A Quantum Key Distribution System for Secure Communication in Electric Vehicle Smart Charging Network
A quantum key distribution and intelligent charging technology, applied in key distribution, can solve problems such as failure to meet encryption requirements, improve security and reliability, increase distribution rate, and overcome low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
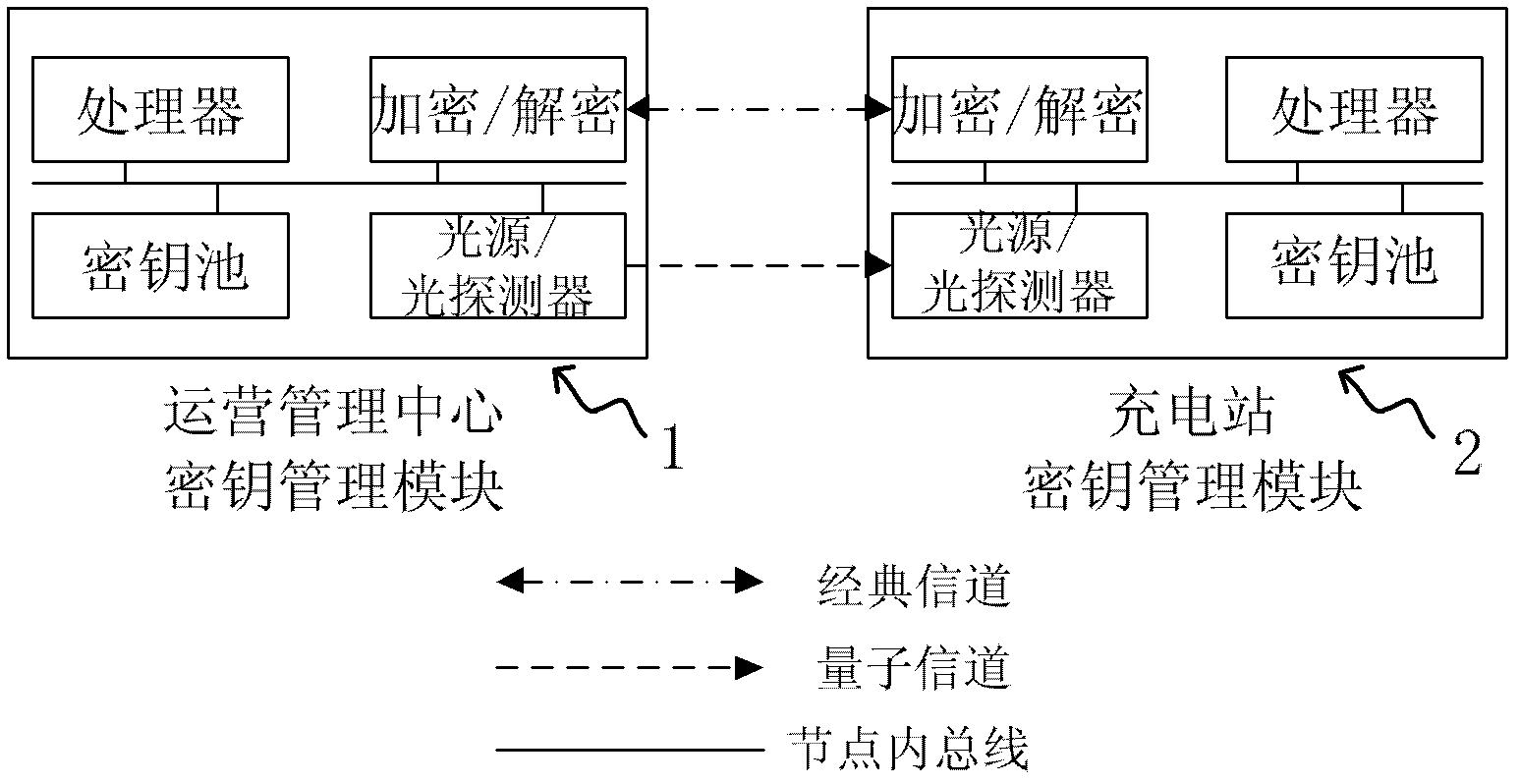
[0024] Quantum key distribution, based on the basic principles of quantum mechanics, unconditionally securely distributes keys between two directly connected points. Taking the most classic BB84 protocol as an example, the protocol shares 4 quantum states to form two sets of orthogonal bases, and each set of orthogonal bases is also a set of measurement bases. The correct result can only be obtained by using the same group of measurement basis to measure the quantum state. The specific communication process is as follows: the sender of the key randomly selects one of the four quantum states, and sends it to the receiver through the quantum channel, the receiver randomly selects a measurement base to measure, and obtains a result, both parties record their own The selection and measurement results are compared with each other through classical channels, and the results of those wrongly selected measurement bases are deleted. If necessary, the final key can be established betwe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com