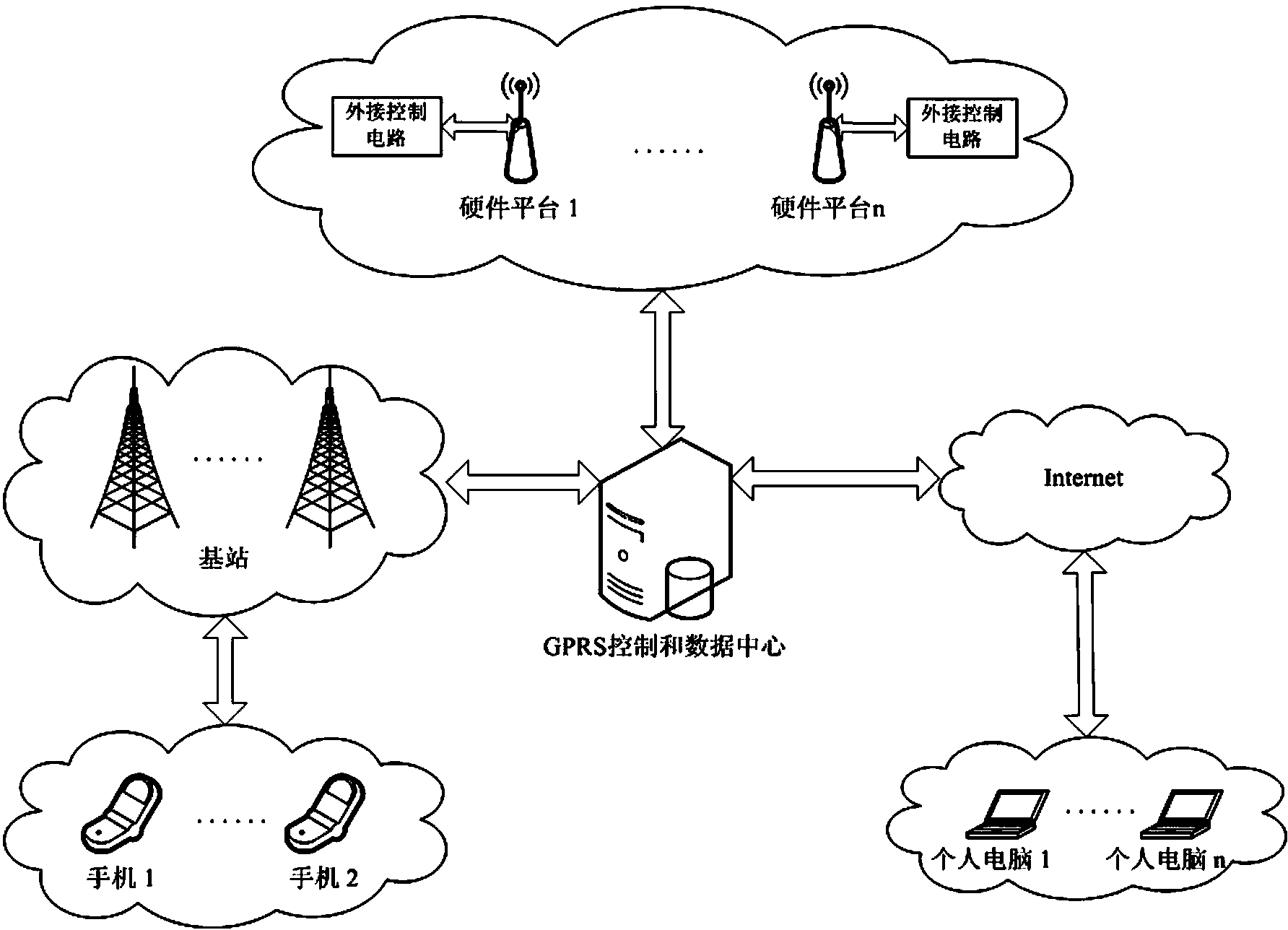
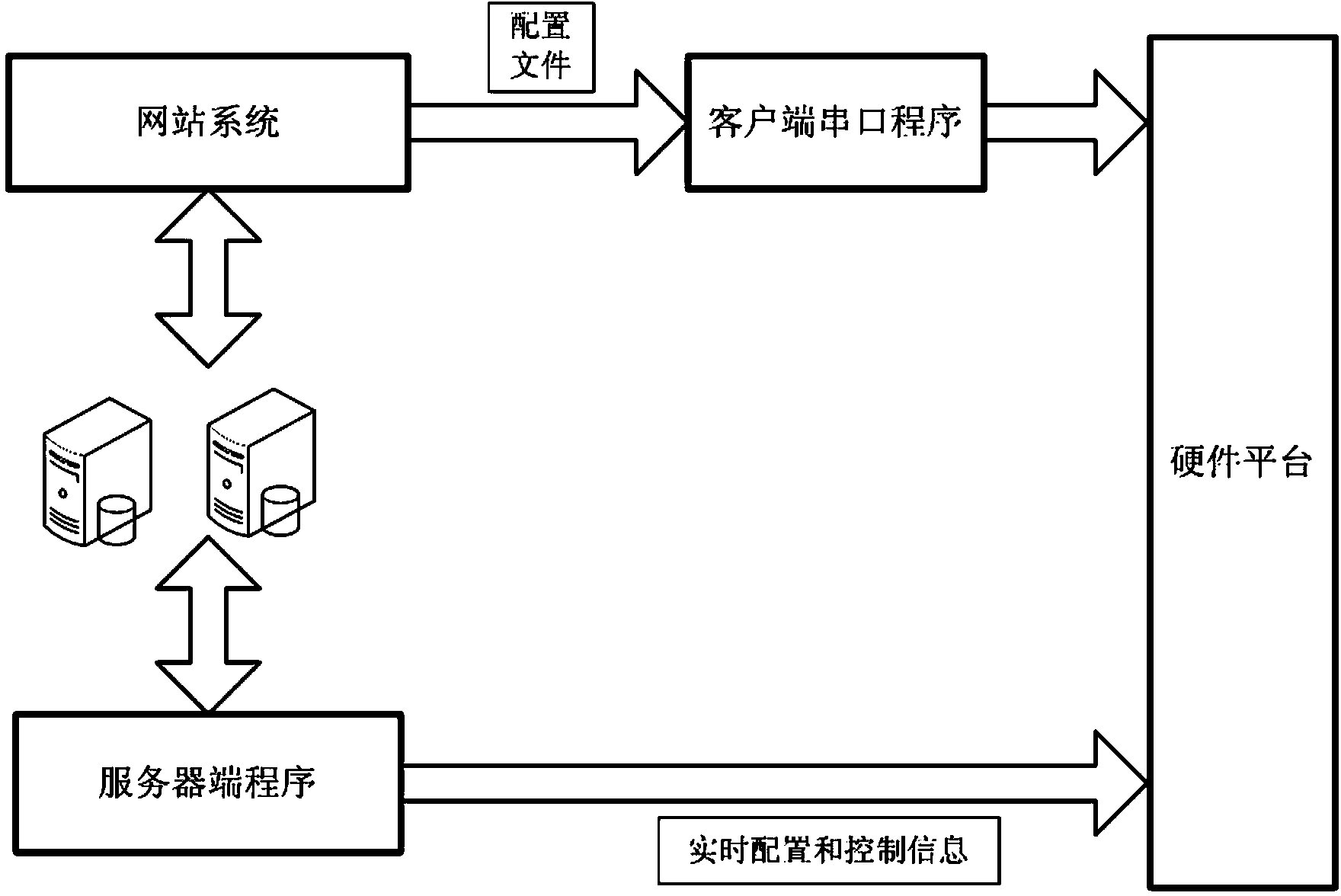
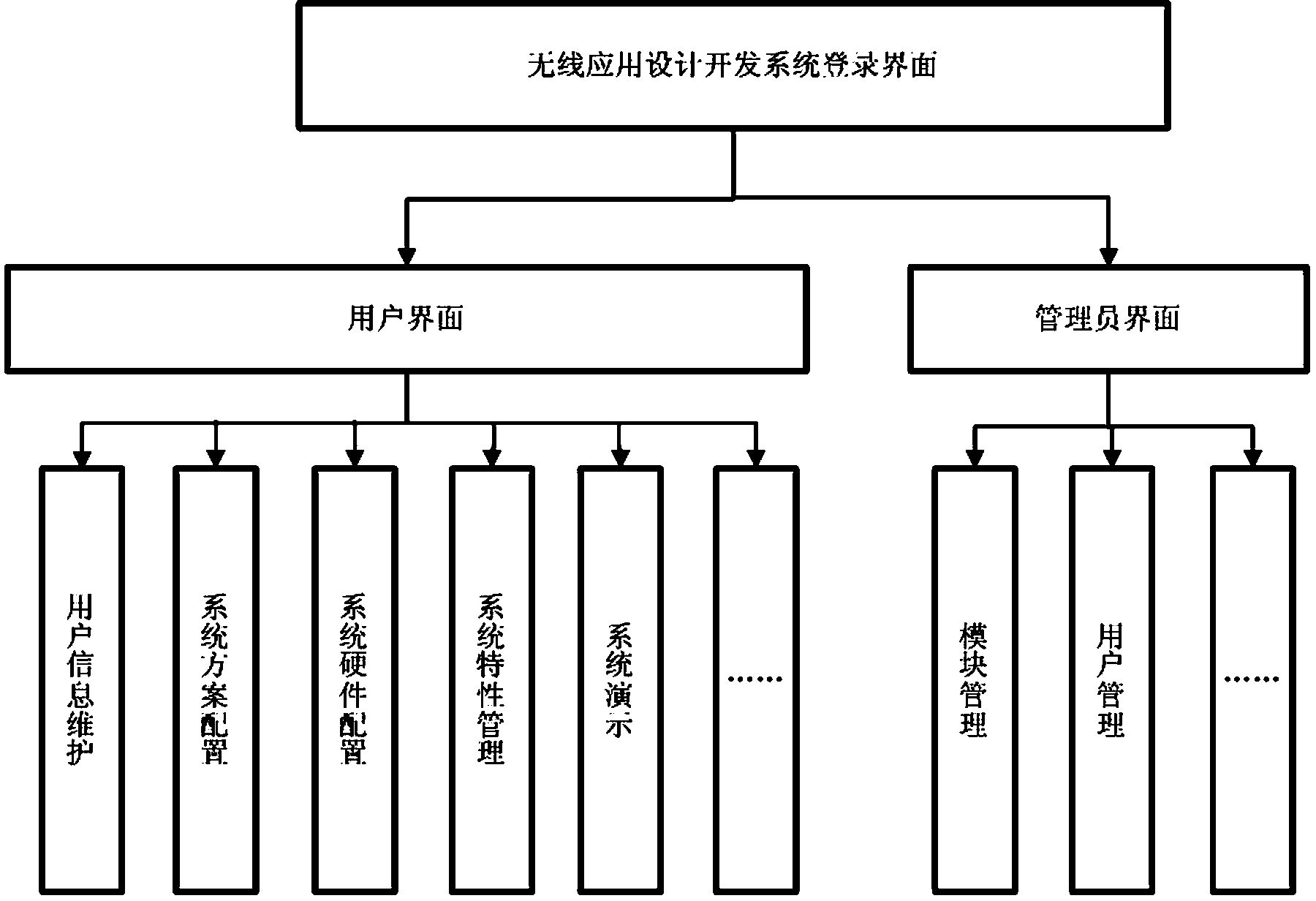
Configurable wireless application design and development method
A wireless, configuration file technology, applied in electrical components, transmission systems, etc., can solve problems such as cost, loss of human and material resources, and increase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0092] Application of the present invention realizes family anti-theft.
[0093] Peripheral modules required: monitoring the thief is ready to enter the module, monitoring the thief has entered the module, voice module, camera module.
[0094] Realized function: When the thief is about to enter the room, he calls the owner, and the owner controls the voice module to work through the mobile phone, and plays the preset warning audio. You can also choose to call the police at this time. After the thief enters the room, he calls the owner, and the owner controls the camera module to take pictures through the mobile phone. You can also choose to call the police at this time.
[0095] 1. Create a plan
[0096] Open the website system and enter the program setting interface to create a program and give a brief description. For example, the program name can be written as home security, and the description information can be written as home security monitoring using a configurable w...
example 2
[0108] The invention is applied to realize anti-theft of automobiles.
[0109] Peripheral modules required: monitor the thief is ready to enter the module, monitor the thief has entered the module, voice module, camera module, control the car flameout module.
[0110] Realized function: When the thief tries to steal, call the owner's mobile phone, the owner controls the voice module through the mobile phone, and plays the preset alarm audio. After the hardware platform dials the owner's number, the owner can call the police.
[0111] Create a plan
[0112] The process of creating a scheme is the same as Example 1.
[0113] 2. Hardware configuration
[0114] Due to the similarity with Example 1, the settings for Solution 1 can be directly borrowed, and a button control input button 3 is added to enable the control of the car flameout module.
[0115] 3. Download configuration information
[0116] same example one
[0117] 4. Install the hardware system
[0118] same exam...
example 3
[0124] The monitoring of river sewage is realized by applying the invention.
[0125]Realized function: Use relevant water pattern monitoring sensor modules (such as water temperature, PH value, phosphorus content, etc.) to monitor the sewage status of the river for 24 hours, and collect river water temperature data in real time. When the data is abnormal, the data can be reported and the preset mobile phone can be called at the same time. Users can view the historical collection data information through the computer. At the same time, multiple points can be set for monitoring the entire river. Solve the difficult problem of obtaining evidence for river sewage.
[0126] 1. Create a plan
[0127] The process of creating a scheme is the same as Example 1.
[0128] 2.1 Configure hardware
[0129] For this program, it takes 24 hours to collect. Assume that the program needs to collect information once an hour. Then you should set the trigger time setting in the hardware co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com