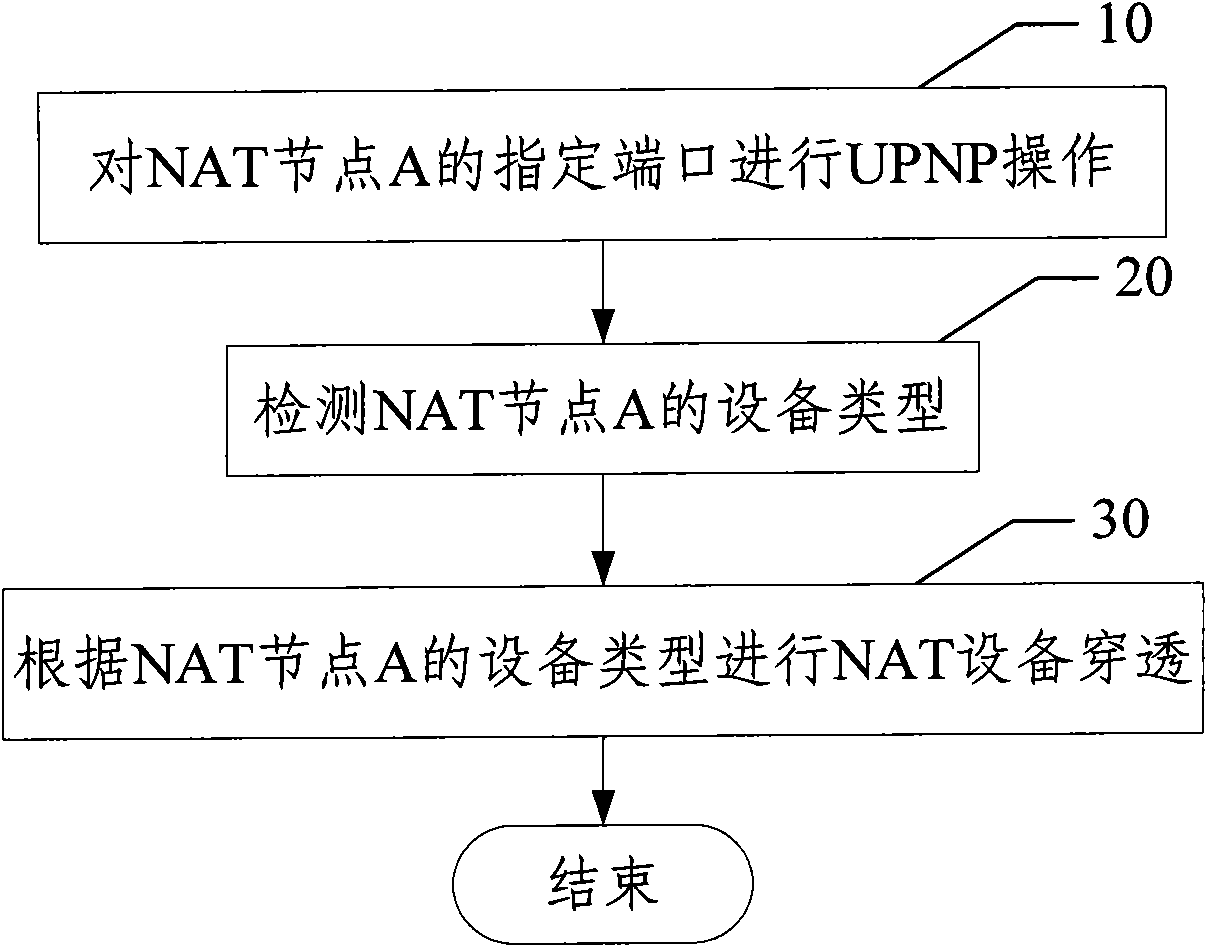
Method for penetrating NAT (Network Address Translation) equipment
A kind of equipment and equipment type technology, applied in the field of Internet communication, can solve the problems that nodes cannot be interconnected, reduce user network experience, and unfavorable enterprise internal user network applications, etc., to reduce penetration costs, improve network experience, and meet real-time network application requirements Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
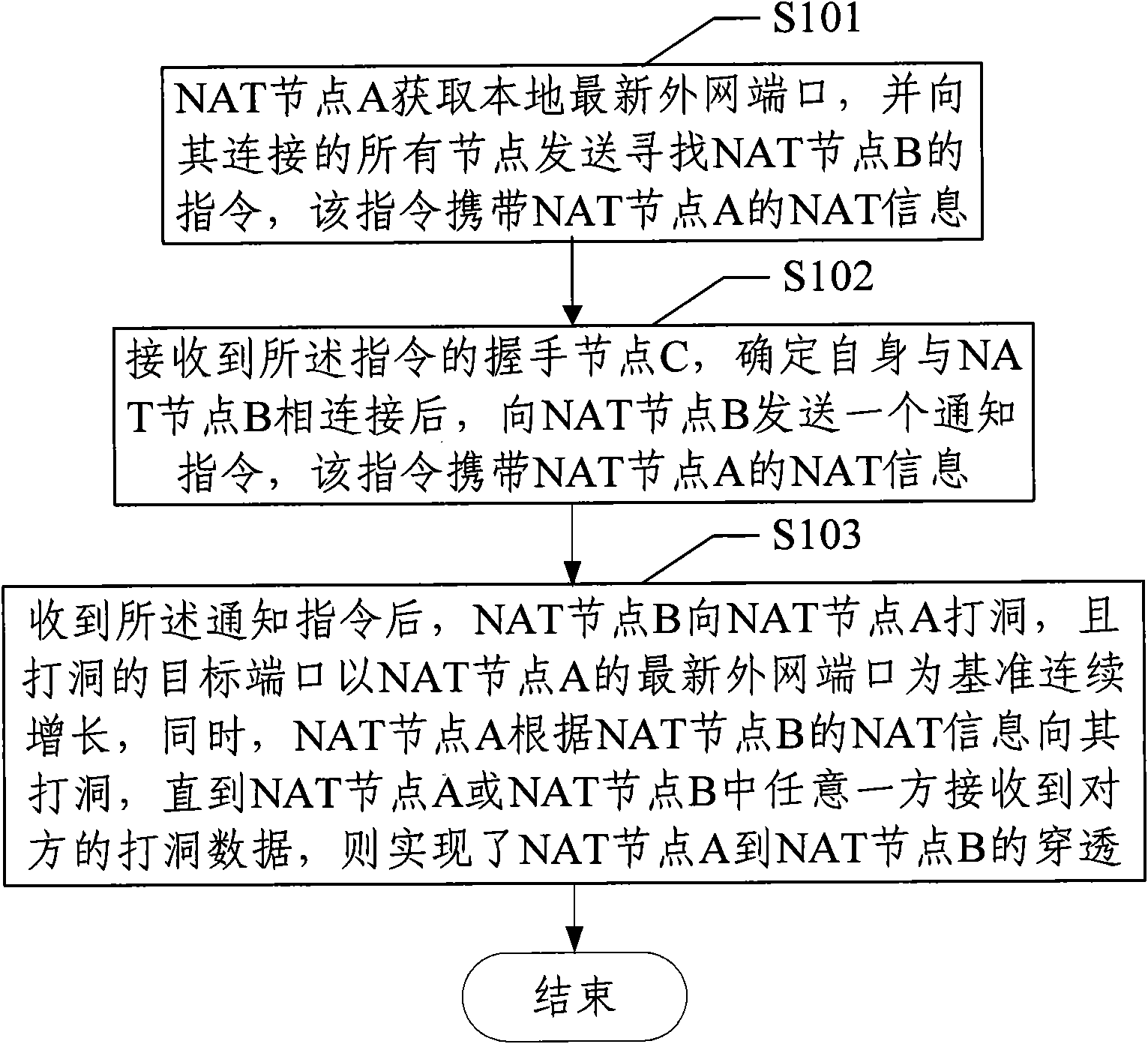
[0065] Example 1: Penetration between NAT2 and NAT1.1 or NAT1.2.
[0066] figure 2 It is the method flowchart of Embodiment 1 of performing NAT device penetration according to the device type of NAT node A in the method of the present invention, as figure 2 As shown, the type of NAT node A is NAT1.1 or NAT1.2, the type of NAT node B is NAT2, and the NAT information of NAT node B is known to NAT node A. The method includes:
[0067] Step S101: NAT node A obtains the latest local external network port, and sends an instruction to find NAT node B to all nodes connected to it, and the instruction carries the NAT information of NAT node A;
[0068] The NAT information includes: NAT type, local IP and port, external network IP and port.
[0069] Step S102: After receiving the instruction, the handshaking node C determines that it is connected to the NAT node B, and then sends a notification instruction to the NAT node B, the instruction carrying the NAT information of the NAT no...
Embodiment 2
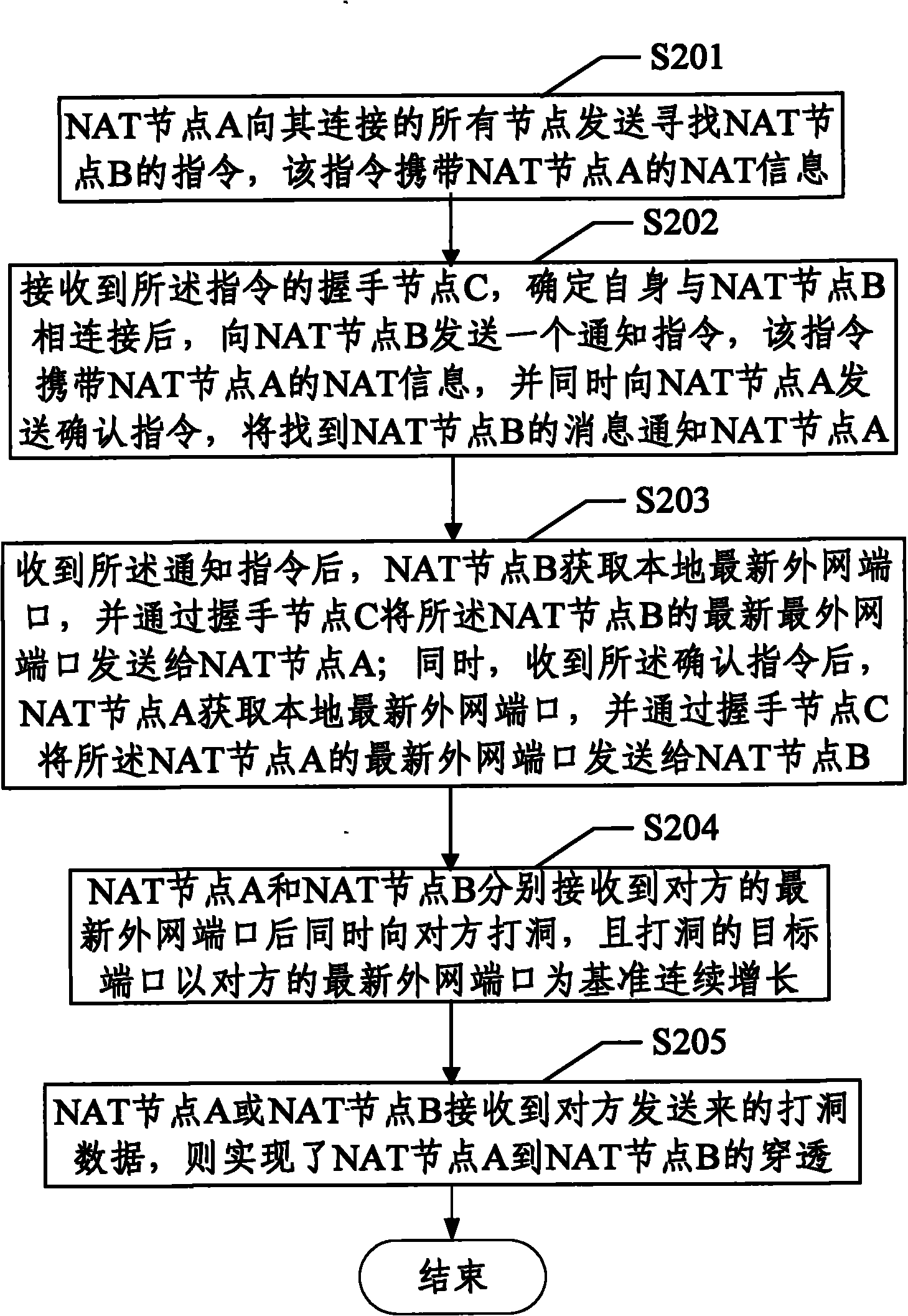
[0075] Example 2: Penetration between NAT1.2 and NAT1.1 or NAT1.2.
[0076] image 3 It is the method flowchart of embodiment 2 of performing NAT device penetration according to the device type of NAT node A in the method of the present invention, as image 3 As shown, the type of NAT node A is NAT1.2, the type of NAT node B is NAT1.1 or NAT1.2, NAT node A knows the NAT information of NAT node B, and the method includes:
[0077] Step S201: NAT node A sends an instruction to find NAT node B to all nodes connected to it, and the instruction carries NAT information of NAT node A;
[0078] The NAT information includes: NAT type, local IP and port, external network IP and port.
[0079] Step S202: After receiving the instruction, the handshake node C determines that it is connected to the NAT node B, and then sends a notification instruction to the NAT node B, which carries the NAT information of the NAT node A, and sends a confirmation to the NAT node A at the same time Instru...
Embodiment 3
[0086] Example 3: Penetration between NAT1.1 and NAT1.1.
[0087] Figure 4 It is the method flow chart of embodiment 3 of performing NAT device penetration according to the device type of NAT node A in the method of the present invention, as Figure 4 As shown, the types of NAT node A and NAT node B are both NAT1.1, and NAT node A knows the NAT information of NAT node B. The method includes:
[0088] Step S301: NAT node A sends an instruction to find NAT node B to all nodes connected to it, and the instruction carries NAT information of NAT node A;
[0089] The NAT information includes: NAT type, local IP and port, external network IP and port.
[0090] Step S302: After receiving the instruction, the handshaking node C determines that it is connected to the NAT node B, and then sends a notification instruction to the NAT node B, which carries the NAT information of the NAT node A, and sends a confirmation to the NAT node A at the same time Instruction, will find the messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com