Integrated identification network personal communication mobile management method based on double-proxy
A mobile management and identification network technology, which is applied in the field of personal communication mobile management based on a dual-agent integrated identification network, can solve the problems of poor compatibility between services, difficult control and management, poor scalability, etc., to ensure simplicity and effectiveness. , Low transmission distance and transmission delay, the effect of ensuring scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
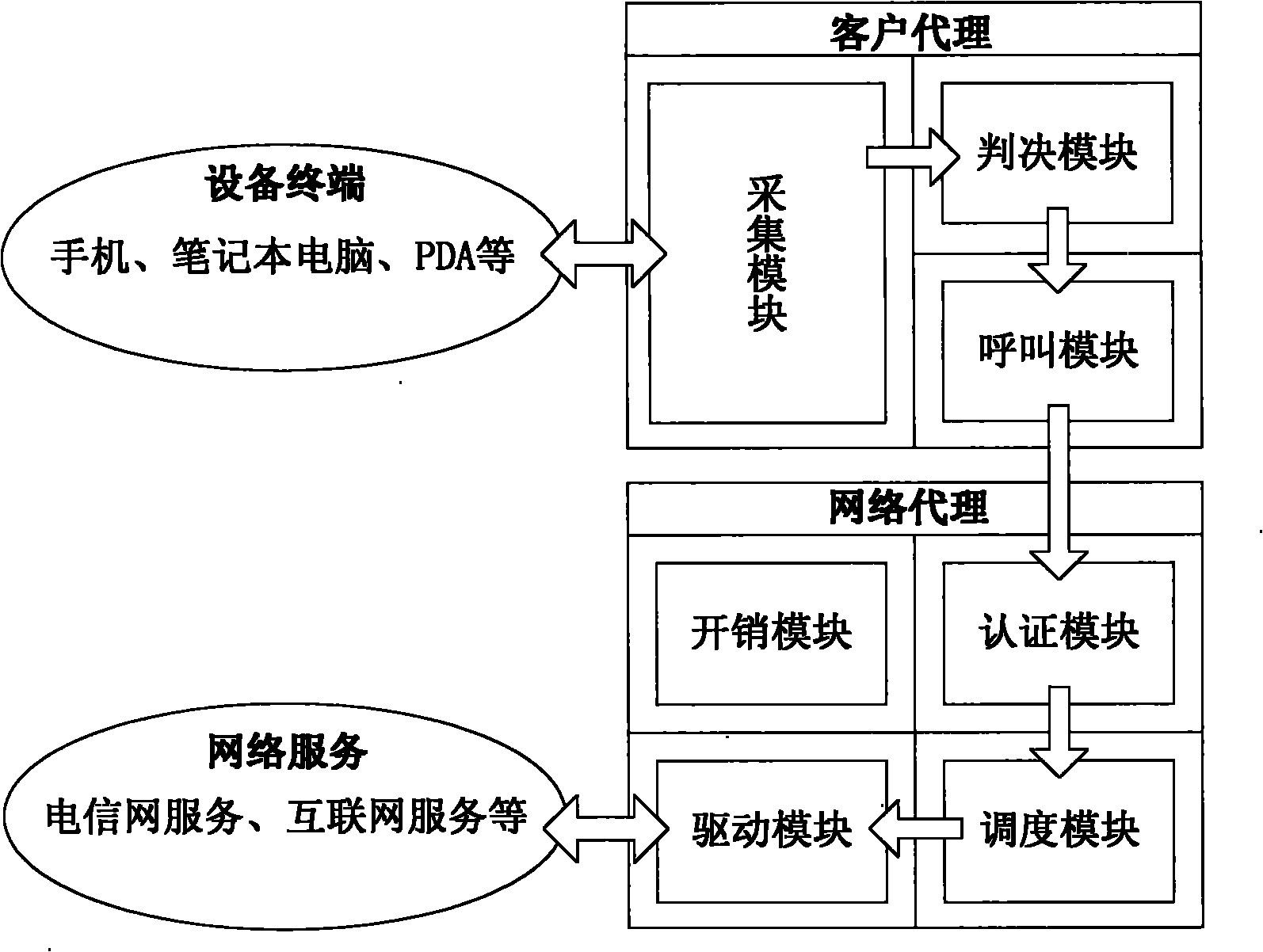
Image
Examples
Embodiment 1
[0049] Embodiment 1: Establishment of two user service communication links
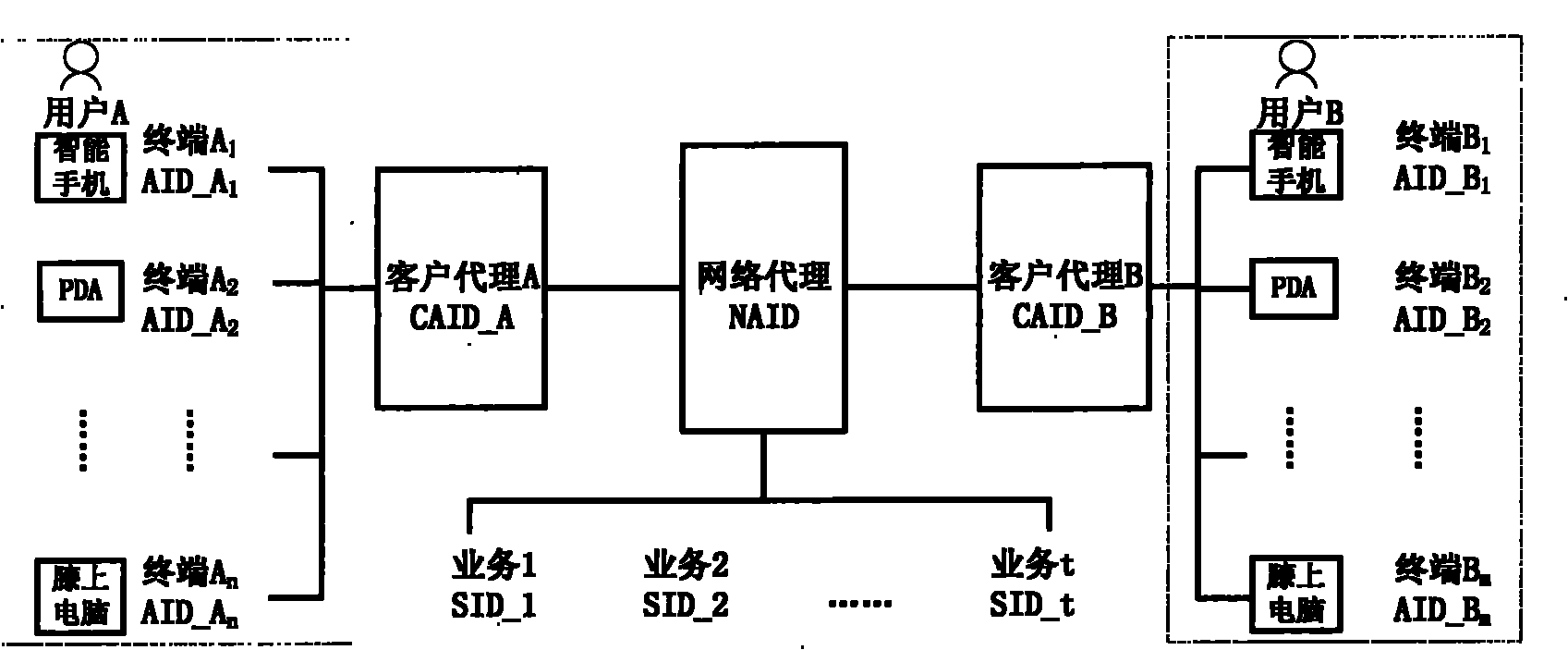
[0050] Establishing a user personalized service connection between two user terminal devices is called the establishment of a service communication link. The establishment of two user service communication links consists of 5 steps, which will be combined below Figure 4 Instructions are given step by step:
[0051] Step 1: User A's customer agent CAID_A selects a device terminal for its business (such as A 1 ) to initialize the communication process, and terminal A 1 Access ID AID_A 1 Sent to user B's customer agent CAID_B.
[0052] Step 2: After user B receives the connection request from user A, CAID_B selects a device terminal for user B (such as B 1 ) to respond; CAID_B will obtain the network agent ID NAID from the network, and then terminal A 1 and B 1 Access ID AID_A 1 and AID_B 1 Sent to the web proxy.
[0053] Step 3: CAID_B connects Terminal B 1 Access ID AID_B 1 and the selecte...
Embodiment 2
[0056] Embodiment 2: Service switching in an integrated identification network environment
[0057] In the communication process of the integrated identification network, the conversion of the same service between different terminals is called service switching. In this embodiment, the service switching in the communication process is divided into 6 steps, which will be combined below Figure 5 Give instructions:
[0058] In this embodiment, we assume that the steps in Embodiment 1 have been followed, and the terminal A is connected through the network proxy 1 and terminal B 1 A service communication link CID_1 is established for SID_1. Now user A wants to transfer SID_1 from terminal A 1 switch to terminal A 2 , where A 2 belongs to user A and is different from terminal A 1 another terminal.
[0059] Step 1: User A submits a switching request to CAID_A.
[0060] Step 2: CAID_A detects terminal A 1 and A 2 According to the working conditions and communication capabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com