Detection method of broadcast storm and device thereof
A technology of broadcast storm and detection method, applied in digital transmission system, electrical components, error prevention and other directions, can solve the problem of inability to detect broadcast storm, improve classification efficiency, optimize classification effect, and avoid misjudgment of hash collision. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
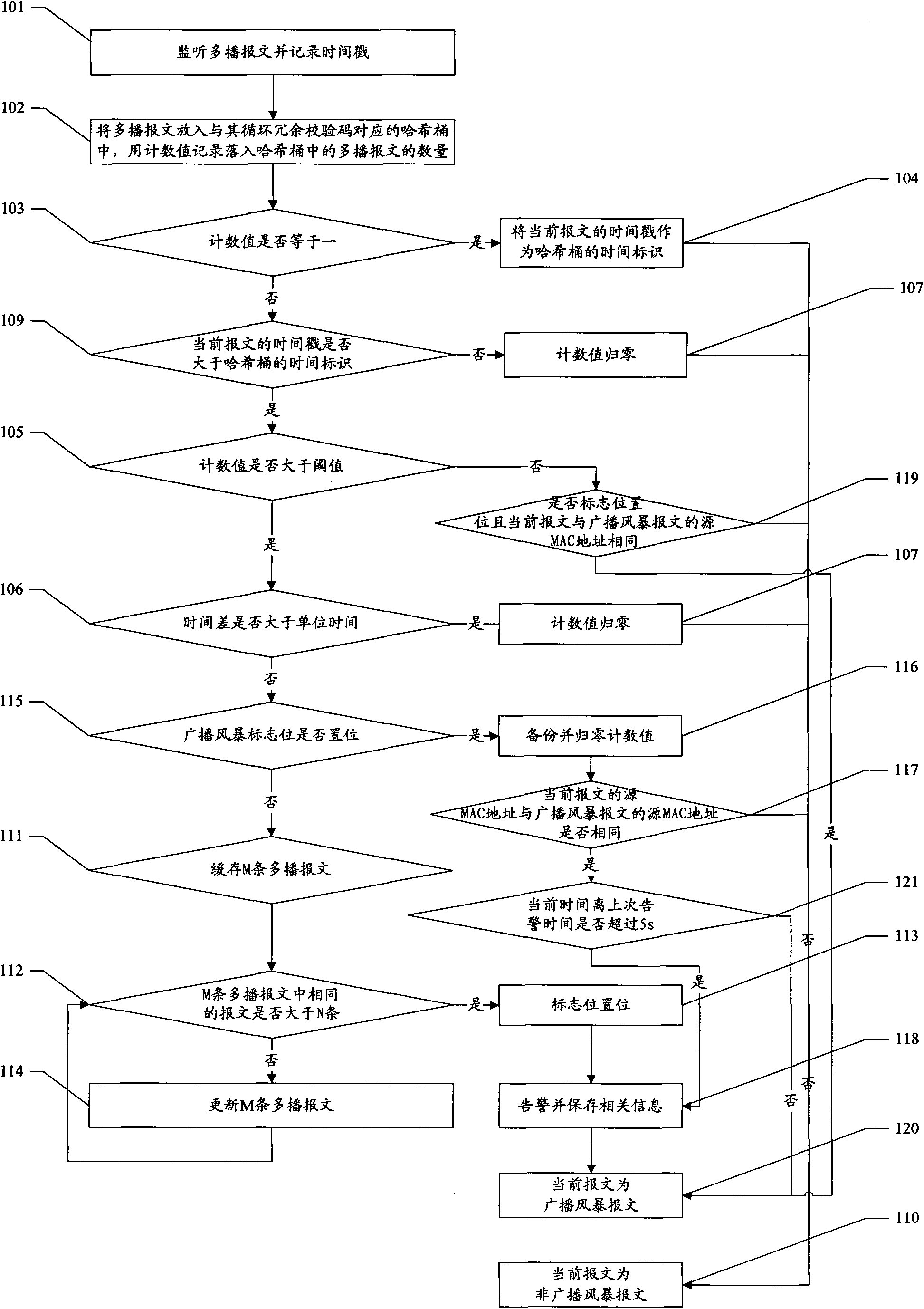
[0074] The detection method of broadcast storm of the present invention comprises the steps:
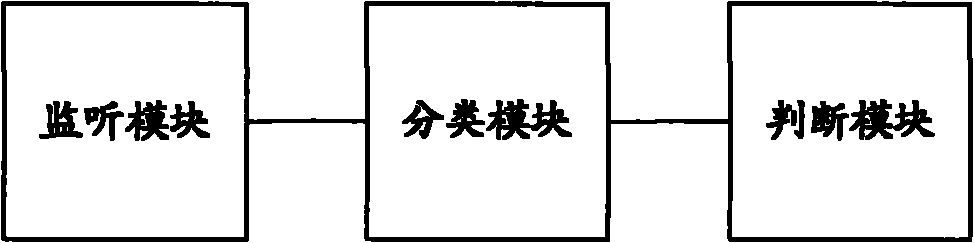
[0075] Listen to multicast messages;
[0076] Classify the monitored multicast packets according to the contents of the packets;
[0077] Calculate the number of each type of multicast packets monitored per unit time. When the threshold is exceeded, it is determined that a broadcast storm has occurred.
specific Embodiment approach
[0078] Messages can be divided into unicast messages and multicast messages according to the number of sending objects. The characteristic of multicast messages is that the highest byte and the lowest bit of the destination MAC address are one. Therefore, a specific implementation method for monitoring multicast messages is :
[0079] Listen to the message, and judge whether the highest byte and the lowest bit of the destination MAC address of the message are one, if so, determine that it is a multicast message,
[0080] Then analyze the contents of the messages judged as multicast messages, classify those with the same content into one category, and calculate the number of multicast messages of each type monitored per unit time. If it exceeds the threshold, it is determined that a broadcast storm has occurred. If the highest byte and lowest bit of the destination MAC address of the message are not one, it can be judged as a non-broadcast storm message. The unit time and thre...
Embodiment 2
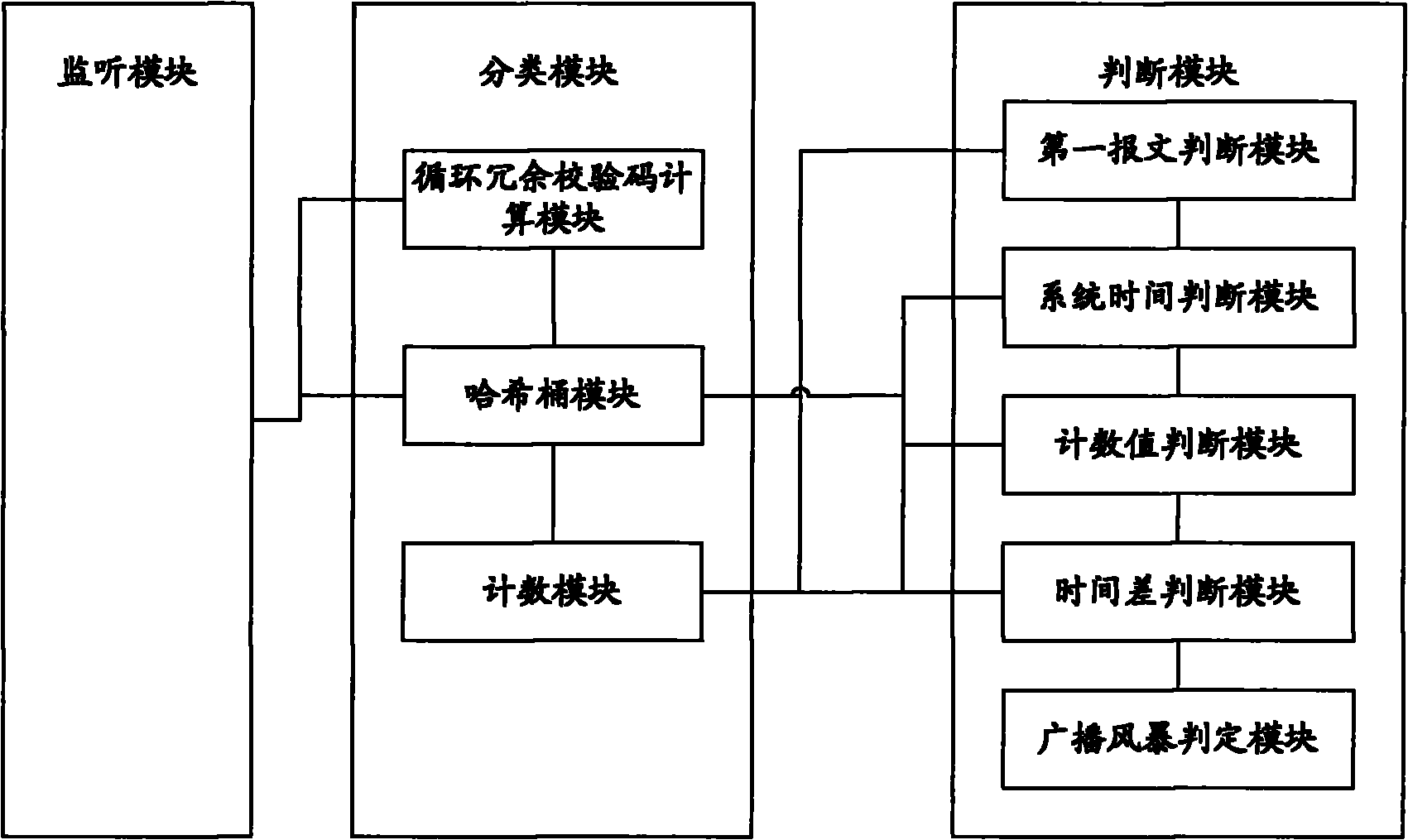
[0083] When classifying multicast messages, if the method of sequentially analyzing the message content of each multicast message is adopted, the efficiency is very low. Therefore, in order to improve efficiency, this embodiment adopts hash algorithm to classify multicast messages .
[0084] Firstly, a certain hash algorithm is used to hash the content of the multicast message, and the multicast message is put into the corresponding hash bucket according to the hash value. The hash value is evenly distributed, so the messages will be evenly placed in the hash bucket, and there will be no situation where the number of messages accumulated in a certain hash bucket exceeds the threshold per unit time. If a certain hash bucket within a unit time If the number of packets accumulated in the bucket exceeds the threshold, it can be determined that it is caused by a broadcast storm, that is, a broadcast storm has occurred. Therefore, choosing an appropriate hash algorithm becomes the k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com