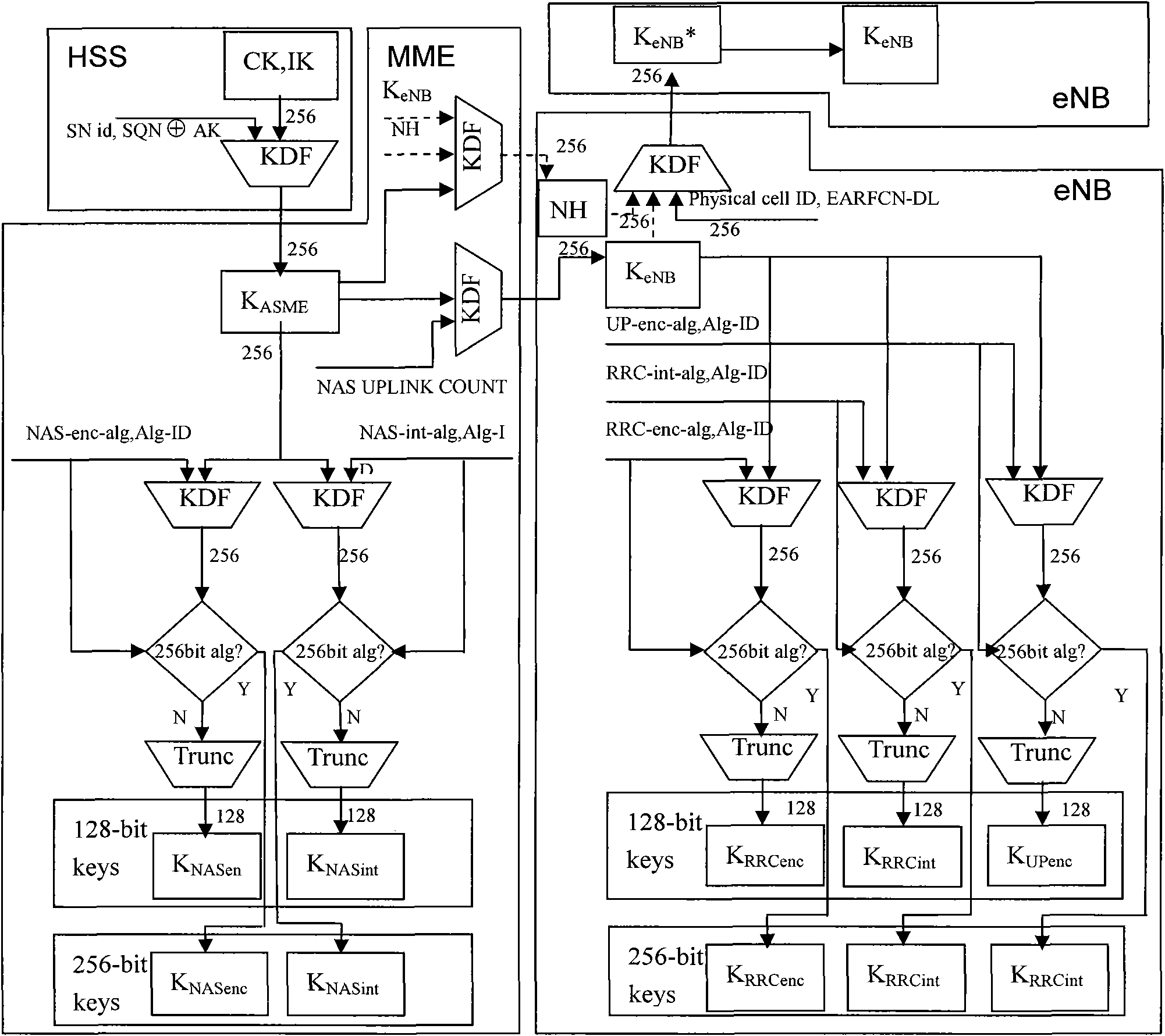
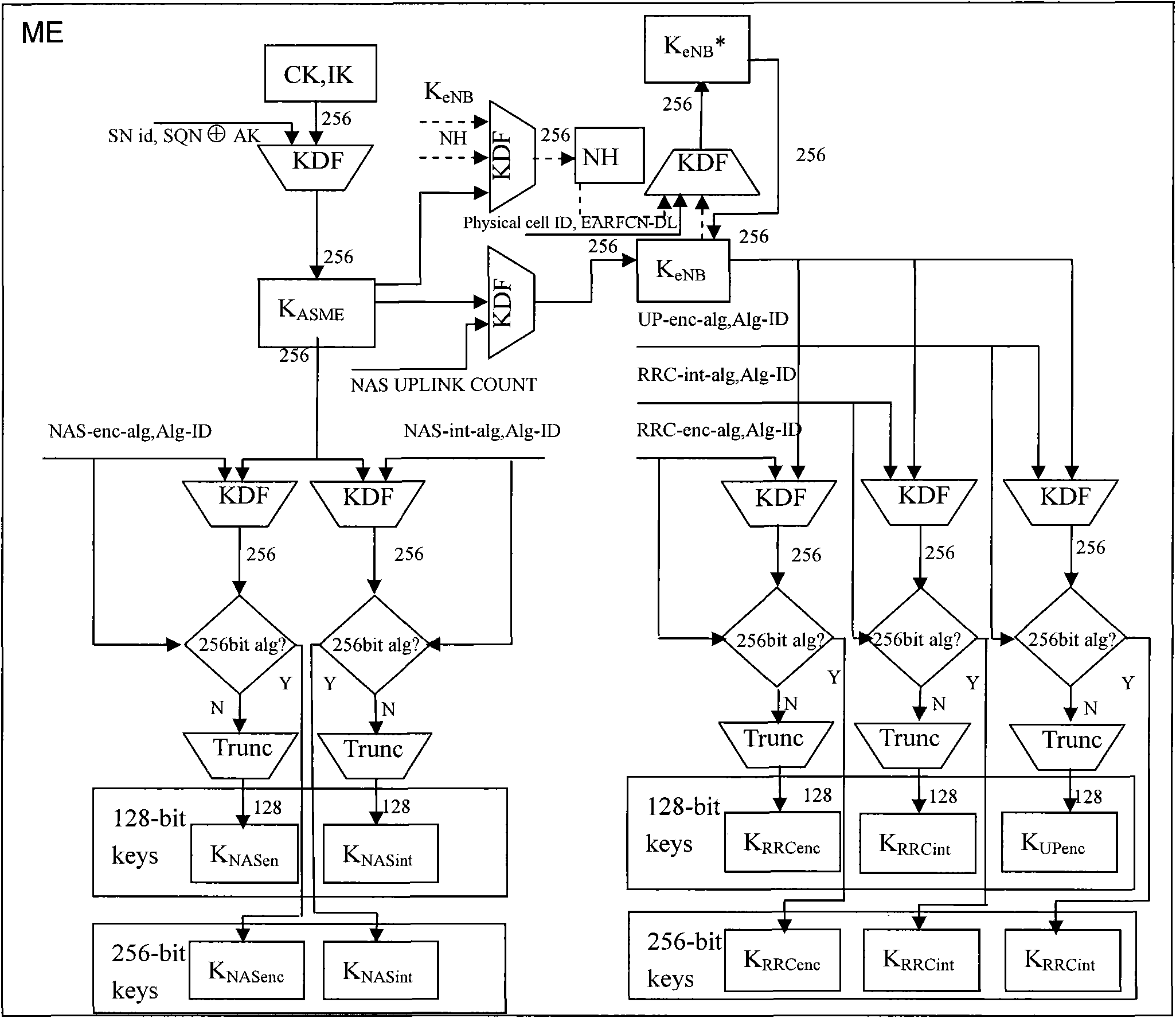
[0077] An enhanced encryption and integrity protection method of the present invention is an improvement based on the existing confidentiality and integrity protection mechanism of LTE / SAE. The original system only supports encryption and integrity algorithms with a key length of 128 bits , the invention enables the system to flexibly support encryption and integrity algorithms with key lengths of 128 bits and 256 bits.
[0078] Concrete scheme of the present invention is as follows:
[0079] i. The key negotiation layer conducts algorithm negotiation and determines the algorithm identification. In order to support two key lengths of 128 bits and 256 bits, the highest bit of the 4-bit algorithm identification is used as the identification key length. When the highest bit is 0, the key length is 128 bits, and when the highest bit is 1, the key length is 256 bits.
[0080] ii. In the key derivation level, determine whether to derive a 128-bit truncated key or a 256-bit non-tru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com