Method for detecting the improper removal of electronic equipment
A technology of electronic equipment and detection method, which is applied in the direction of computer security device, cooperating device, error detection/correction, etc., can solve problems such as key erasure, and achieve the effect of improving operability and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Hereinafter, the best mode for carrying out the present invention will be described with reference to the drawings.
[0035] [Structure of electronic equipment device]
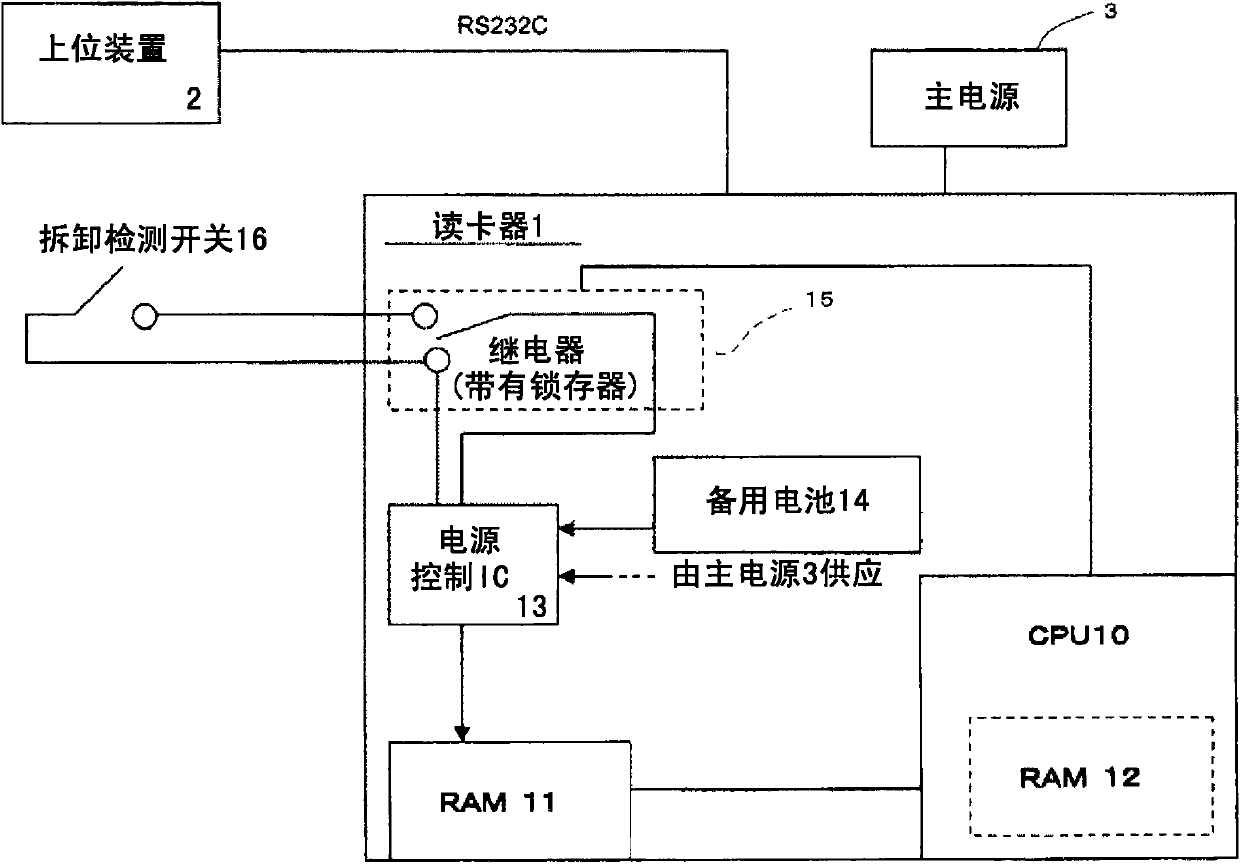
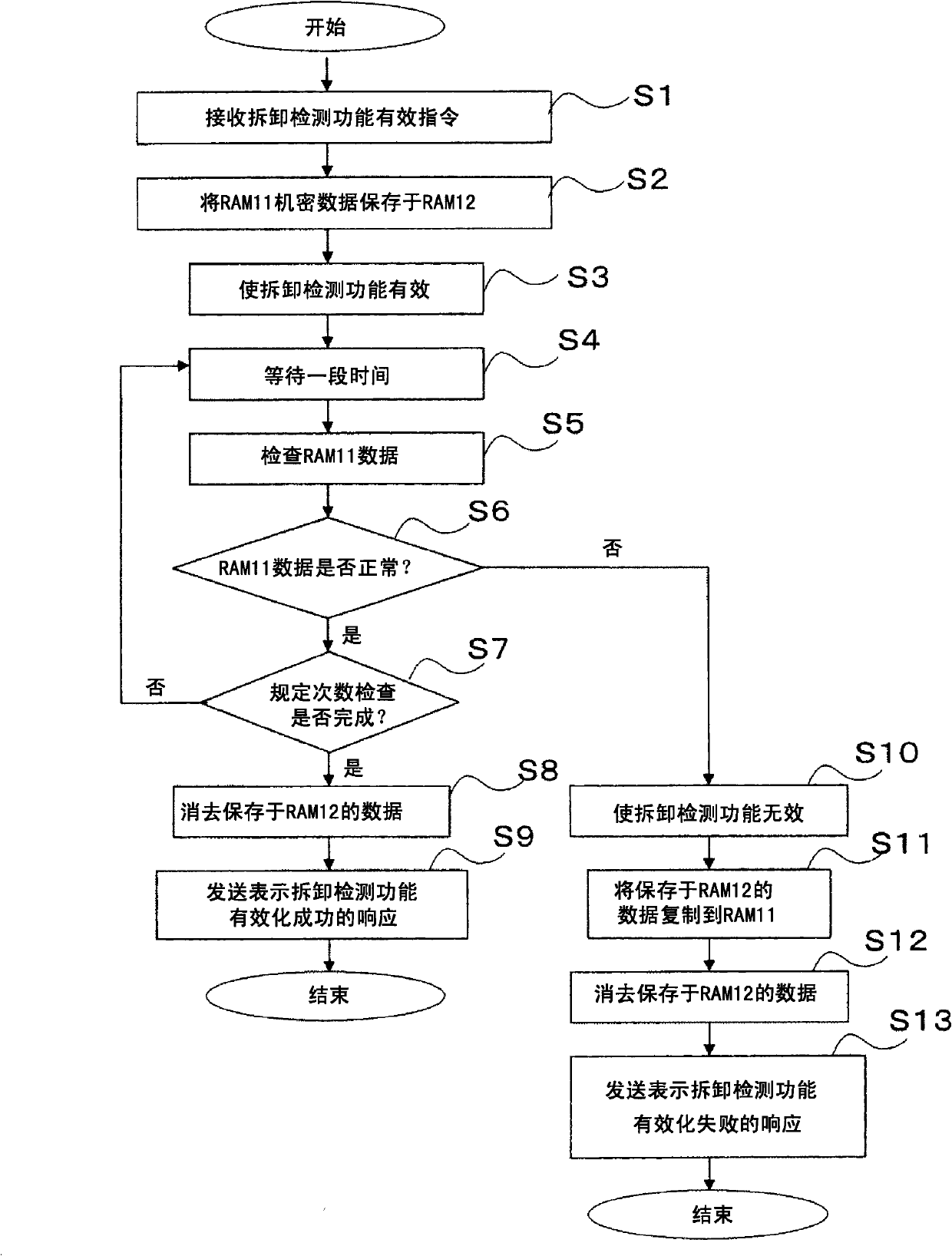
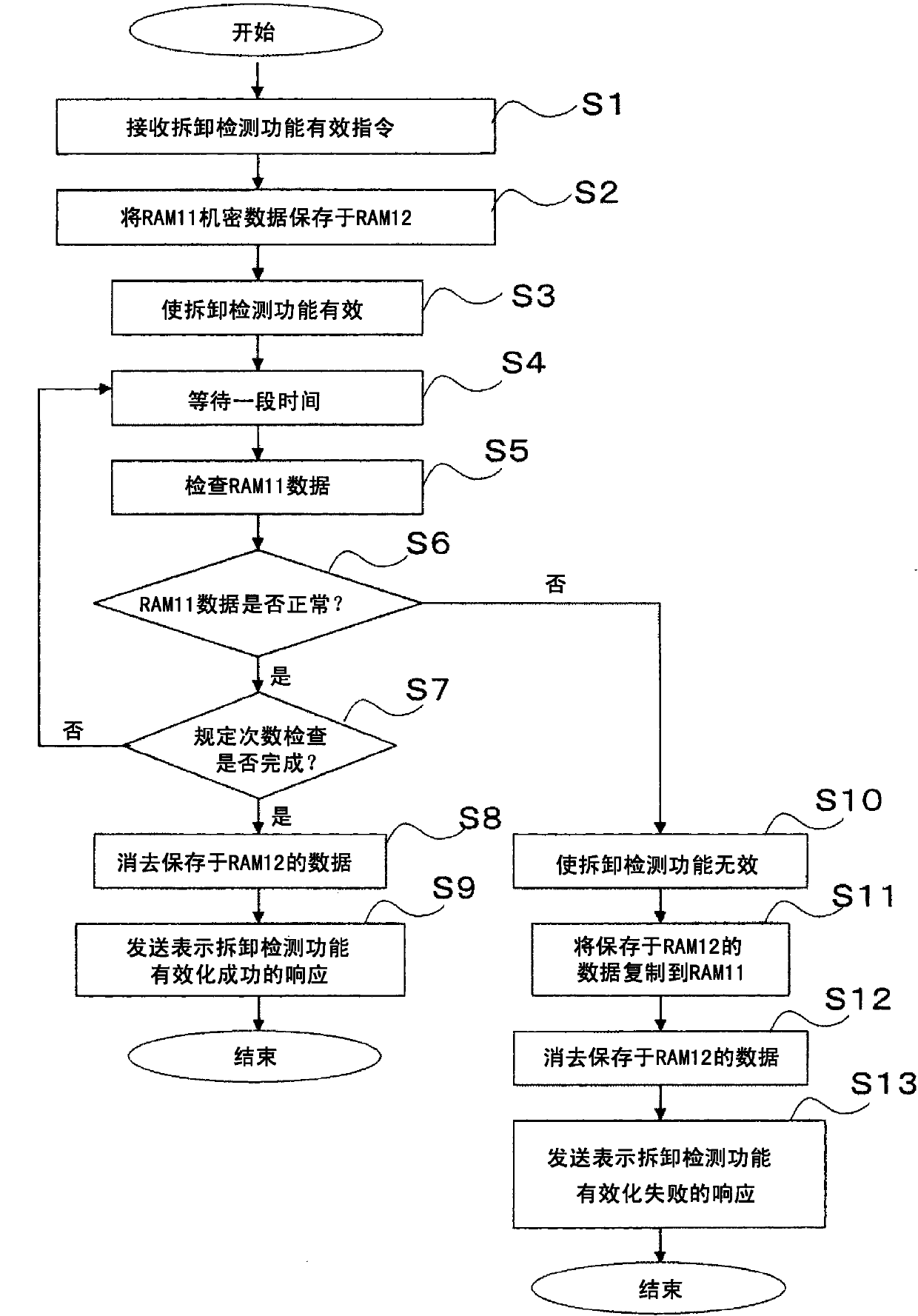
[0036] figure 1It is a block diagram showing the electrical configuration of the card reader 1 used in the fraudulent removal detection method according to the embodiment of the present invention. In this embodiment, the card reader 1 is mounted on a housing of a user-operated terminal operated by a user, such as a terminal at a gas station or an ATM, and the card reader 1 and a host terminal are accommodated in the housing. device 2. In addition, in this embodiment, the card reader 1 and the host device 2 are electrically connected through RS232C (Of course, other connection forms may also be adopted). In addition, the host device 2 may not be housed in the user operation terminal, but may be installed in another control device. In addition, in this embodiment, although the card reader 1 is used as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com