Access method of distributed internet
An access method and Internet technology, applied in the field of distributed Internet access based on password two-way authentication, can solve the problems of wasting bandwidth, reducing query efficiency, increasing server burden, etc., to improve system stability, improve query efficiency, The effect of reducing the load on the server
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
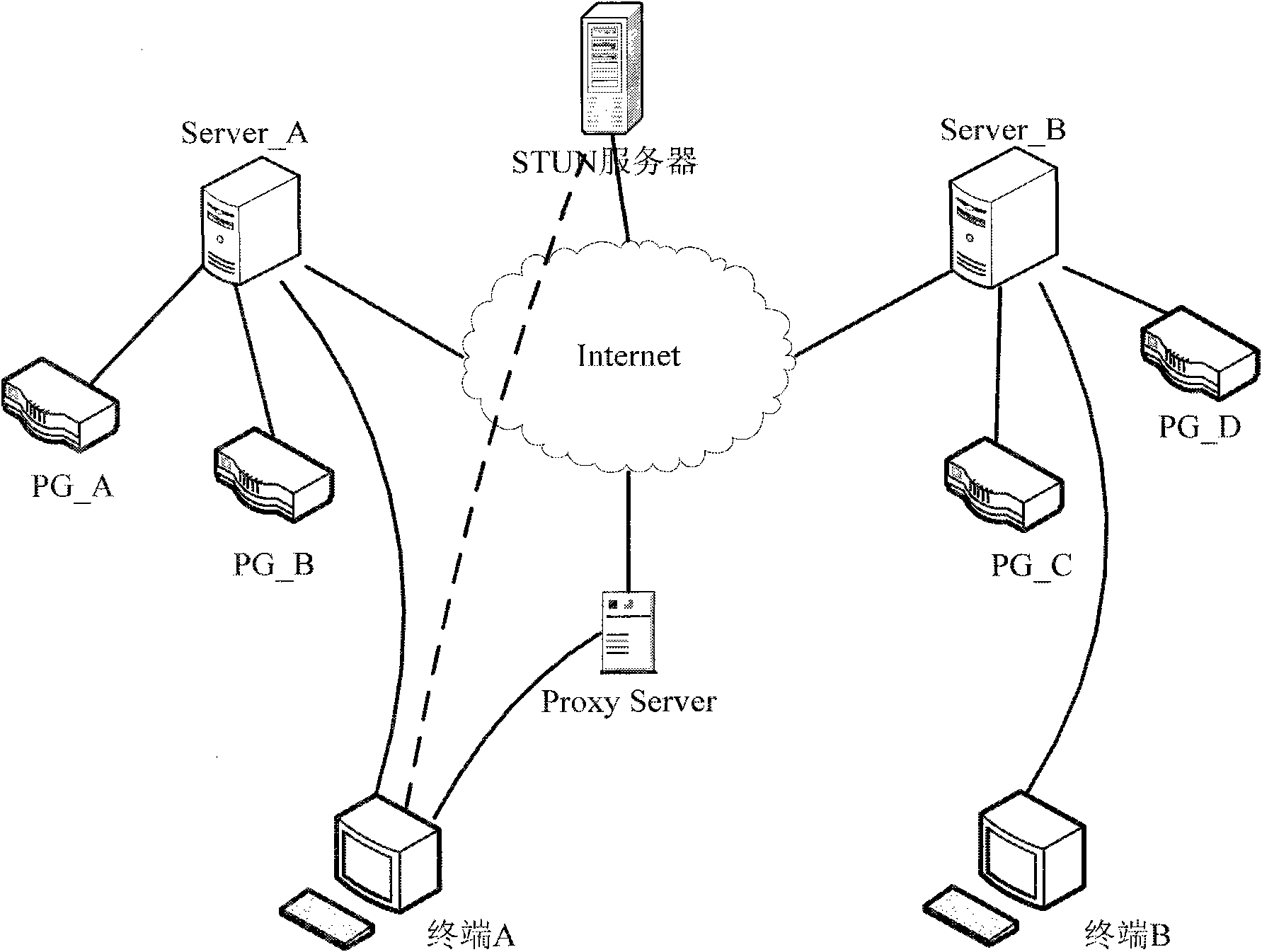
[0035] figure 1 It is a topological structure diagram of the distributed Internet access network proposed by the present invention. In the present invention:
[0036] Proxy Server refers to a proxy server. Server A and Server B are the target servers.
[0037] PG_A, PG_B, PG_C, and PG_D refer to terminals on a private network or a public network, respectively.
[0038] The STUN server is used for firewall penetration, so that terminals can learn their public network address, the NAT type of the network they are in, and the port of the public network egress.
[0039] NAT refers to Network Address Translation.
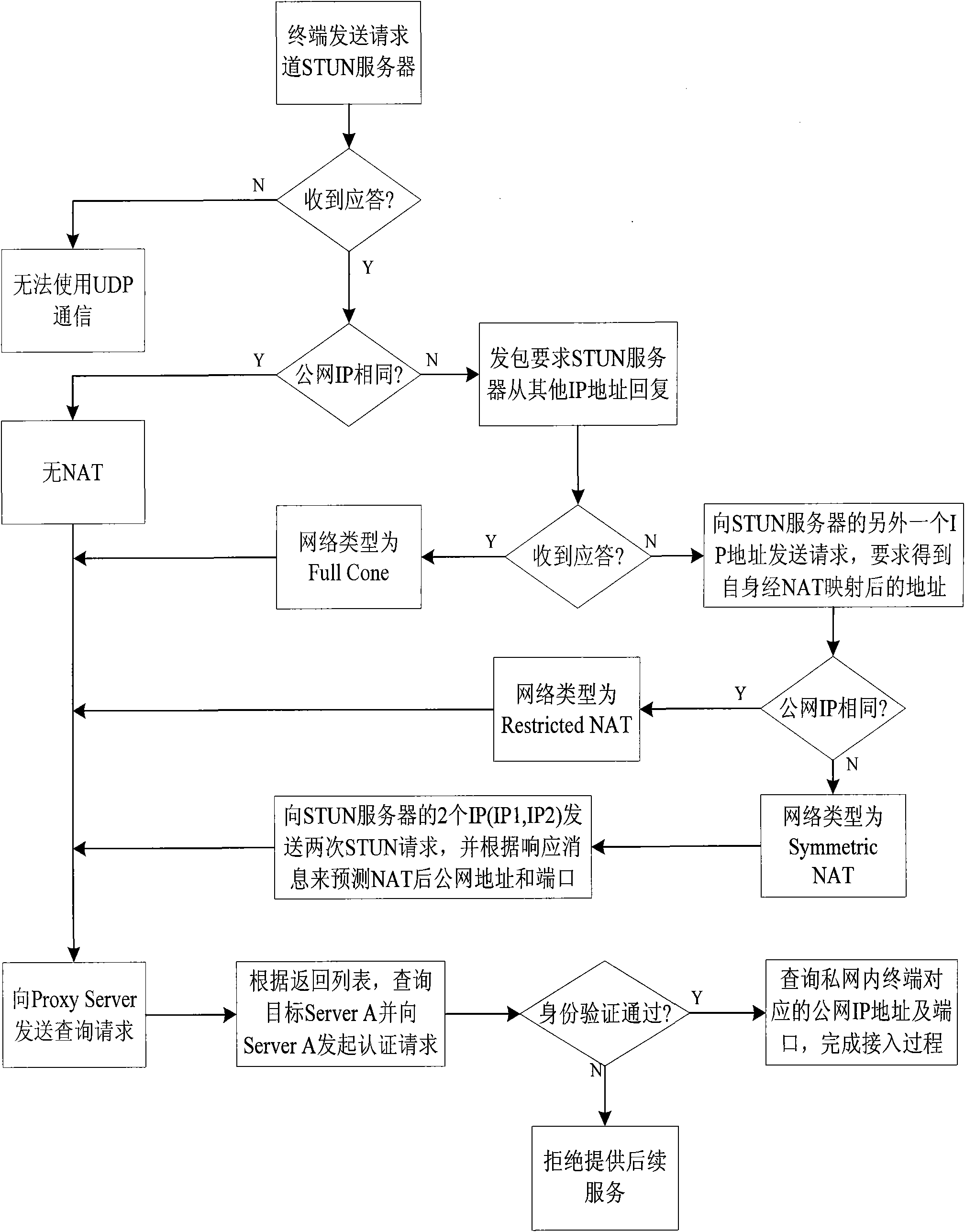
[0040] Detecting the NAT type of the network means that by sending a request packet to the STUN server with a public network IP address, the terminal judges the NAT type of the current private network it is in according to the message IP address and port returned by the STUN server.
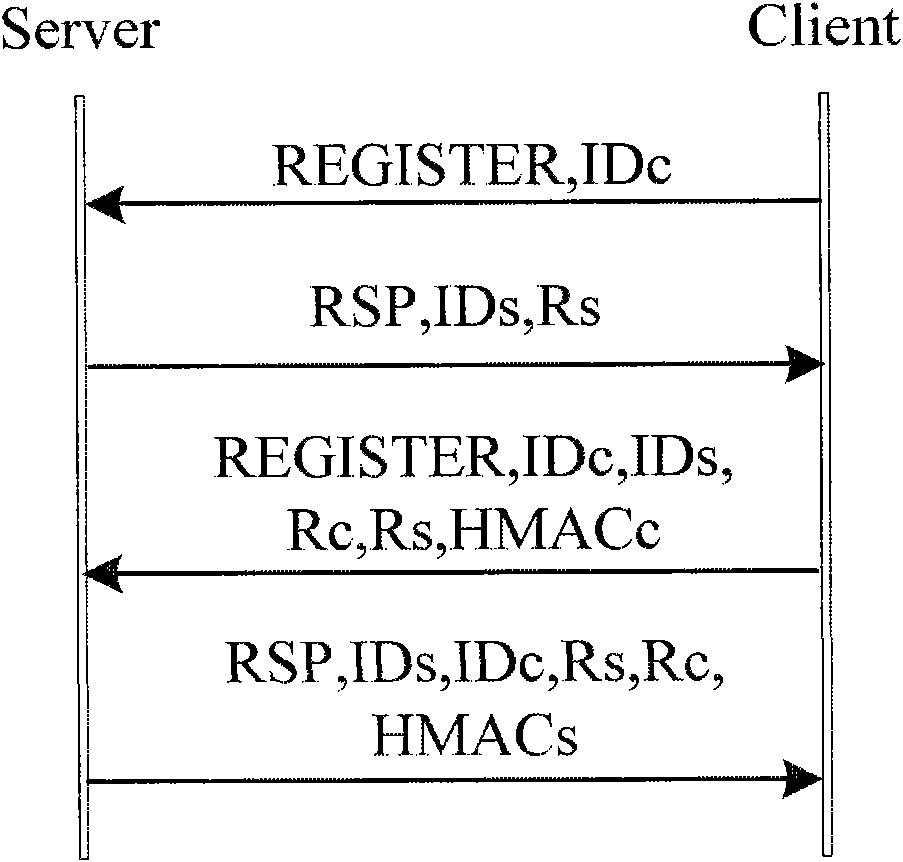
[0041] Legal terminals mean that no matter these terminals are inside the private ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com