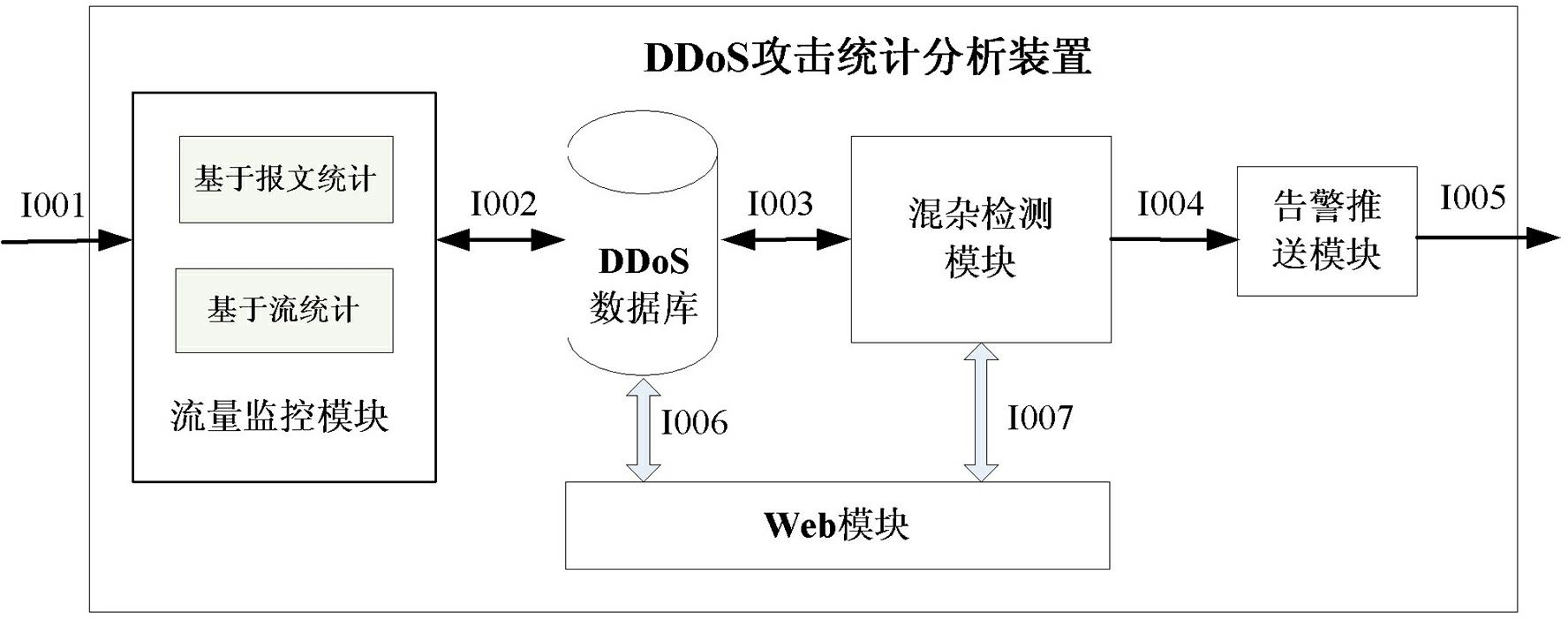
Promiscuous mode-based DDoS (Distributed Denial of Service) attack detection method and device
A promiscuous mode, attack detection technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
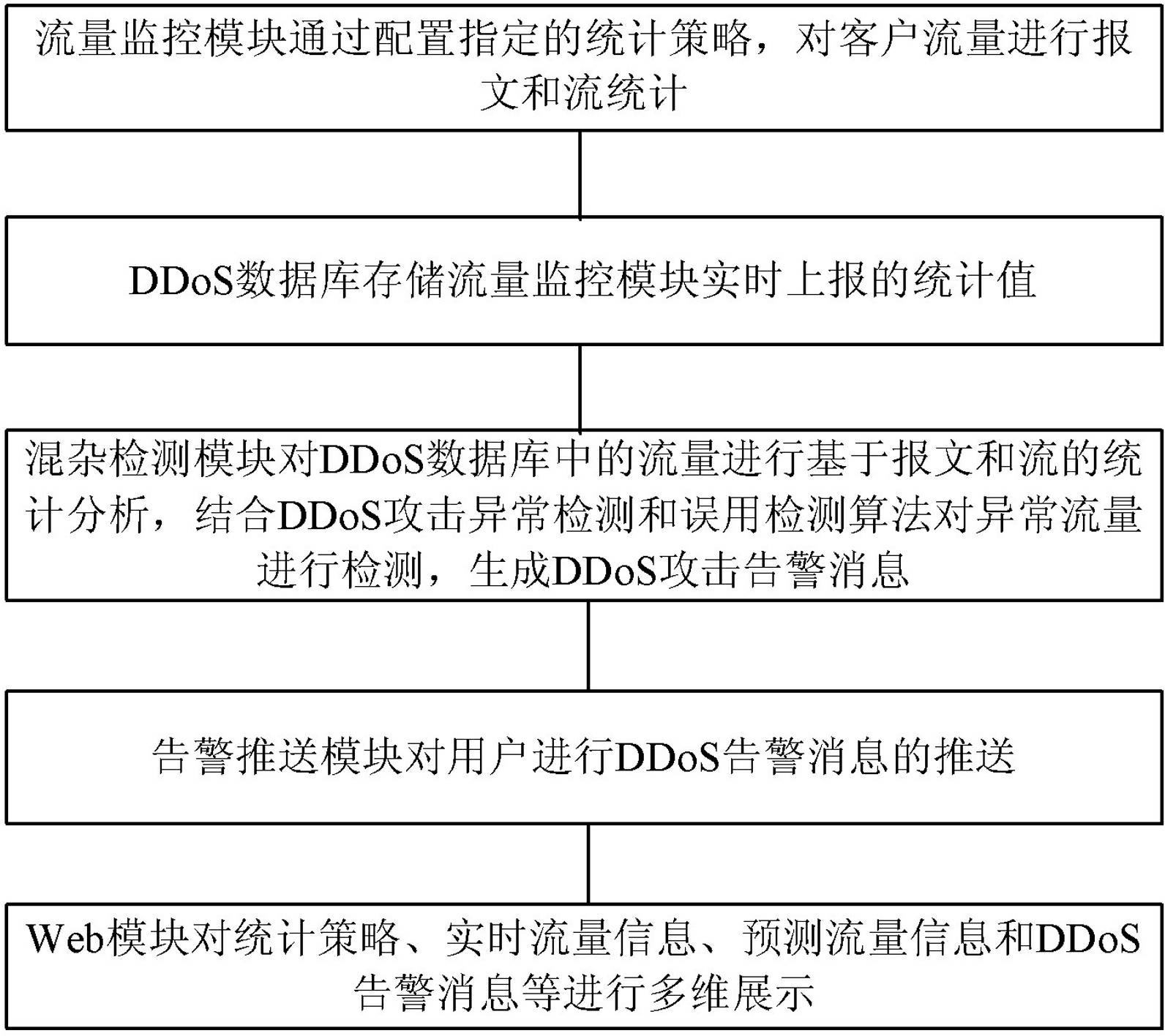
[0021] Embodiment one: see Figure 5 , the DDoS attack detection method based on the promiscuous mode of the present invention, the basic detection process is: the traffic in the DDoS database is based on the dual-scale statistics of the message and the flow, and the promiscuous mode combining misuse detection and anomaly detection is adopted. Detect traffic and generate DDoS attack alarm messages. In this promiscuous mode, packet detection and flow detection are performed in parallel, and anomaly detection and misuse detection are detected in series.
[0022] At the beginning, when there were few feature samples in the misuse detection mode, the method of anomaly detection was used to detect DDoS attacks for the first time. With the continuous increase of feature samples, the detection of DDoS attacks was converted to the method of misuse detection. .
Embodiment 2
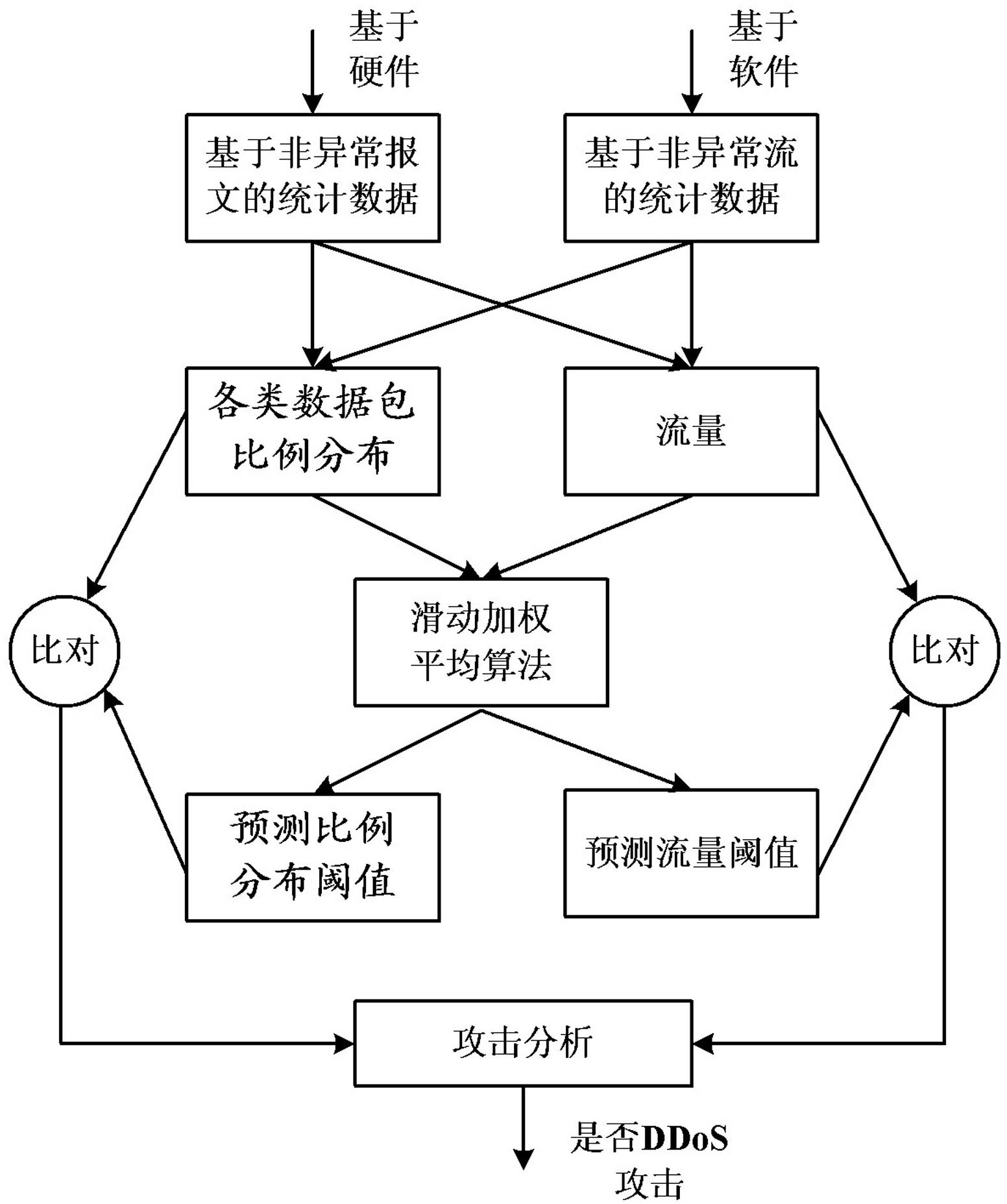
[0023] Embodiment two: see image 3, this embodiment is based on the promiscuous mode DDoS attack detection method, on the basis of Embodiment 1, specifically discloses the anomaly detection based on the message and the abnormal detection process based on the flow: the abnormal detection based on the message, with the real non-abnormal The statistical value of the historical packets of the data is used as the benchmark data to calculate the proportion distribution and statistical number of each type of data packets in the total number of data packets per unit time, and predict the threshold value of the proportion distribution and statistical number of various types of data packets at the current moment. The threshold Calculated according to the "sliding weighted average" algorithm, the sliding window adopts four granularities of second level, minute level, hour level, and day level, and compares the predicted threshold with the current data packet proportion distribution and s...
Embodiment 3
[0024] Embodiment three: see Figure 4 , the present embodiment is based on the promiscuous mode DDoS attack detection method, on the basis of the second embodiment, specifically discloses the message-based misuse detection and flow-based misuse detection process: message-based misuse detection, excerpted typical The DDoS attack anomaly feature value obtained by the packet-based anomaly detection is put into the misuse pattern feature library as the detection feature of the misuse pattern. When a certain feature is the same, it is judged that a DDoS attack has occurred; for flow-based misuse detection, the typical DDoS attack abnormal feature value obtained by flow-based anomaly detection is extracted and put into the misuse pattern feature library as the detection feature of the misuse pattern. When the characteristics of flow proportion distribution and statistical number are the same as a certain characteristic in the misuse detection characteristic library, it is judged th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com