Application program copyright protection method and digital copyright protection system
An application program and copyright protection technology, which is applied in the field of digital copyright protection methods and systems, can solve the problems of easy-to-crack application program copyright and lack of protection, and achieve the effect of simplifying the process of copyright verification and high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
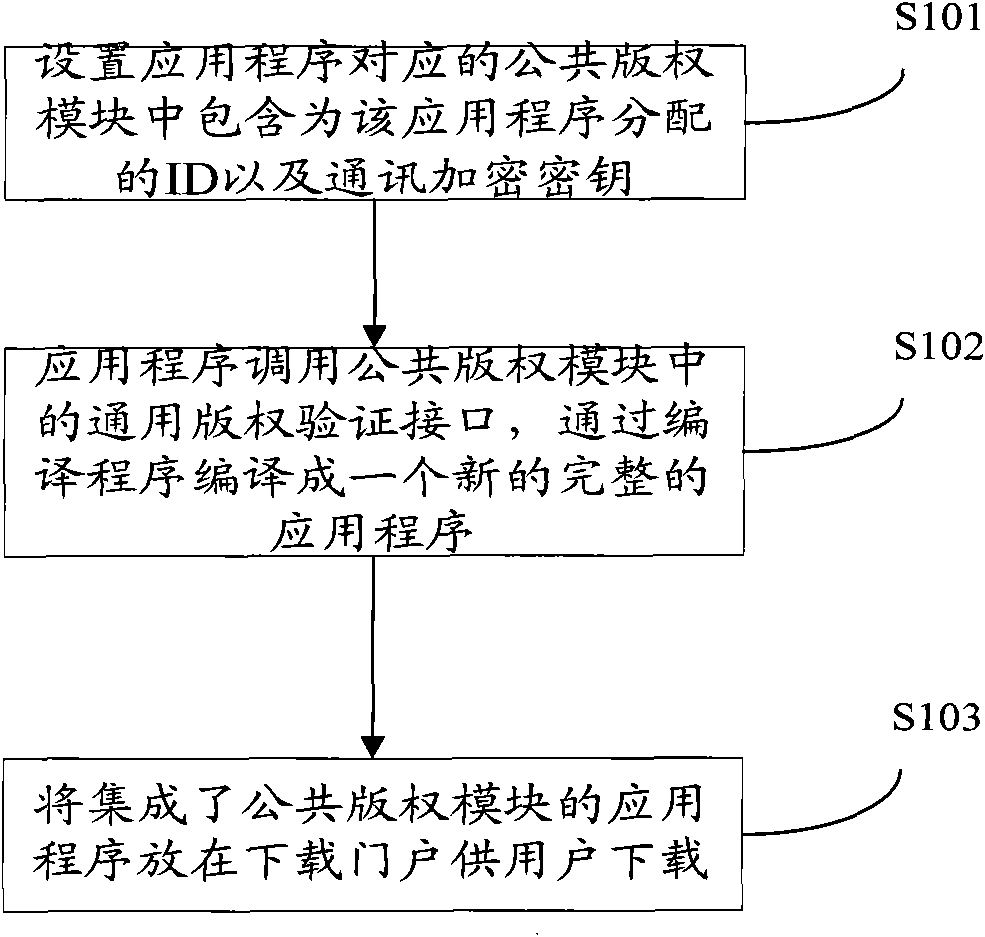
[0019] In the present invention, the application program is protected by integrating the public copyright module in the application program. The application program is integrated with the public copyright module, which is a process similar to assembly. The application program is integrated with the public copyright protection module, which is difficult to separate and thus safer. Compared with the original application, the new application only has one more step of copyright verification before the application runs. This step is completed by the public copyright module. After passing the copyright verification, the operation of the new application is the same as that of the original application. difference. Integrating the application program with the public copyright protection module can be compiled into a complete new executable application program by compiling the program. Such as figure 1 Shown is an example diagram of the integration mode diagram of the public copyright...
Embodiment 2
[0025] Based on the application program protection method and application program protection system of the present invention, when a user downloads an application program through a download portal website, the copyright server provides a copyright file for the user to download. The copyright server records the correspondence between the application program ID and the communication encryption key. When the copyright server receives the copyright verification request message from the public copyright module, it parses out the application program ID from it, and queries the communication encryption key according to the corresponding relationship.
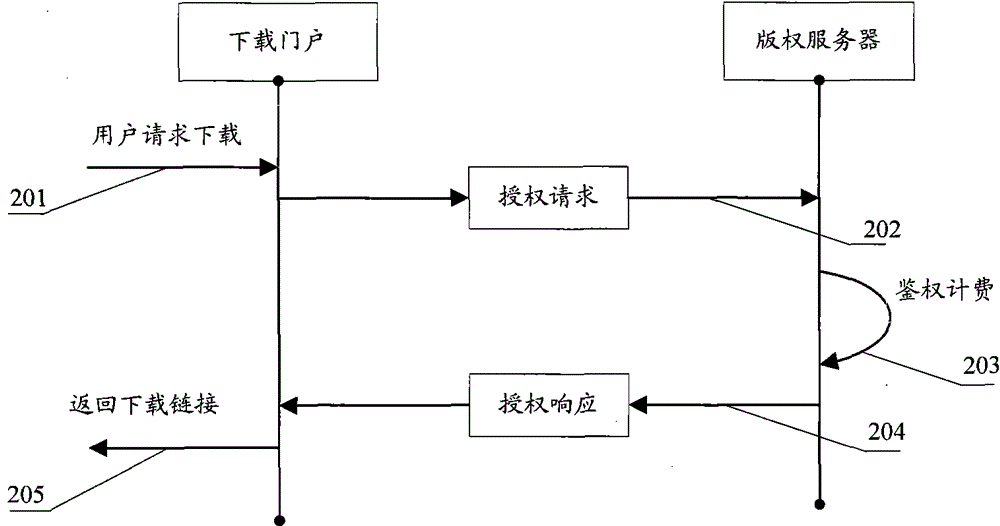
[0026] Such as figure 2 Shown is an example diagram of the user downloading application program of the present invention.
[0027] Step 201: the user logs in to the download portal, selects an application program and sends an authorization request to the portal website.
[0028] Step 202: The download portal sends an authorization re...
Embodiment 3
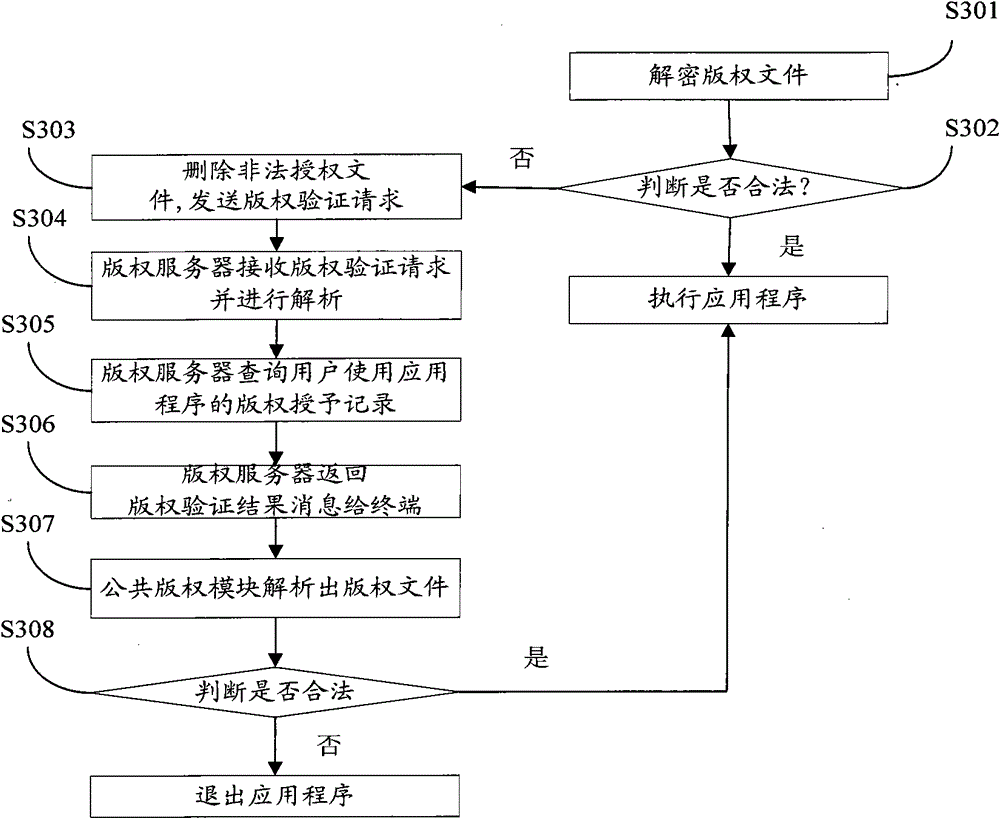
[0033] Users who want to use the application must pass the verification of the public copyright module. Such as image 3 Shown is the process diagram of verifying the user's copyright by the public copyright module of the present invention.
[0034] Step 301: Use the communication encryption key to decrypt the copyright file to obtain the user ID, application program ID and authorization result.
[0035] Step 302: The public copyright module verifies the legality. If it is legal, the verification is completed, and the application program starts to be executed; otherwise, the local copyright verification result is invalid, and the process turns to step 303 . This step is mainly to compare the SIM number and verified application ID obtained on the terminal with the SIM card number and application ID in the copyright file. If both are the same, and the authorization result allows the use of the application, it is legal authorized.
[0036] Step 303: Delete the local illegal c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com