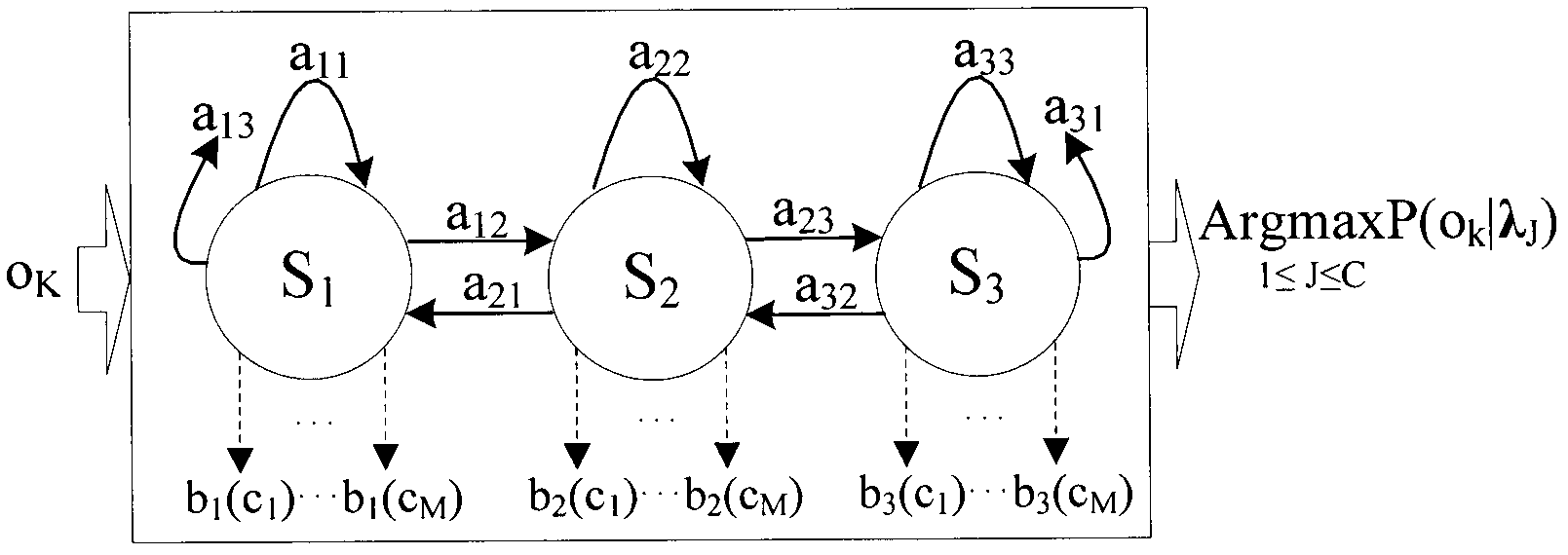
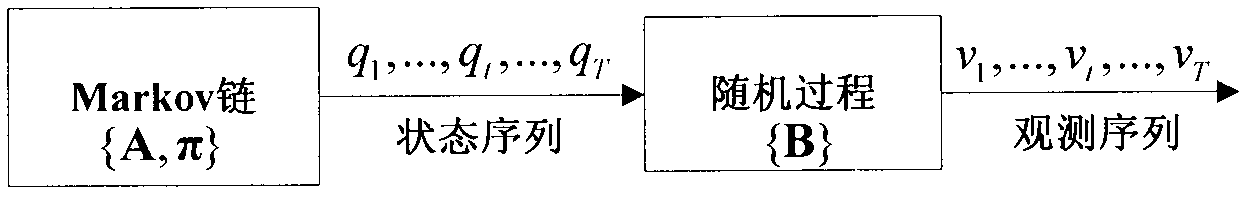
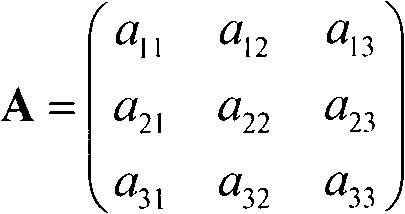Hidden Markov model based method for detecting assembler instruction level vulnerability
A technology of hidden Markov and assembly instructions, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0093] The technical solutions of the present invention will be described in detail below in conjunction with specific embodiments.
[0094] In this embodiment, the method of the present invention is used to perform vulnerability detection on 30 executable programs whose size is between 50KB and 100KB. Proceed as follows:
[0095] Step 1. Use 30 executable programs with a size of about 10KB to construct a vulnerability instruction library. The vulnerability instruction library contains 3 vulnerabilities, specifically:
[0096] Step 1.1: Disassemble 10 executable programs containing a software vulnerability using a static disassembly analysis tool to obtain a function structure diagram of all functions in the executable program; each function structure diagram is called an assembly instruction fragment.
[0097] Each function graph corresponds to a function, and each function graph includes but not limited to the following information: function name, function parameters, return ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com