Method for improving data security under SaaS application
A security and user data technology, applied to the public key and key distribution of secure communication, can solve problems such as increasing burden and affecting operation speed, and achieve the effect of improving data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] The invention discloses a method for improving data security under a SaaS application, and the method includes the following steps:
[0033] When the user registers, a data encryption key is assigned to the user; the data encryption key is encrypted with the public key algorithm of the server, and the encrypted key is kept by the user;
[0034] When users use SaaS services, they use encrypted communication protocols to communicate;
[0035] The user's data is encrypted and decrypted using a symmetric encryption algorithm, and the data encryption key is only temporarily stored in the memory of the application server. The symmetric encryption algorithm is DES or AES, and the asymmetric algorithm is RSA or ECC algorithm.
[0036] Preferably, when encrypting user data, the document data generated by a designated application is selected for encryption and decryption. When a user opens or saves data, the application server that provides services to the user applies to the a...
Embodiment 2
[0040] By adopting transparent encryption and decryption technology in the data server, the user's data files are dynamically encrypted and decrypted, so that the data is always in an encrypted state in the data server, while it is in a clear text state at the user end. At the same time, encrypted communication is adopted, and the user The data key is kept by itself, and the data key is not stored in the application server, so as to ensure that the user's normal usage habits are not affected, and the security of user data in the server can be guaranteed. So that users don't have to worry about leaking their confidential information when using SaaS services, and promote the development of SaaS applications.
[0041] The specific implementation steps are as follows:
[0042] Install a transparent encryption and decryption program in the application server. Using a symmetric encryption algorithm, for the application process, it decrypts the data process read into the memory, and...
Embodiment 3
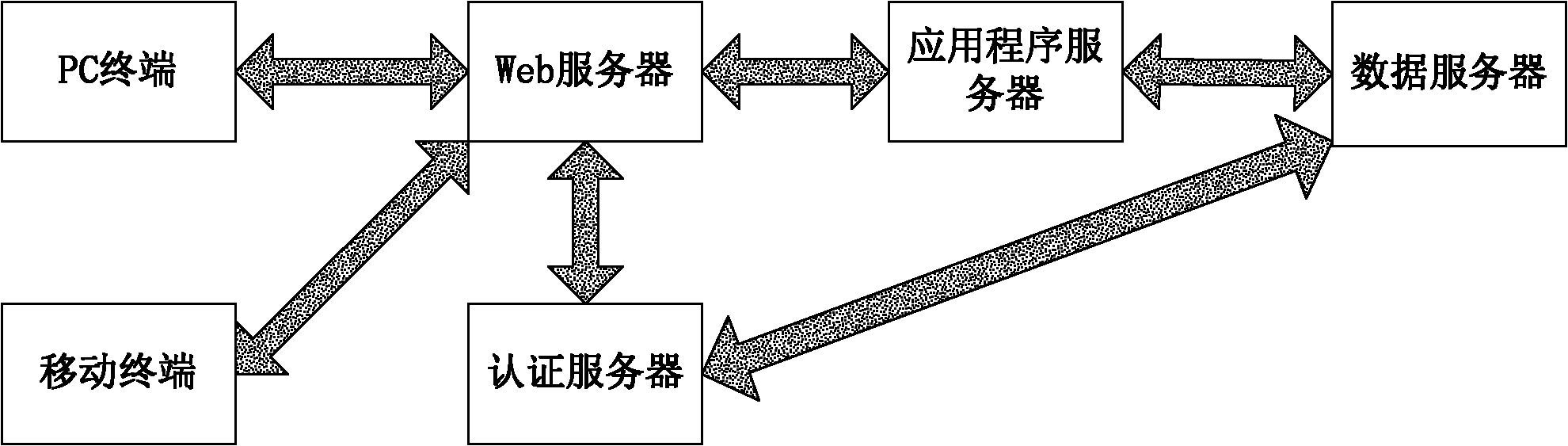
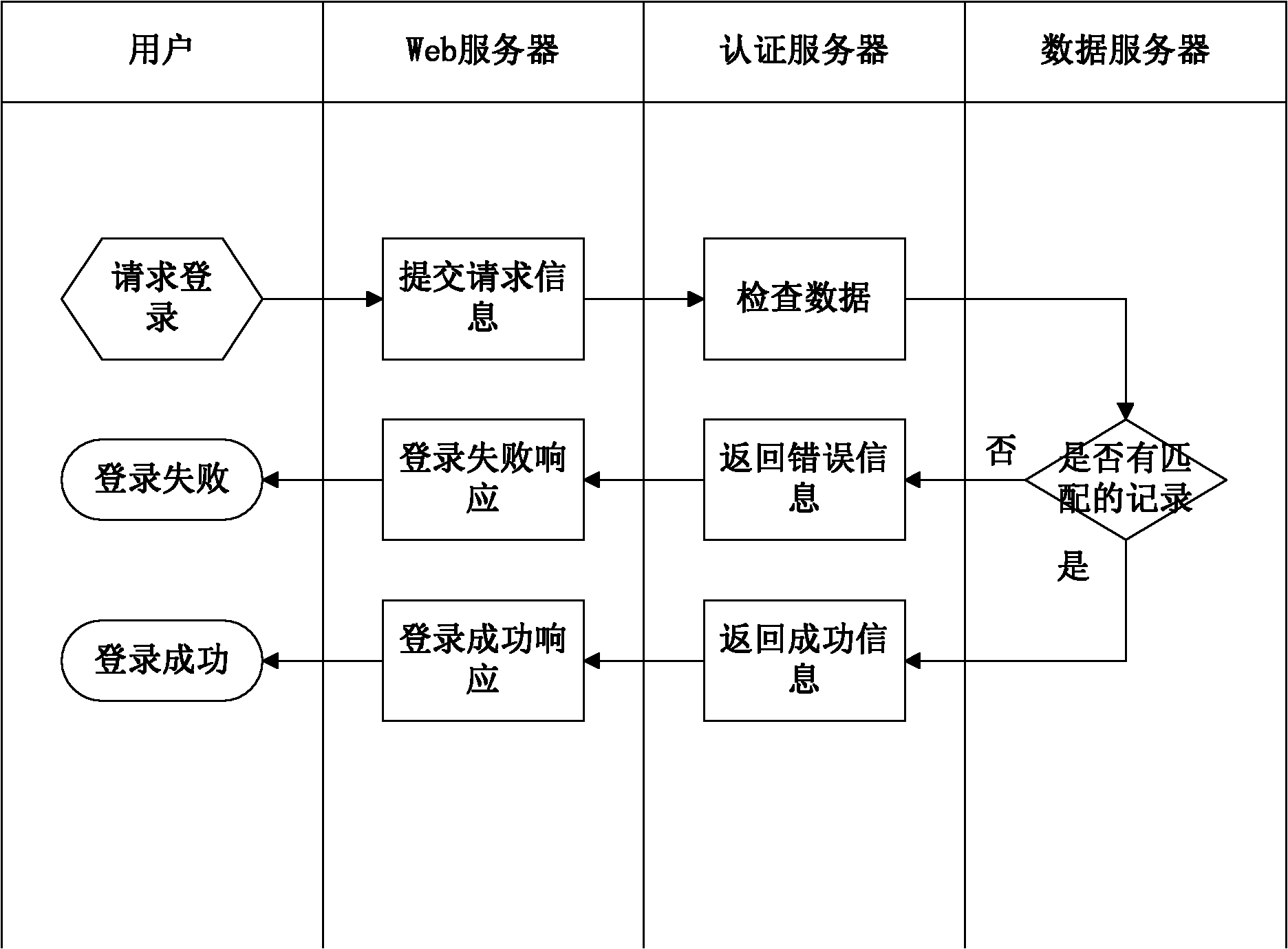
[0047] An encryption system is installed on the application server side, and the system adopts transparent encryption technology. The connection between the user and the server uses the HTTPS protocol to encrypt the communication. Transparent encryption uses a symmetric algorithm, which can be 3DES or AES, etc. The user data key is encrypted using an asymmetric algorithm, and the encrypted key can be saved in the extension field of the X509 certificate and stored in the user's certificate. The application program applies for a key from the authentication server to encrypt and decrypt user data. The normal use of the service by the user will not be affected in any way.
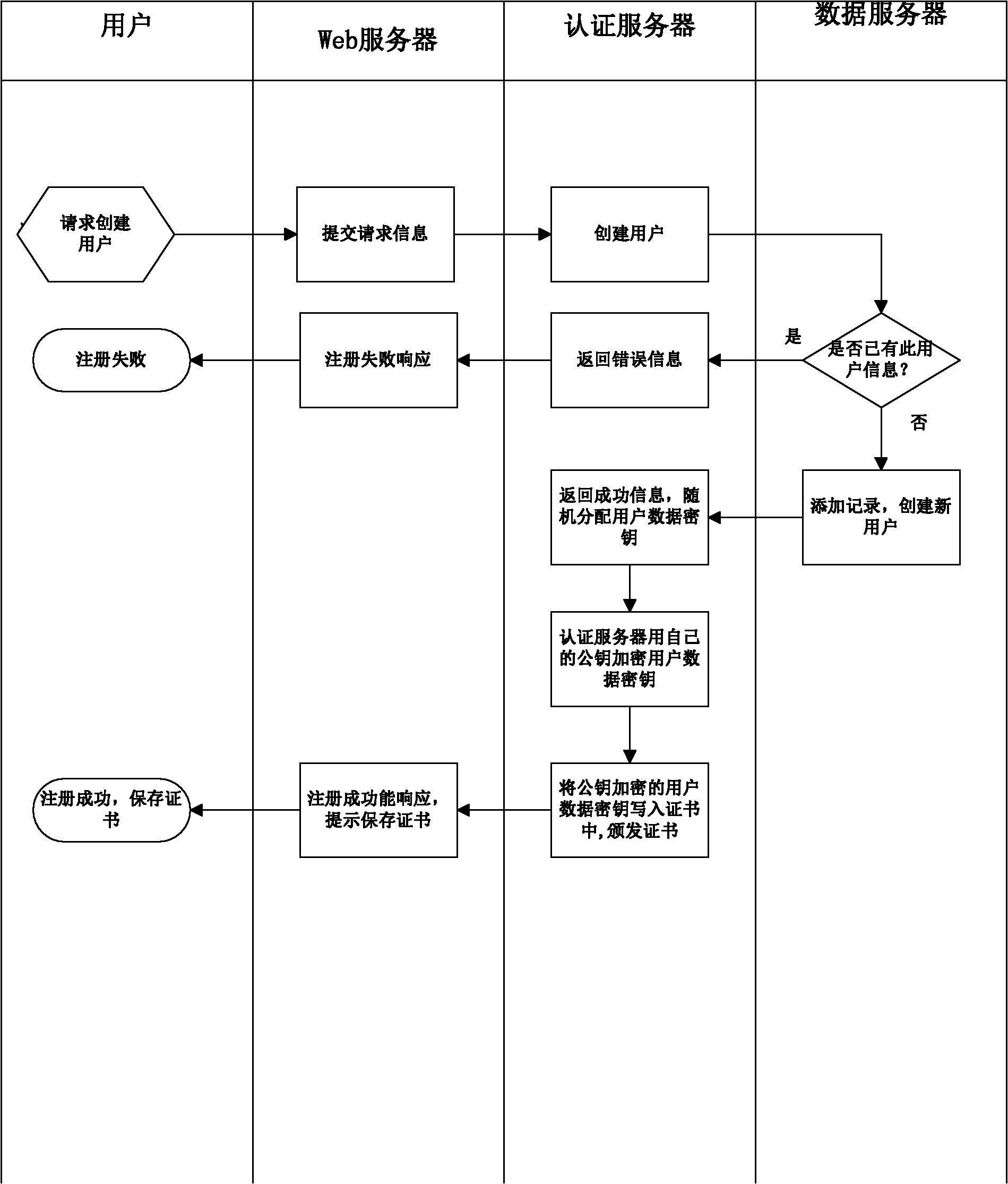
[0048] User registration steps are as follows:
[0049] 1. If figure 2 As shown in , the user applies to register a new user on the web page, and the authentication server judges whether registration is allowed. If registration is possible, a record is added to the database and a successful response is ret...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com