Binary image fragile watermark embedding and extraction method based on topology structure
A binary image and topology technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of being easily tampered, unrecognizable, troublesome, etc., and achieve the effect of ensuring visual hiding effect and fast hiding effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
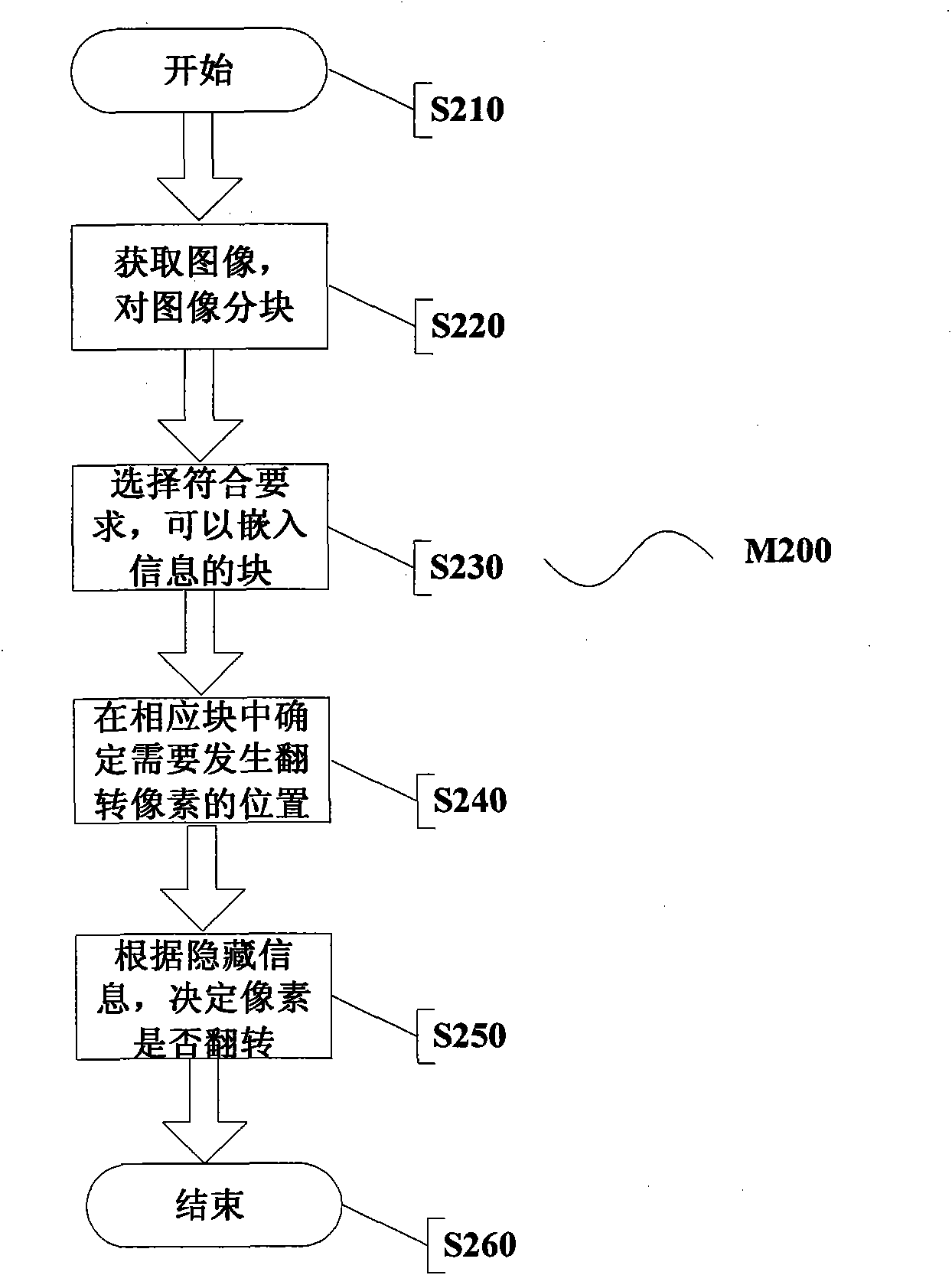
[0078] figure 2 A flow chart of an M200 embodiment for performing fragile watermark embedding processing on binary images according to the method of the present invention is given.
[0079] Such as figure 2 As shown, the method M200 starts at step S210.
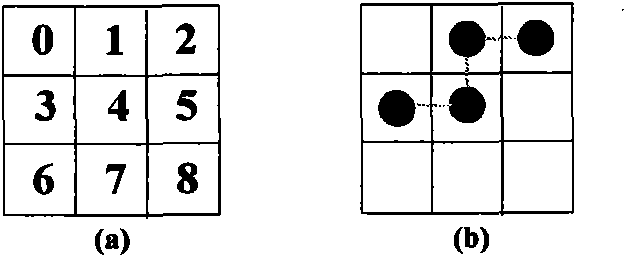
[0080] In step S220, a basic file in bitmap format (BMP) is obtained from files in different formats of the binary image. At this time, each pixel has one bit to represent its black and white information. Next, we divide the image into the spatial domain and divide it into small blocks of equal size. Note that the small block does not have to be a square, it can be of size n 1 ×n 2 , 21 , n 2 <10 rectangles. We won't have to deal with the excess on the sides. Those skilled in the art will recognize that the size of the tiles is readily applicable to more than 3x3 tiles.
[0081] Then in step S230, we select a part from the several small blocks of the image divided above as blocks that meet the requirements and can e...
Embodiment 2
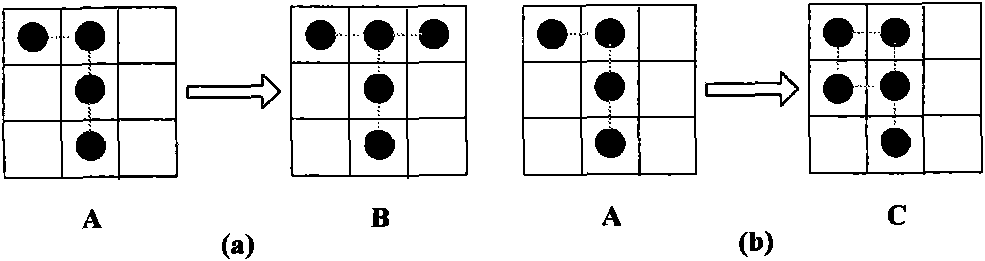
[0091] Pic 4-1 Algorithm 1 for generating hidden chains that can be embedded into information blocks according to the method of the present invention is given, and for 3×3 blocks, an example of block hidden chains generated according to Algorithm 1 is given. From image 3 In the example of , we conclude that flipping pixels with the same topology (one-stroke property) has a good visual hiding effect. According to Euler's basic research results on one-stroke painting, in fact, we only need to pay attention to the parity of the degree of vertices, and investigate whether the addition of vertices still conforms to the nature of one-stroke painting. Considering the need to extract information, the blocks after hiding information must still be in the set of embedded information blocks, so we can derive a block change chain of hidden information from a block that can embed information. In order to generate a set of blocks that can embed information, a generation chain can be deri...
Embodiment 3
[0093] Figure 5-1 Algorithm 2 of the embeddable information block set generated according to the method of the present invention is given, and an example of the embeddable information block set generated according to Algorithm 2 is given for a 3×3 block.
[0094] According to method M500, at first in step S510 adopt depth-first or breadth-first search (basic algorithm in graph theory) to generate a weight Those satisfying the properties i, ii, and iii above can be embedded in the set S of information blocks; then in step S520, select a block in S, and generate a chain of embeddable information blocks according to Algorithm 1. If the generated block is re- Appears to stop. Finally, all embeddable information block chains are merged to obtain the final set of embeddable information blocks. In order to make the algorithm flow easy to understand, here is an example, see Figure 5-2 . Thus we get a collection of blocks that can embed information that meets the requirements: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com