Private network detection and traverse compounding method for P2P (Peer-to-Peer) network application system
A P2P network and application system technology, applied in the field of large-scale network applications, can solve the problems that network nodes cannot provide internal and external network address mapping, difficult to support large transmission volume, performance bottlenecks, etc., to achieve good adaptability and traversal rate, The effect of improving data sharing efficiency and high pass rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
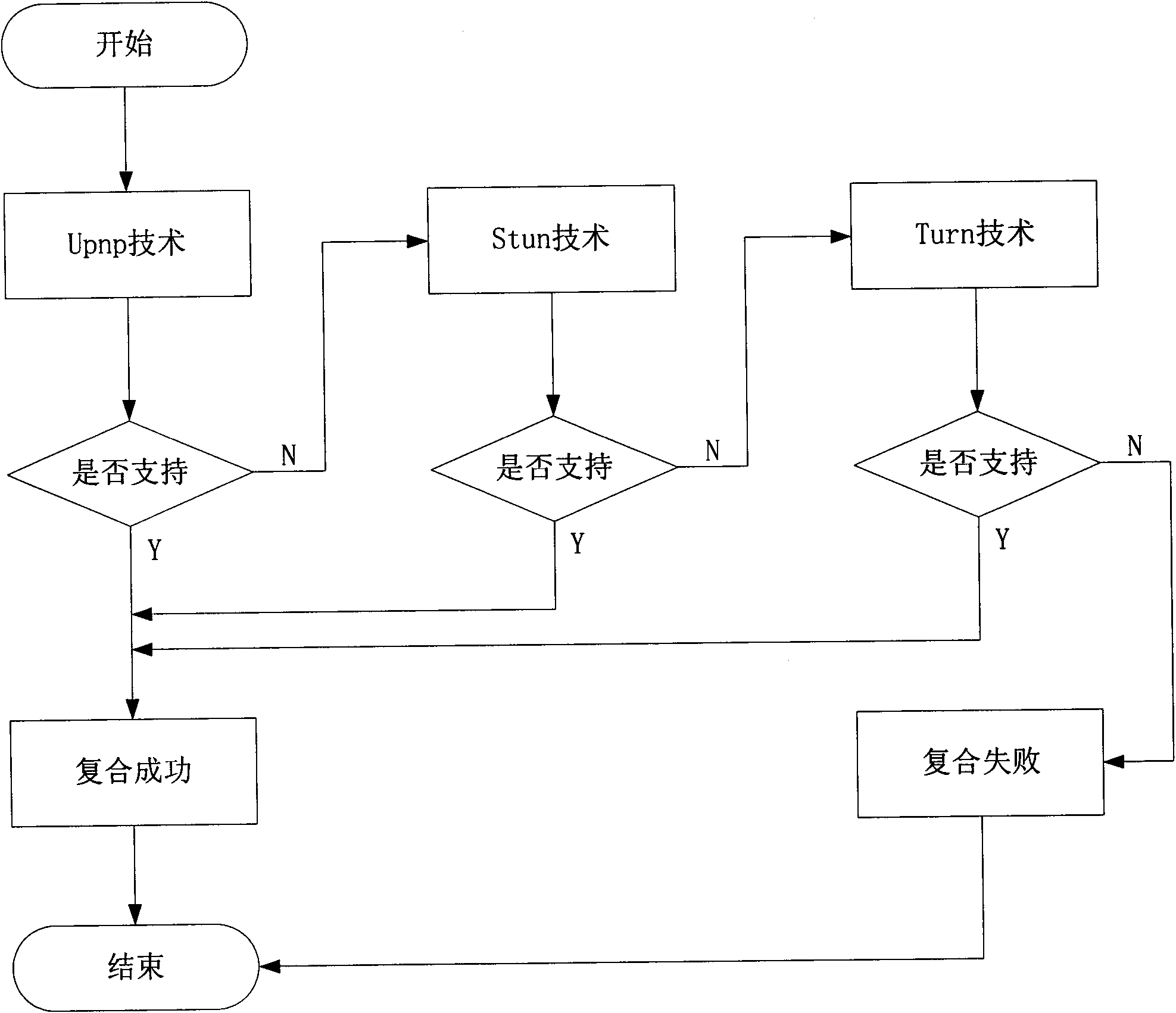
[0024] The method of the present invention comprises the following steps:
[0025] 1. Set different priorities for the three methods, the priority order is: UPNP, STUN, TURN.
[0026] 2. Detect and classify the network where the node is located. If the detection result shows that the network environment where the node is located can be opened to external nodes through UPNP technology, then use UPNP technology to realize NAT traversal of the internal nodes of the network.
[0027] 3. For a node that cannot support the UPNP method, use the STUN mechanism to detect the traversal problem of the node in the STUN environment; if the network environment where the node is located can meet the requirements of the STUN technology, use the STUN technology to realize the private network traversal of the node .
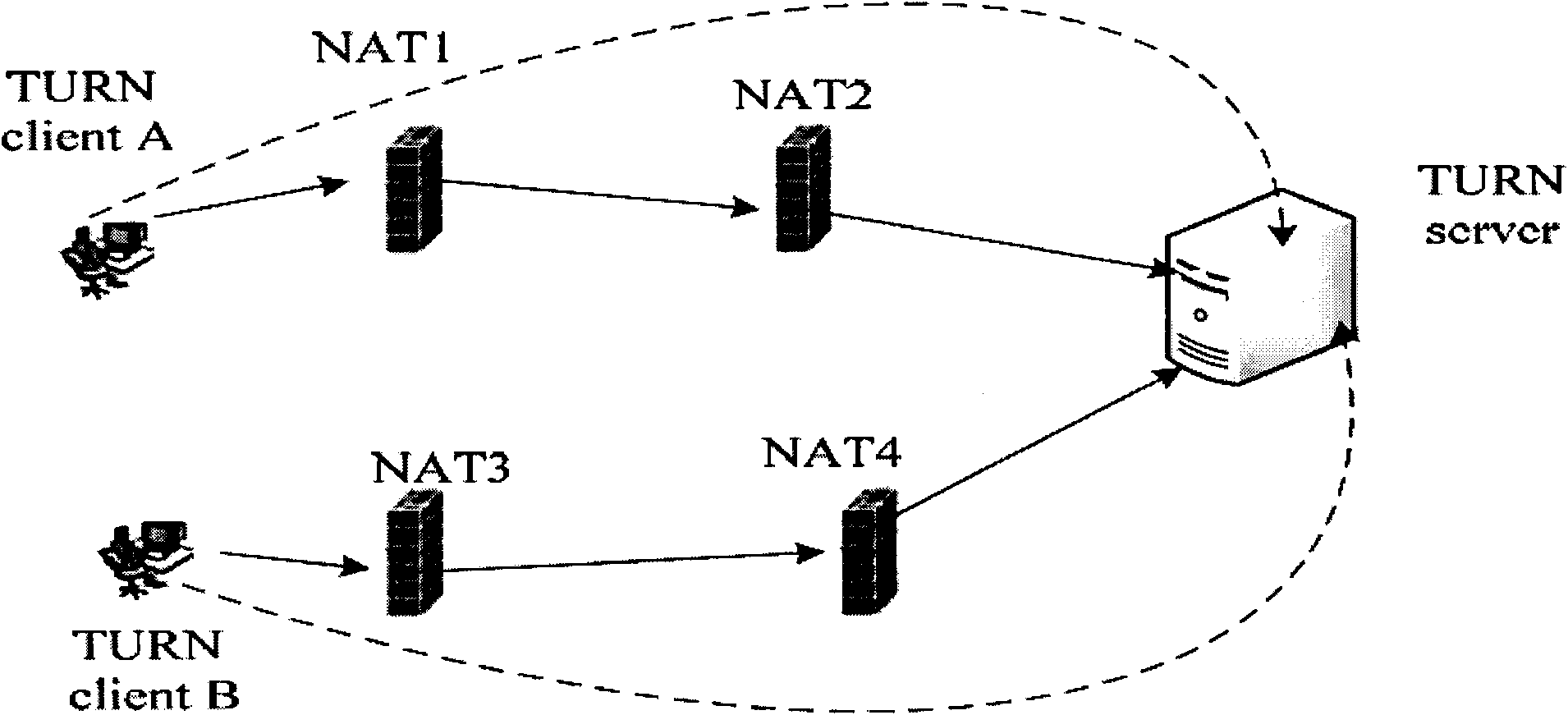
[0028] 4. For network nodes that cannot be realized by the above methods, the TURN method is used to realize private network traversal.
Embodiment 2
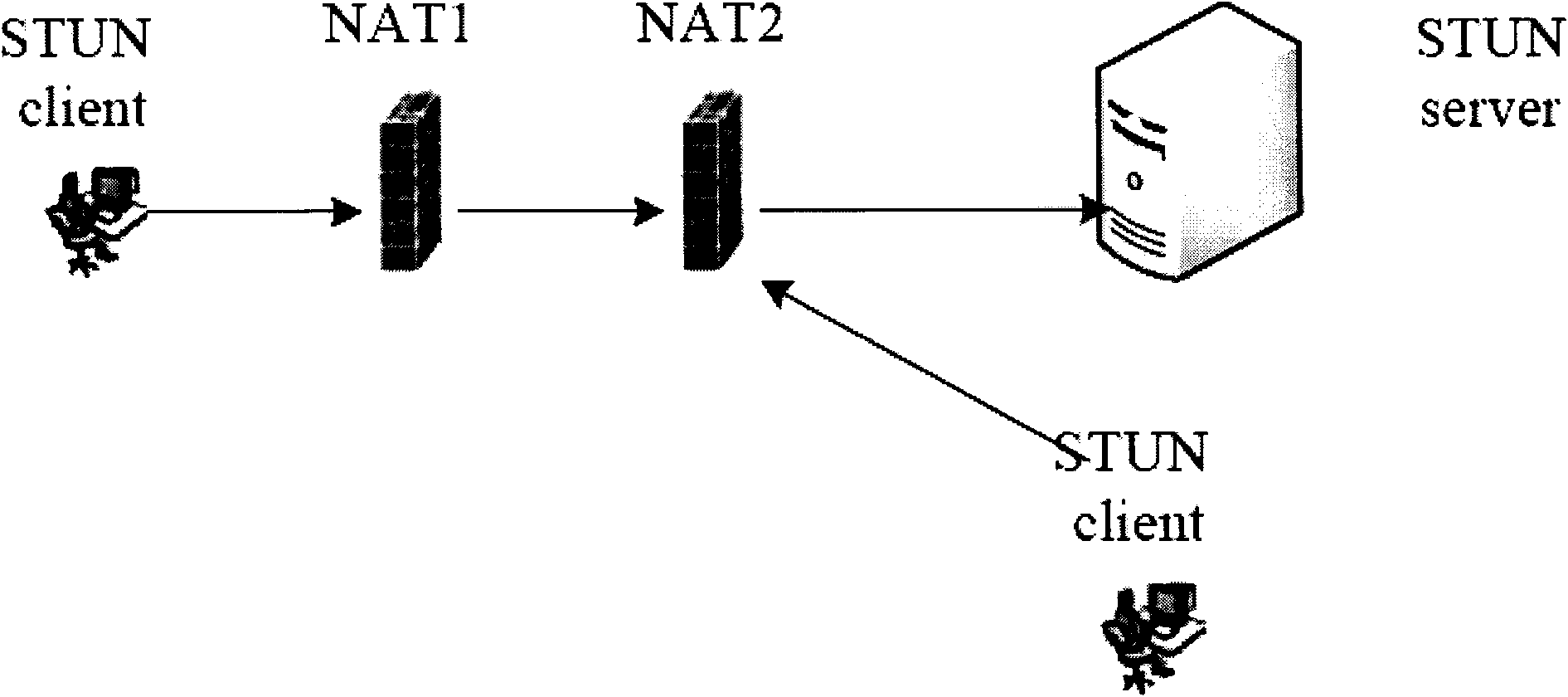
[0030] This embodiment provides a compound method for private network detection and traversal in a P2P network application system, such as image 3 As shown, the detailed steps of the method are:
[0031] Step 1, client node A checks whether the current gateway supports UPNP technology, if so, applies for a UPNP external network port, and sends an application to join the network to the global routing server B through this port.
[0032] Step 2, the global routing server B initiates a connection to client node A, and sends a handshake protocol; if the handshake is successful, it means that client node A is behind an effective UPNP gateway, and the inward address of client node A sending data is recorded by global routing server B, And determine that the inbound address is the external mapping address of client node A; other system nodes can actively communicate with client node A after obtaining the external mapping address of client node A through the global routing server B. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com