Internet protocol (IP) telephone network-based trust model construction method
A technology of IP telephony and trust model, which is applied in the direction of telephone communication, electrical components, transmission systems, etc. It can solve problems such as attacks and servers are vulnerable to attacks, and achieve the effects of ensuring security, avoiding information theft and tampering, and enhancing accessibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
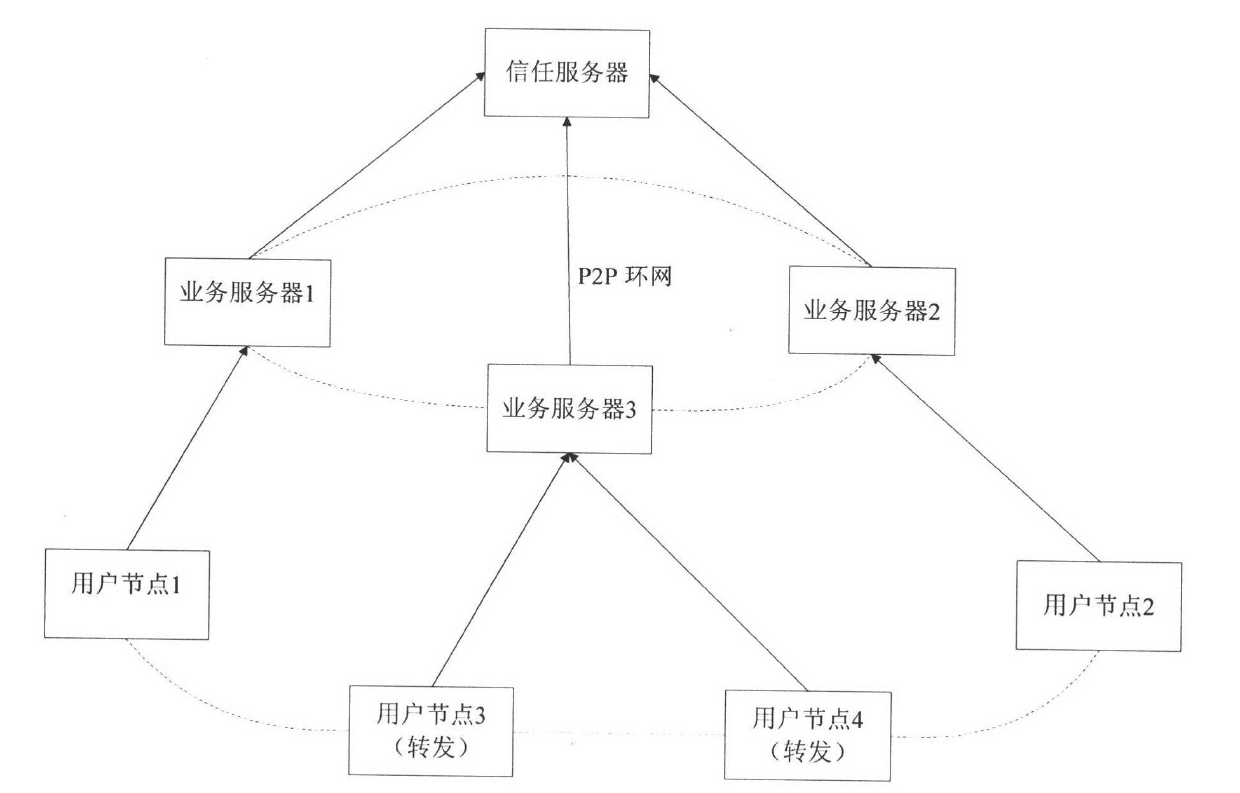
[0052] 1. System structure:
[0053] The entire trust mechanism is to allow the service server SS to quickly select a suitable user node UE as the voice data forwarding node, and to restrict the VoIP call function of the user node UE that is illegally authorized. The trust process includes data transmission, restricted access, and point calculation. Due to the need to achieve information exchange between two different platforms, several sets of TCP-based socket transmissions have been established. It is mainly used to realize information transmission between UE and SS, and transmission between SS and trust server TN.
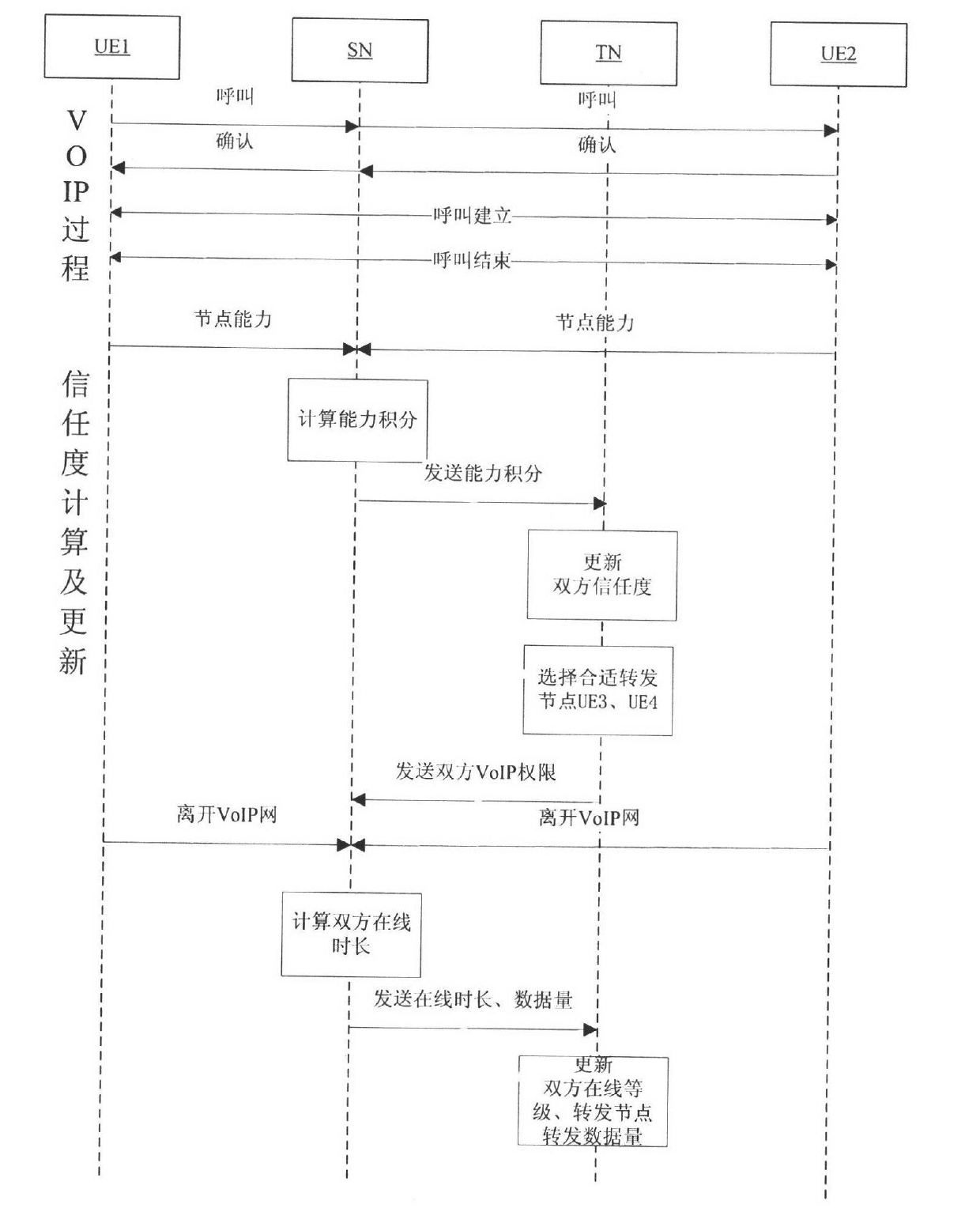
[0054] Two, method flow
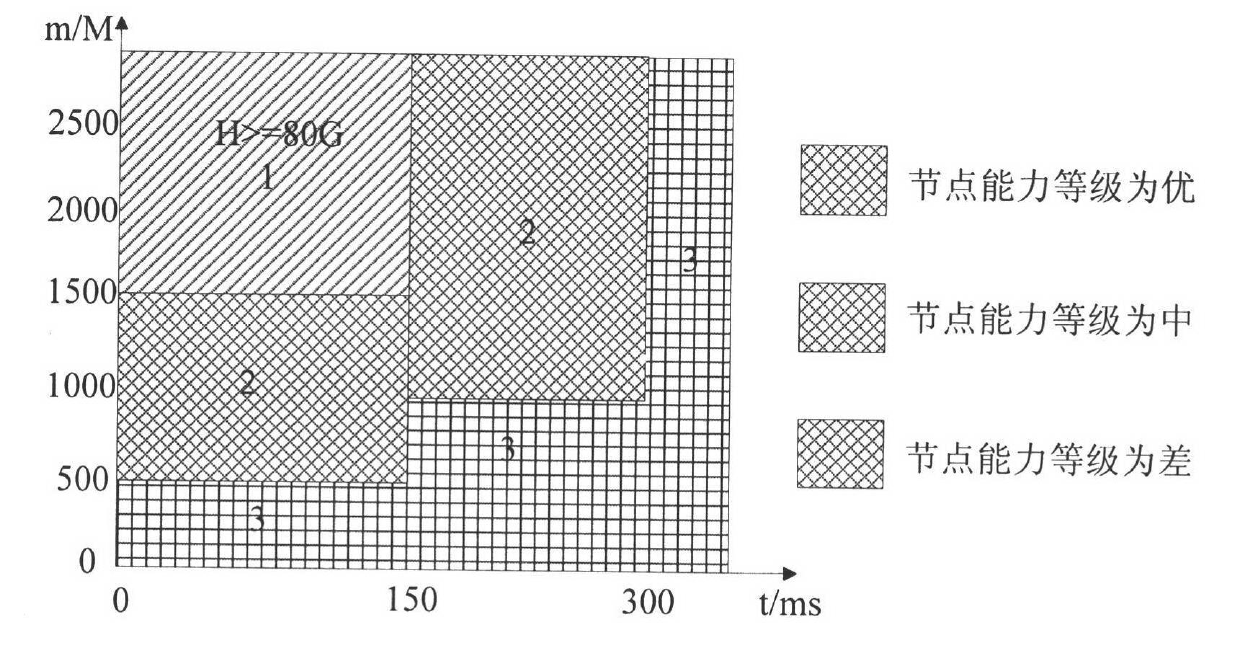
[0055] The VoIP trust mechanism metrics, trust calculation, and trust update adopt mechanisms similar to those at the entity layer. This section mainly discusses the trust model of VoIP networks from the aspects of trust evaluation criteria, credit calculation and update, and the construction process is as follows :
[0056] 1. Develop trust...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com