Method, device and system for encryption and decryption
An encryption method and encryption algorithm technology, applied in the field of digital anti-counterfeiting, can solve the problems of low security of encryption and decryption methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
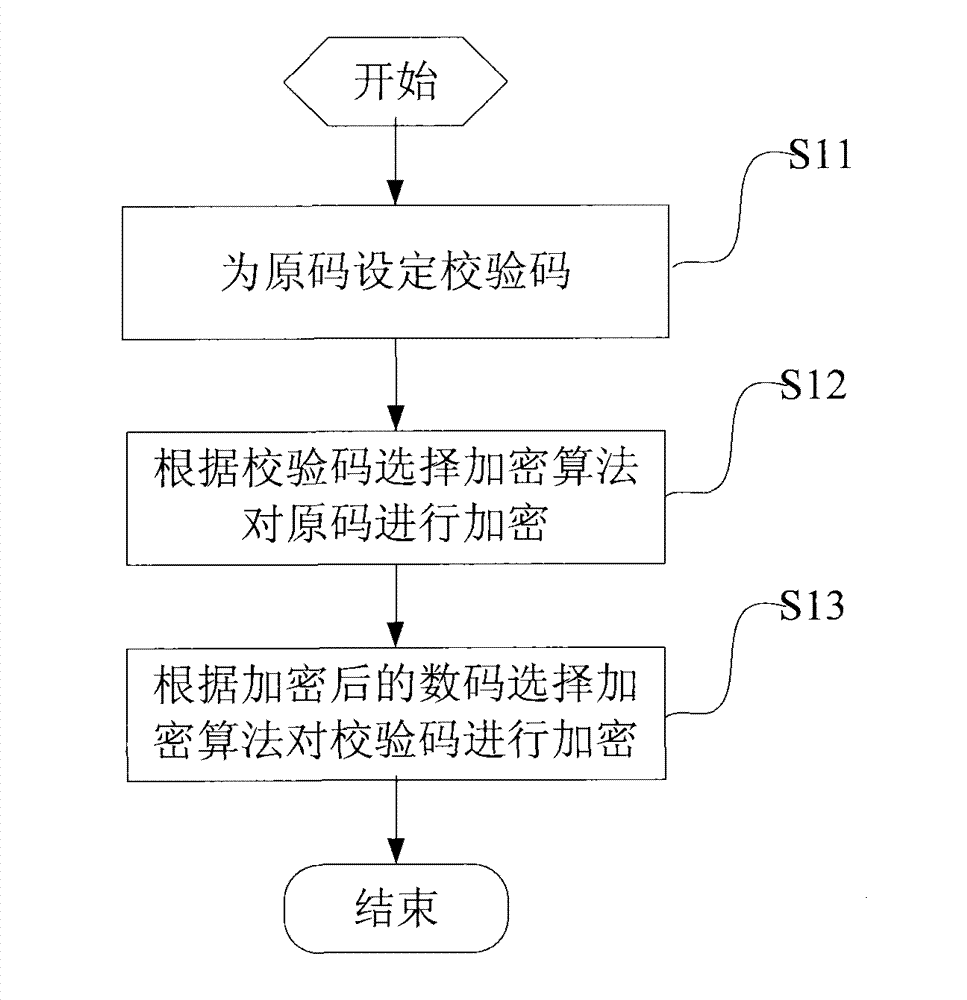
[0095] The process flow of the encryption method disclosed in Embodiment 1 of the present invention is as follows figure 2 shown, including:
[0096] Step S21, obtaining the N-digit original code, and setting a C-digit check code for the N-digit original code;
[0097] Step S22, according to the verification code, select the corresponding encryption algorithm from the pre-established encryption algorithm group to encrypt the N-bit original code;
[0098] Step S23: Select a corresponding encryption algorithm according to the encrypted N-digit number to encrypt the verification code.
[0099] Step S24, the encrypted N-digit number and the C-digit check code are formed into an N+C-digit number, and one of the N+C-digit numbers is arbitrarily selected as a selection code, and one of them is selected from a pre-established matrix group according to the selection code. The corresponding N+C-1 order matrix;
[0100] Step S25, multiplying the remaining N+C-1 digits in the above st...
Embodiment 2
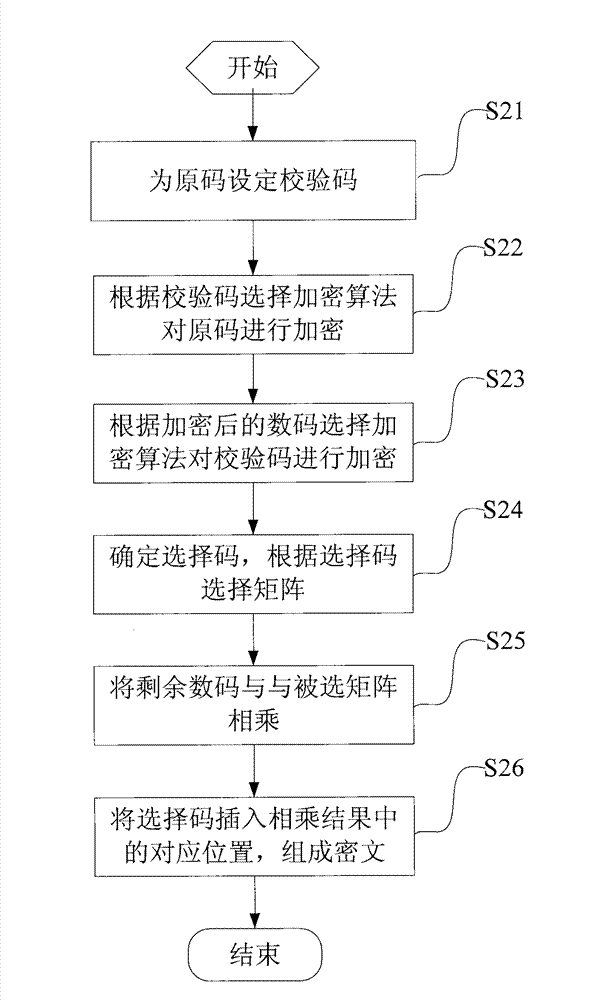
[0105] The process flow of the encryption method disclosed in this embodiment is as follows: image 3 shown, including:
[0106] Step S31, obtaining the N-digit original code, and setting a C-digit check code for the N-digit original code;
[0107] Step S32, select the a-th original code disorder algorithm from the pre-established original code disorder algorithm group according to the first a digits of the check code, and perform random sequence on the N-bit original code;
[0108] Step S33: Select the b-th symmetric encryption algorithm from the pre-established symmetric encryption algorithm group according to the remaining b digits of the check code, and perform a symmetric encryption algorithm on the original code after the disorder.
[0109] Here, the N-bit original code is encrypted twice by using the value of the check code, and different encryption methods are selected, and any number of encryption algorithms can be selected according to the actual situation to encryp...
Embodiment 3
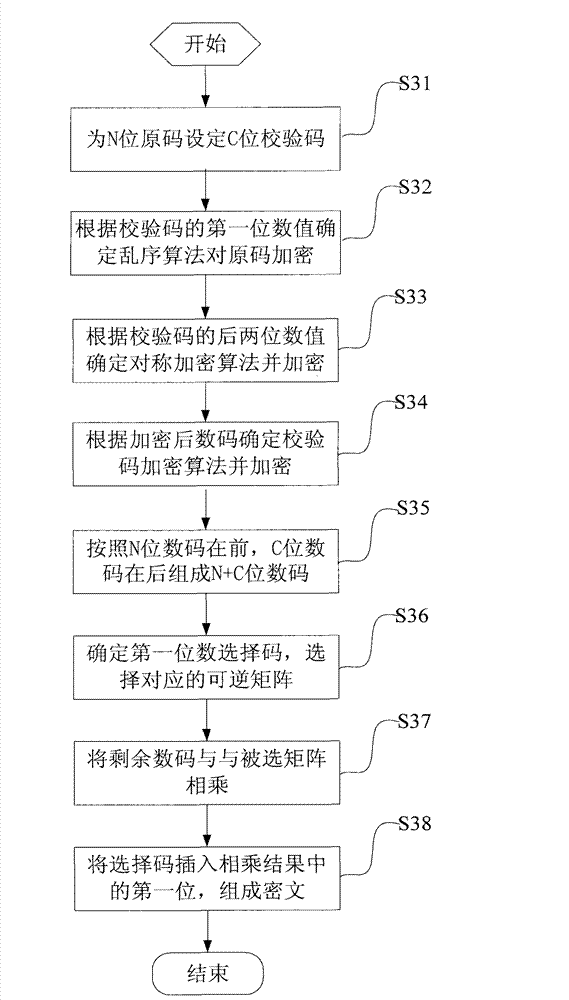
[0120] The specific implementation of each step in the further disclosed encryption method of this embodiment, first establishes an encryption algorithm group in advance, which includes: 10 sets of check code encryption algorithms, 10 sets of symmetric encryption algorithms and 10 sets of out-of-sequence algorithms, pre-set Values from 0 to 9 correspond to 10 sets of out-of-sequence algorithms L0 to L9, 20 to 29 correspond to 10 sets of symmetric encryption algorithms S0 to S9, and 0 to 9 correspond to 10 sets of checksum encryption algorithms C0 to C9.
[0121] The algorithm in this embodiment has been processed by modulo 10, that is, the step of adding modulo 10 after the algorithm, and converting the encrypted ciphertext into a decimal number. After verification, each set of symmetric encryption algorithms is mainly a combination of an out-of-sequence algorithm and three symmetric encryption algorithms. In this embodiment, the three encryption methods are hill encryption, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com