Method and computer for protecting computer security based on bios password
A computer security and password protection technology, applied in the computer field, can solve problems such as low protection performance and easy cracking, and achieve the effect of protecting security and preventing illegal modification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
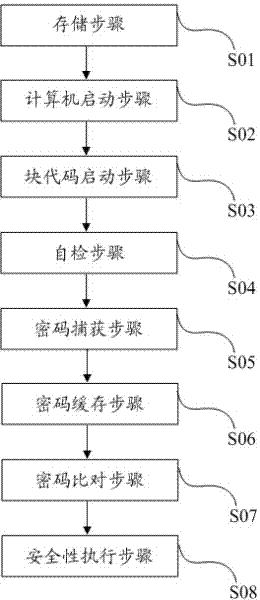
[0037] Embodiment one, see figure 1 Shown, the method for protecting computer security based on BIOS password of the present embodiment, comprises the following steps:
[0038] S01, storage step, the background writes the BIOS password in the BIOS chip, sets the parameter of the password check option in the BIOS, and stores this parameter in the CMOS chip; wherein, the password check option is whether to carry out password verification when controlling the execution of the BIOS unit, the BIOS will determine whether to implement this password protection according to the parameter setting;
[0039] S02, computer starting step, press the computer switch, start the computer, after the power supply voltage is stable, the CPU jumps;
[0040] S03, the block code start step, the BIOS starts the block code;
[0041] S04, the self-inspection step, the hardware device is self-inspected, and when the self-inspection is passed, the control display pops up a password input dialog box, req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com