Method for preventing DOS attack by utilizing priority queue
A priority queue and priority technology, applied to electrical components, transmission systems, etc., can solve problems such as message loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
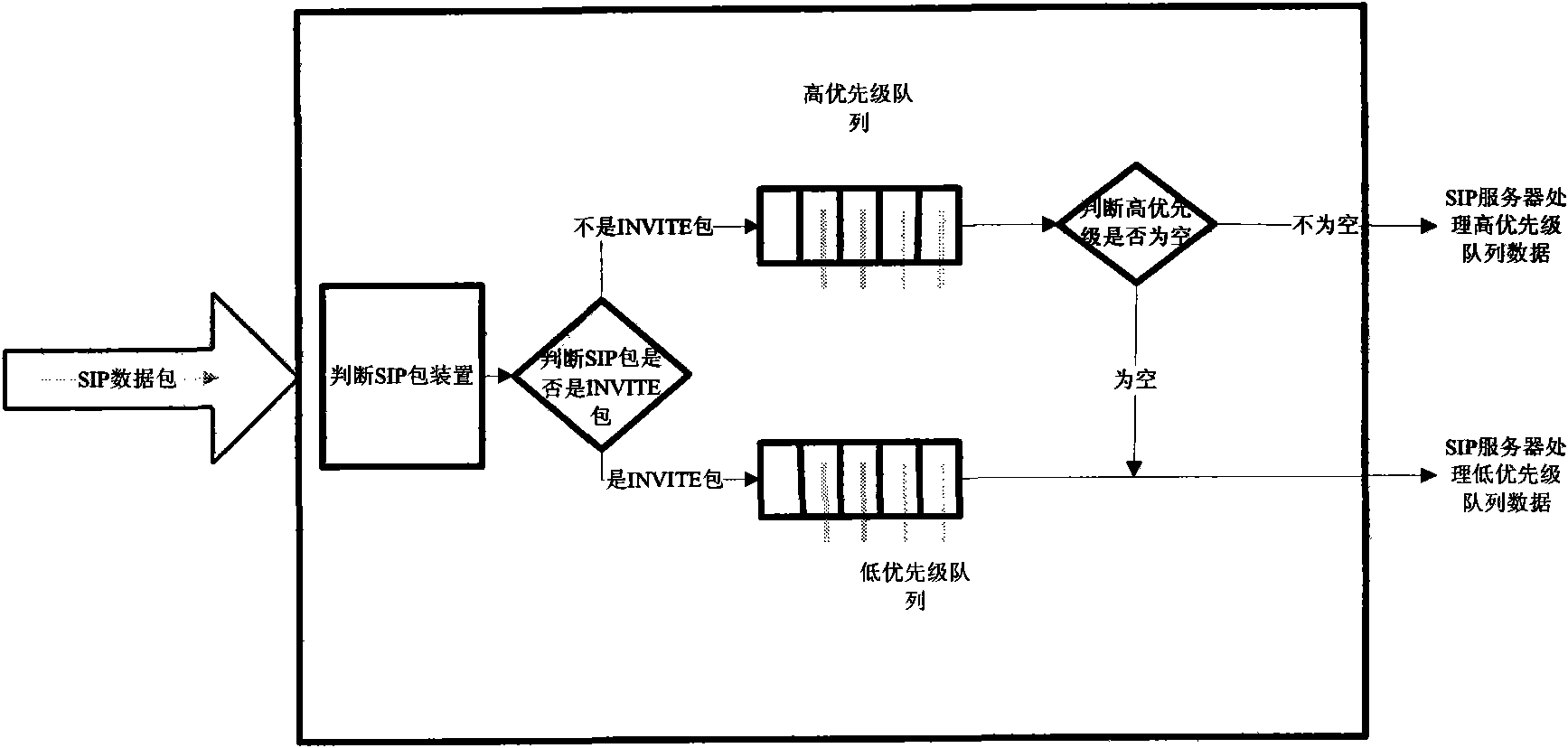
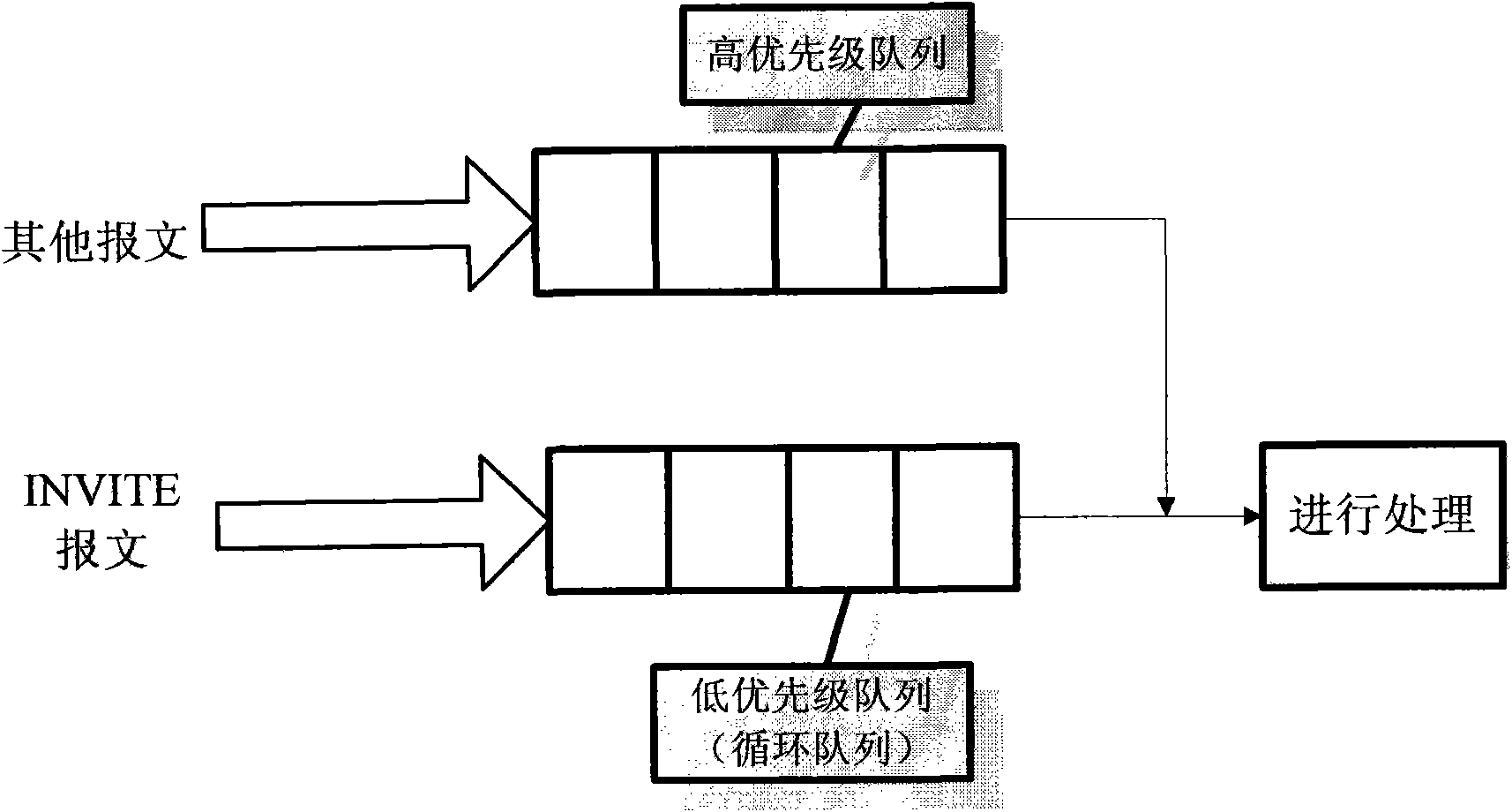
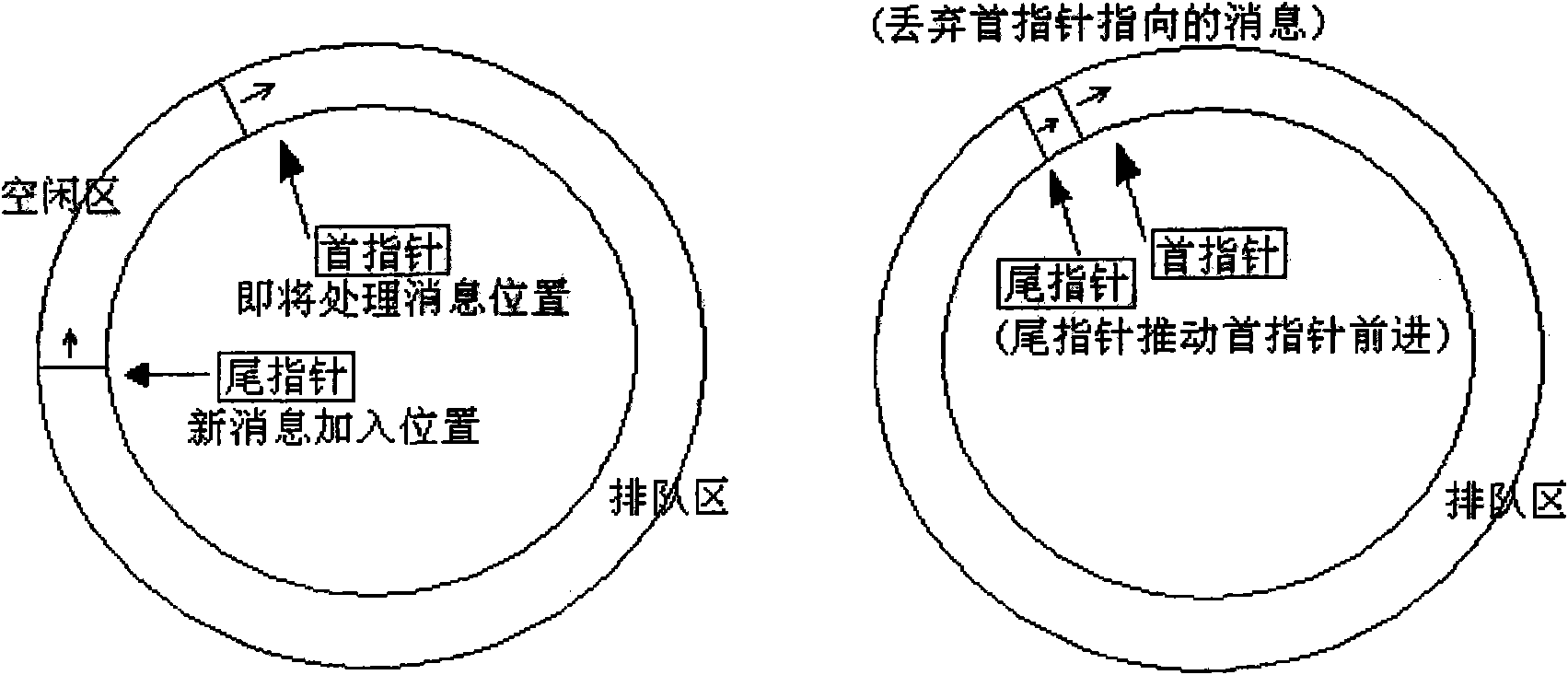
[0031] The present invention is applied at the receiving end of a SIP server. When a data packet is received, it is first judged whether it is an INVITE data packet, and then it is determined which queue to enter. The queue is divided into a high priority queue and a low priority queue, and only the INVITE data packet enters a low priority queue. SIP packets that are not INVITE packets enter the high-priority queue, and the SIP server processes the data packets in the high-priority queue first, and only starts processing the low-priority queue when the high-priority queue is empty, and the low-priority queue It is designed as a circular queue, so that when it is attacked by INVITE DOS, it will automatically drop packets by pushing the head pointer forward through the tail pointer, so as to avoid congestion and reduce delay. like figure 1 As shown, the method for preventing copying of webpage text content provided by the embodiment of the present invention includes:
[0032] l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com