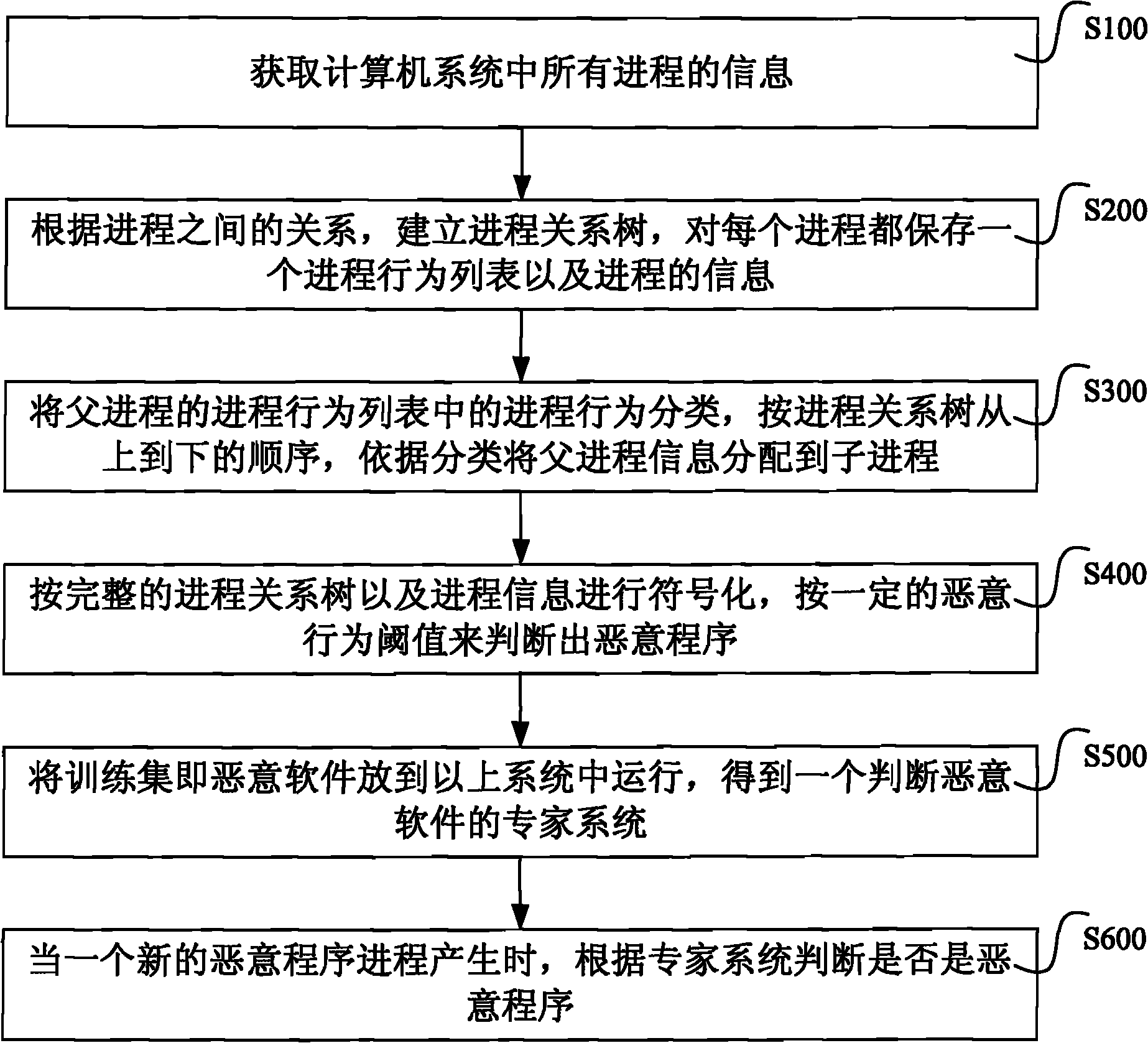
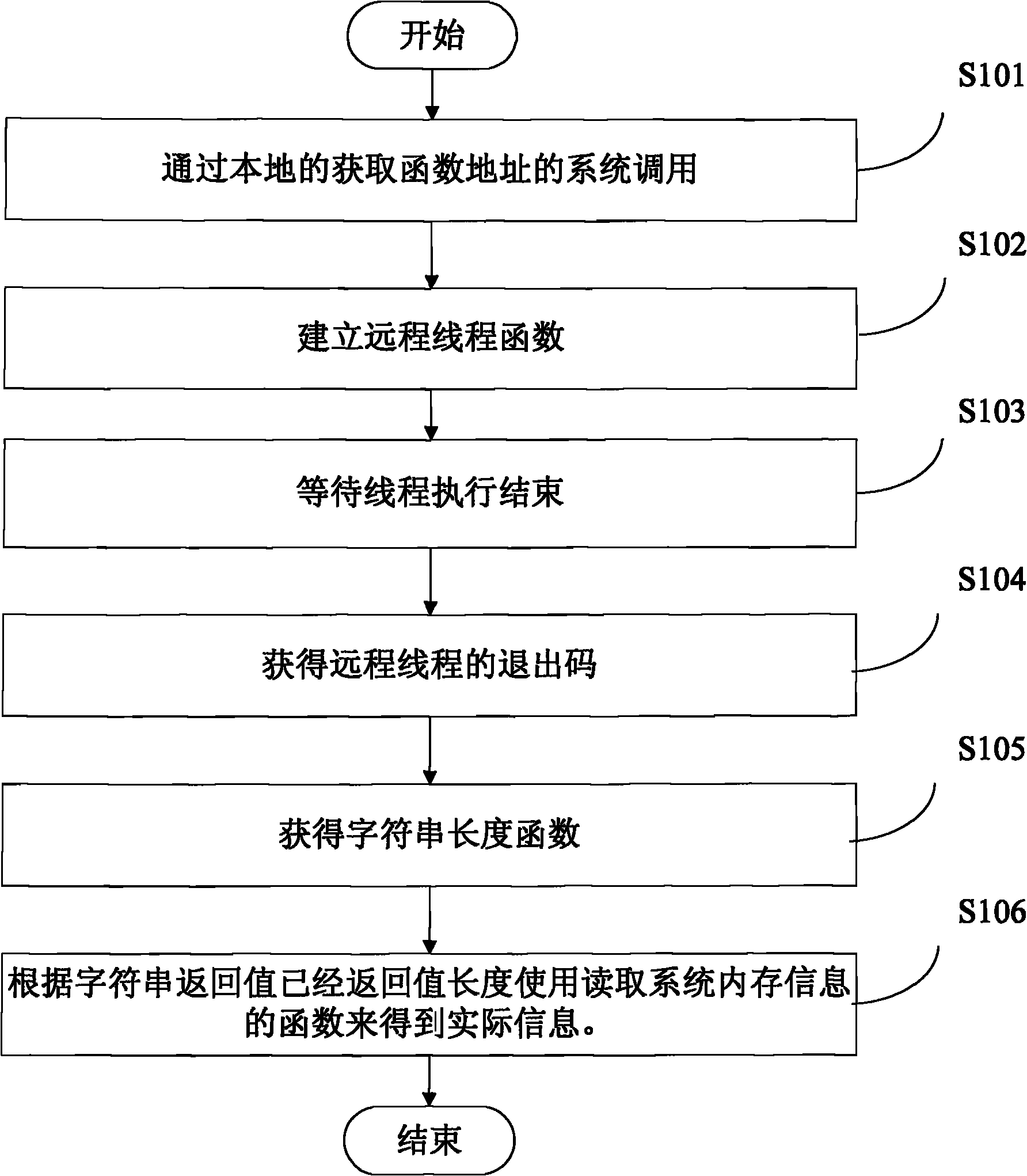
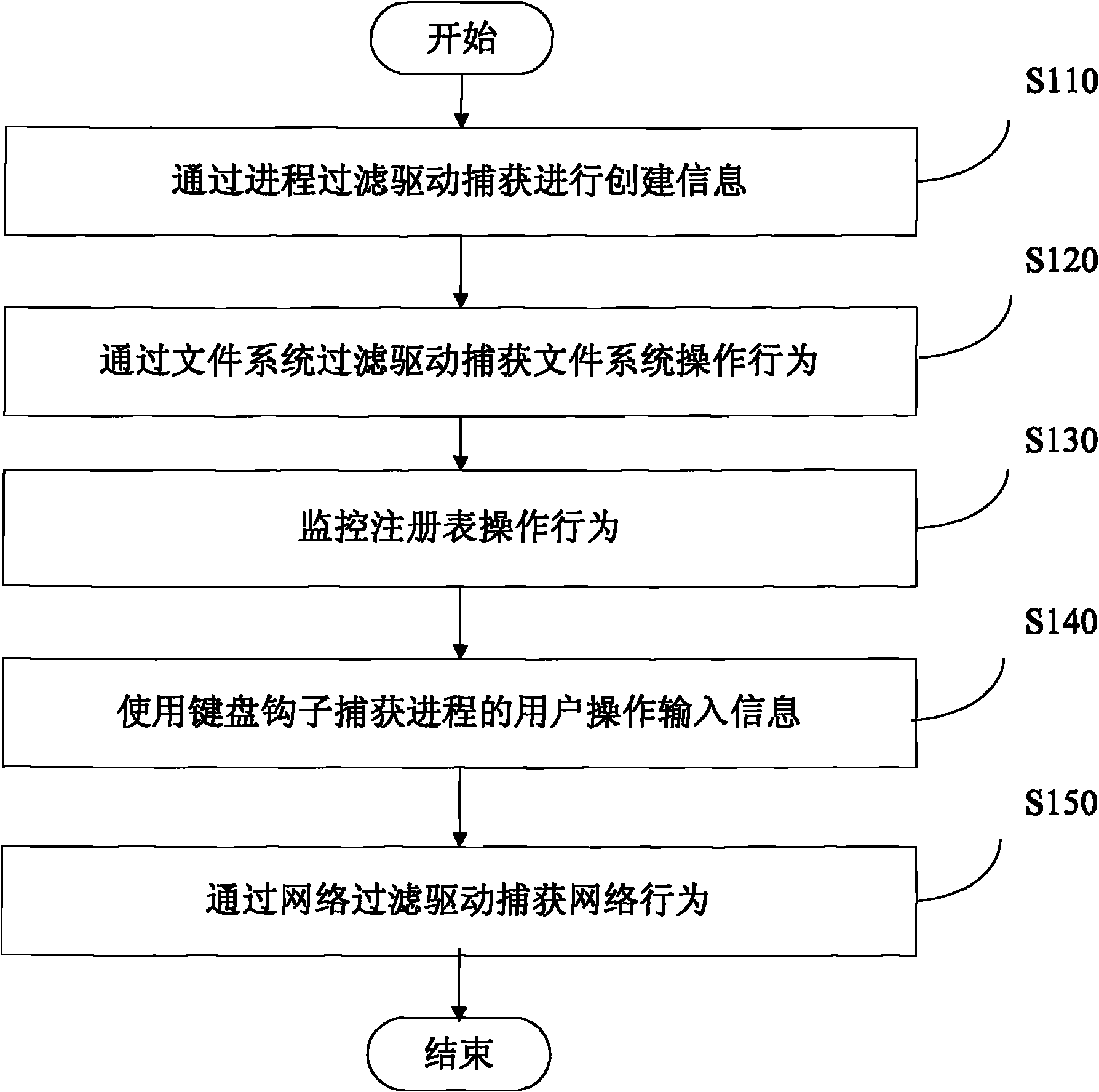
Method and system for identifying malicious program
A malicious program and new program technology, applied in the field of information security, can solve problems such as dynamic analysis failure, strategy interference, inaccuracy, etc., and achieve the effect of improving accuracy, reducing false alarm rate, and high false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0111] It is used in the network shooting range experiment platform of the Network Key Laboratory of the Institute of Computing Technology, Chinese Academy of Sciences.
[0112] The application scenarios of the process association and process behavior analysis method proposed in this patent include, antivirus software based on dynamic analysis technology, including inside and outside the system; host-based intrusion detection system; network-based intrusion detection system; firewall; network experiment platform.
[0113] Figure 5 It is the embodiment of the present invention on the network experiment platform system. Compared with the traditional feature-based mode of anti-malware, process correlation and process behavior analysis can be run on a distributed system, and malicious behavior thresholds and corresponding values can be manually defined. It has the ability to discover unknown attacks, vulnerabilities, malware and other comprehensive detection methods. .
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com