Method and device capable of acquiring executable file input table
A technology for inputting tables and purposes, applied to program control devices, computer security devices, instruments, etc., can solve problems such as programs that cannot run anymore, and achieve a high degree of automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
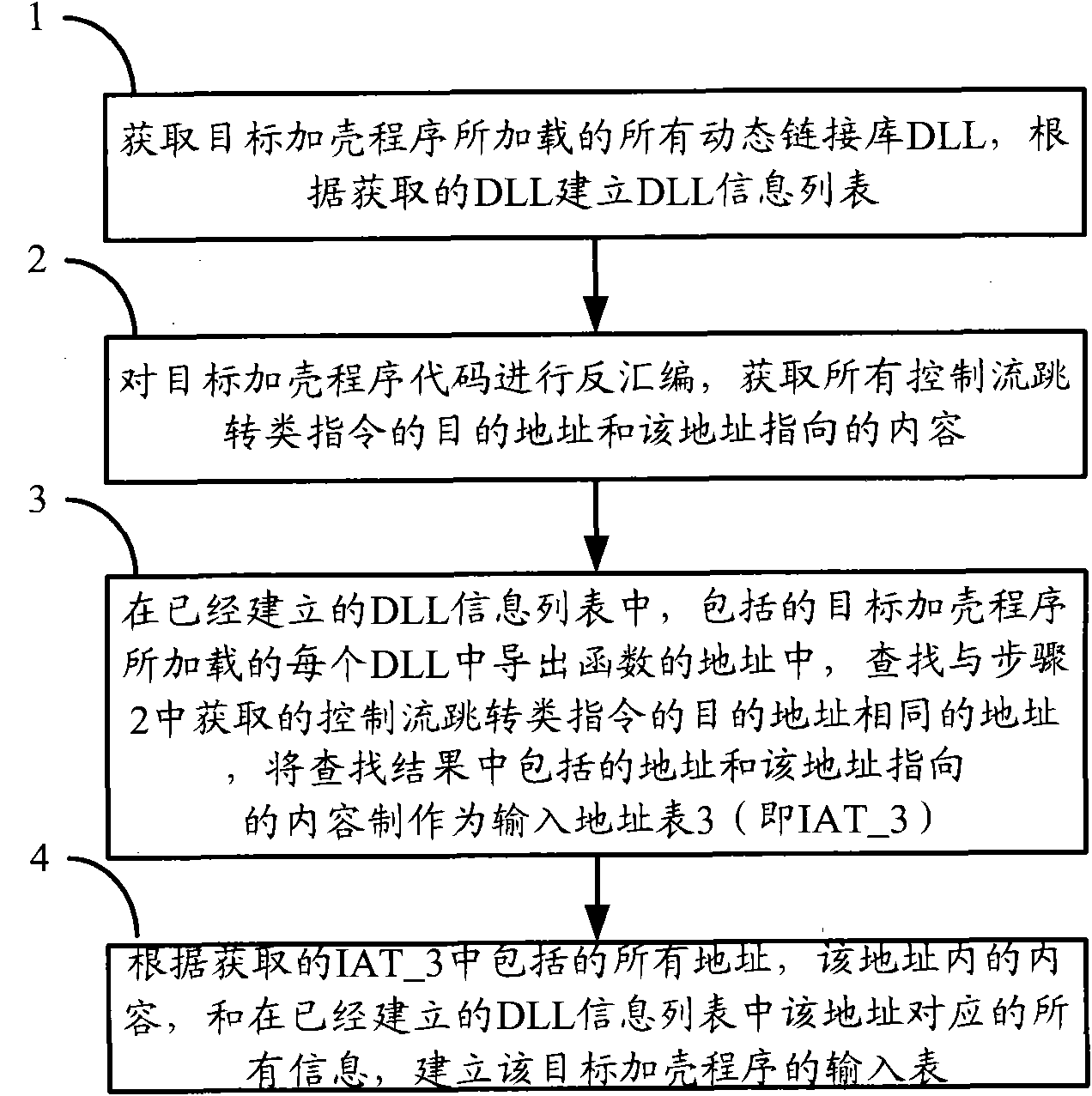
[0035] An embodiment of the present invention provides a method for obtaining an executable file input table. Before describing the method provided by this embodiment, firstly, the concept of an input table will be described, so as to facilitate the understanding of the method provided by this embodiment of the present invention.
[0036] The packaged target software to be run is composed of executable files, which will call one or more DLL files in the dynamic link library (DLL, Dynamic Link Library), that is, the code that calls the DLL or Data, the code or data of the calling DLL, is called input. The location of the input function address is determined by the operating system through the input table when the executable file is loaded. The input table (Improt Table) is an integral part of the executable file structure. When an executable file needs to call other file functions, it needs to look up the input table for addressing. The contents of the input table are all ad...
Embodiment 2
[0082] The embodiment of the present invention provides a method for obtaining an executable file input form, which is similar to the method provided in Embodiment 1, and can obtain the input form of the target packer program; and the method provided by the embodiment of the present invention, in On the basis of Embodiment 1, some operations are added to make the obtained input form more accurate, and also to make the operation process more efficient.
[0083] Attached below Figure 5 The method provided in this embodiment is described, and the method includes:
[0084] Step D1 and step D2 are the same as step 1 and step 2 in Embodiment 1, please refer to the description in step 1 and step 2;
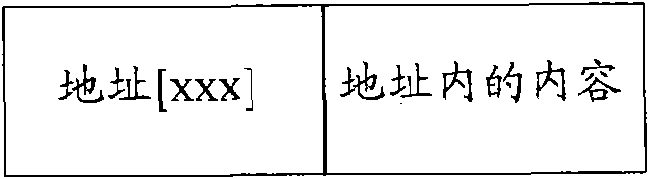
[0085] Step D3: Remove the addresses in the non-executable address range of the destination addresses of all control flow jump instructions obtained in step D2, and the content pointed to by the addresses in the non-executable address range; thus obtain IAT_1, the IAT_1 includes: the ...
Embodiment 3
[0107] An embodiment of the present invention provides a device for obtaining an executable file input table, such as Image 6 As shown, the device includes: a dynamic link library (DLL) information acquisition unit 100 , a disassembly unit 101 , a control flow jump instruction address acquisition unit 102 , an effective address acquisition unit 103 , and an input table reconstruction unit 104 .
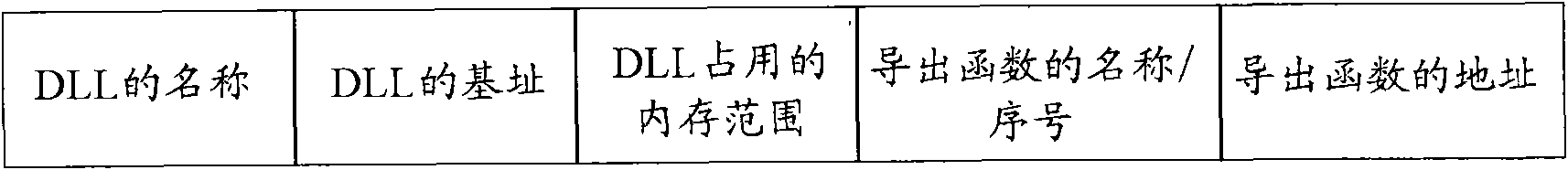
[0108] Wherein, the DLL information obtaining unit 100 is used to obtain all dynamic link library DLLs loaded by the target packer, and establishes a DLL information list according to the DLLs obtained, including: all DLLs loaded by the target packer in the DLL information list Name, the base address of each DLL loaded by the target packer, the memory range occupied by each DLL loaded by the target packer, the address of the exported function in each DLL loaded by the target packer, all items, and the name of the exported function in each DLL loaded by the target packer, and any one ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com