Method and system for flow identification of point to point (P2P) protocol
A traffic identification and protocol technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of server address and port changes, which are not very effective, and achieve the effect of good scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
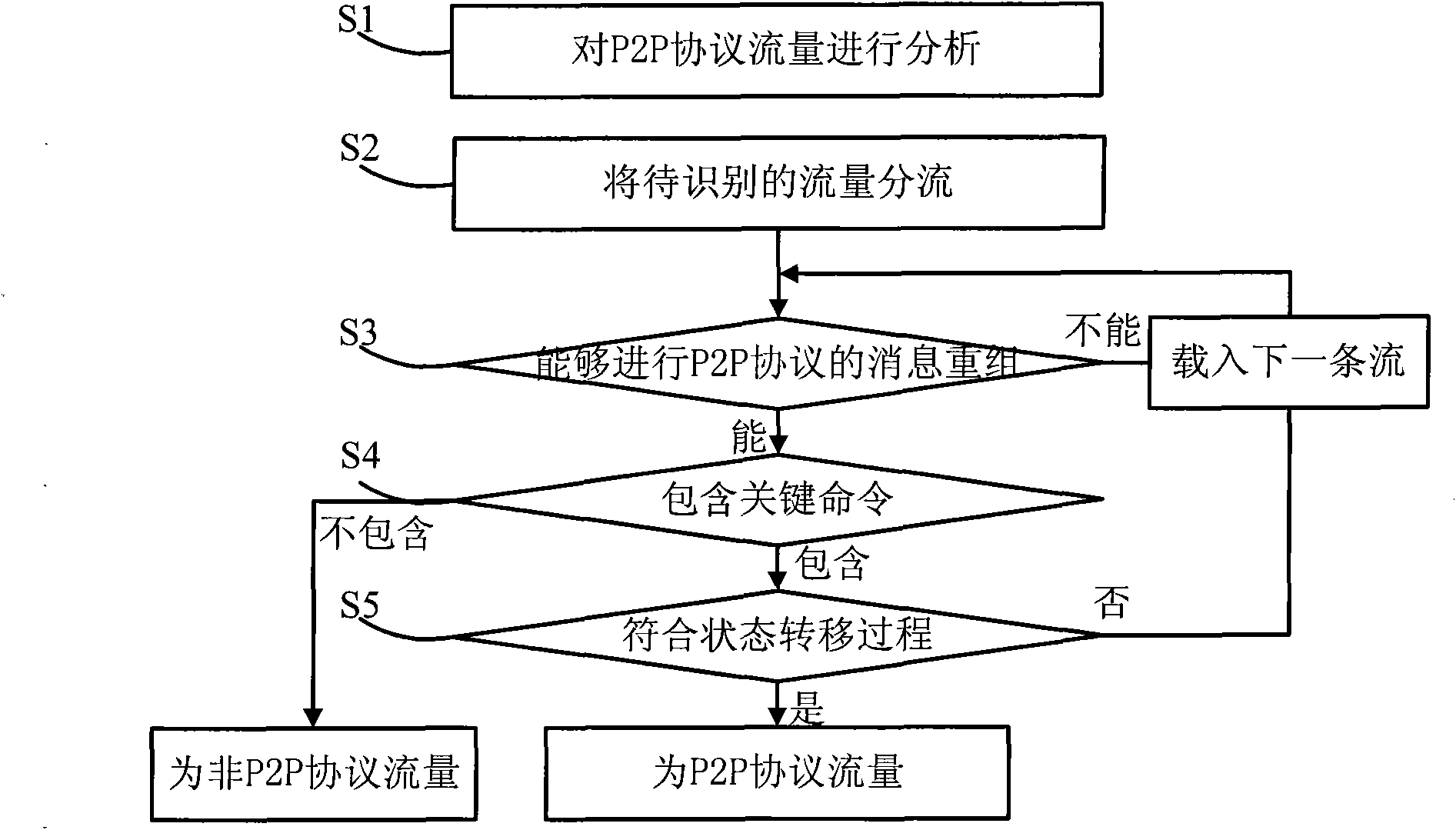
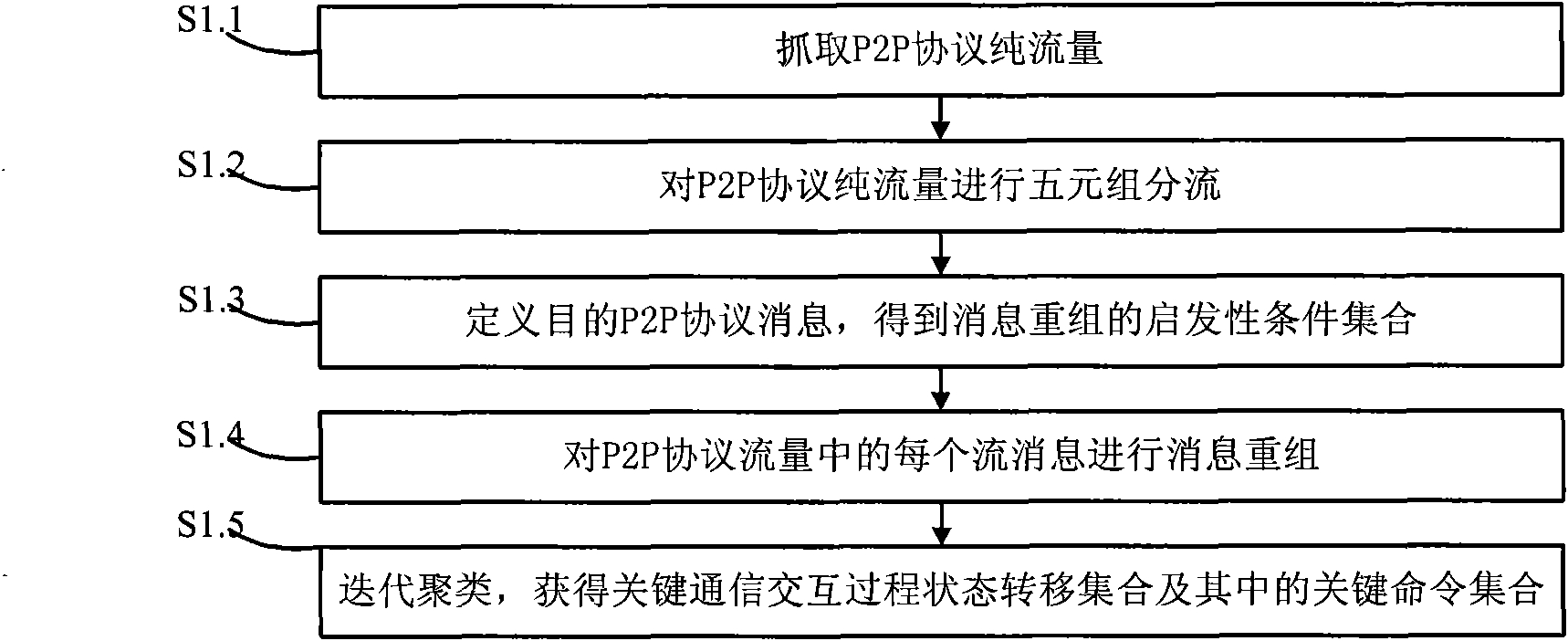
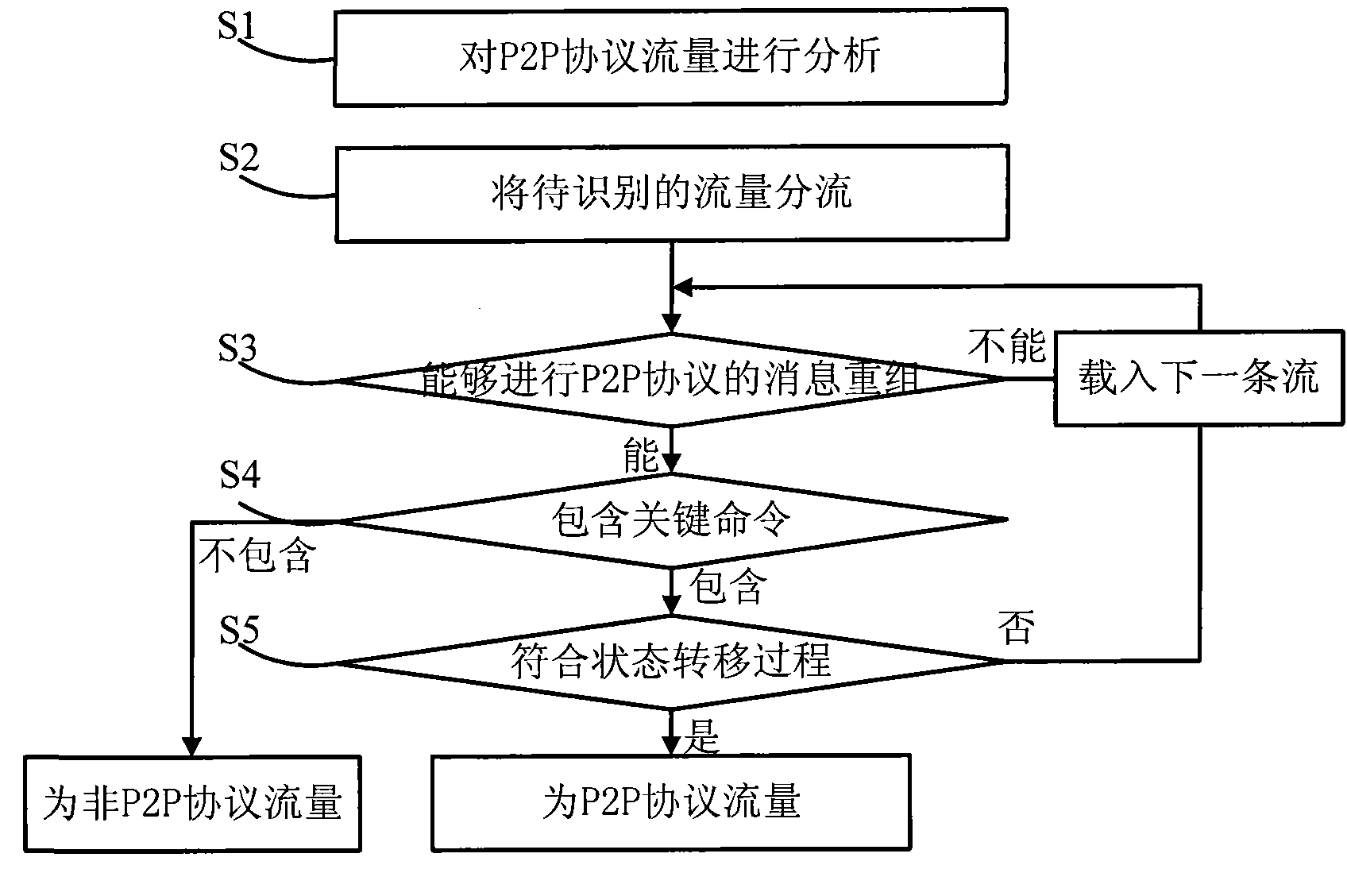
[0045] The P2P protocol traffic identification method and system proposed in the present invention will be described in detail in conjunction with the accompanying drawings and embodiments.
[0046]The present invention summarizes the structure of the P2P protocol based on a large number of observations on the P2P protocol and traffic, and innovatively adopts the heuristic message clustering technology to analyze the P2P protocol traffic, and obtains the working status of the P2P protocol The key interaction process state machine and the key commands in it, with the support of the key commands and the key interaction process state machine, can identify and classify the P2P protocol traffic in the traffic in real time. According to the P2P protocol traffic identification method of an embodiment of the present invention, especially the identification of Thunder traffic, the heuristic conditions for Thunder's message reorganization include:
[0047] (1) Xunlei header is not encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com