Method and system for automated information security evaluation
An information security and safety technology, applied in special data processing applications, instruments, electrical and digital data processing, etc., can solve problems such as error-prone, aggravating staff workload, and difficulty in scanning result data analysis in a comprehensive, objective, and complete manner. To achieve the effect of reducing labor costs, improving work efficiency and ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to make the objectives, technical solutions and advantages of the present invention clearer and clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
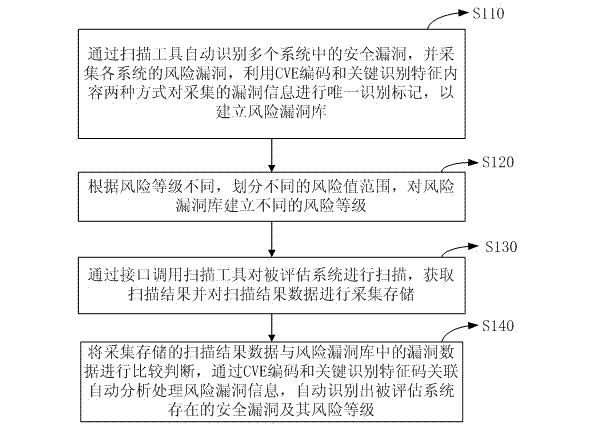
[0040] Such as figure 1 As shown, an automated information security assessment method provided by the present invention includes the following steps:
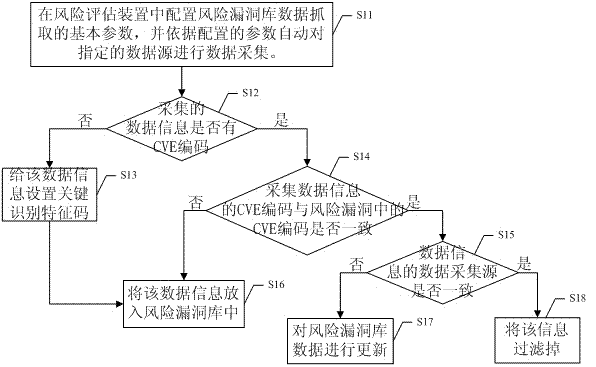
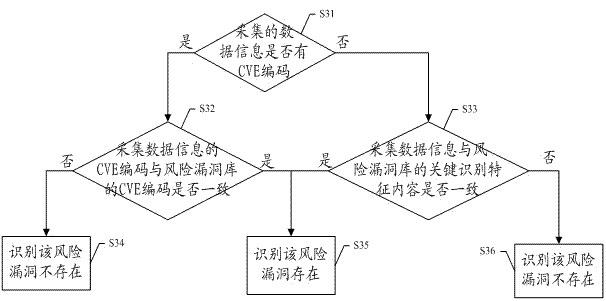
[0041] Step S110: Automatically identify security vulnerabilities in multiple systems through the scanning tool, and collect the risk vulnerabilities of each system, and use CVE (the full English name is "Common Vulnerabilities & Exposures", that is, public vulnerabilities and exposures) encoding and key identification feature content two In this way, the collected vulnerability information is uniquely identified and marked to establ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com