User card based online transaction method and system
A user card and user technology, applied in the network field, can solve problems such as payment difficulties, reduce transaction security, and user distribution, and achieve the effect of realizing personalization and intelligence, improving flexibility and convenience, and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
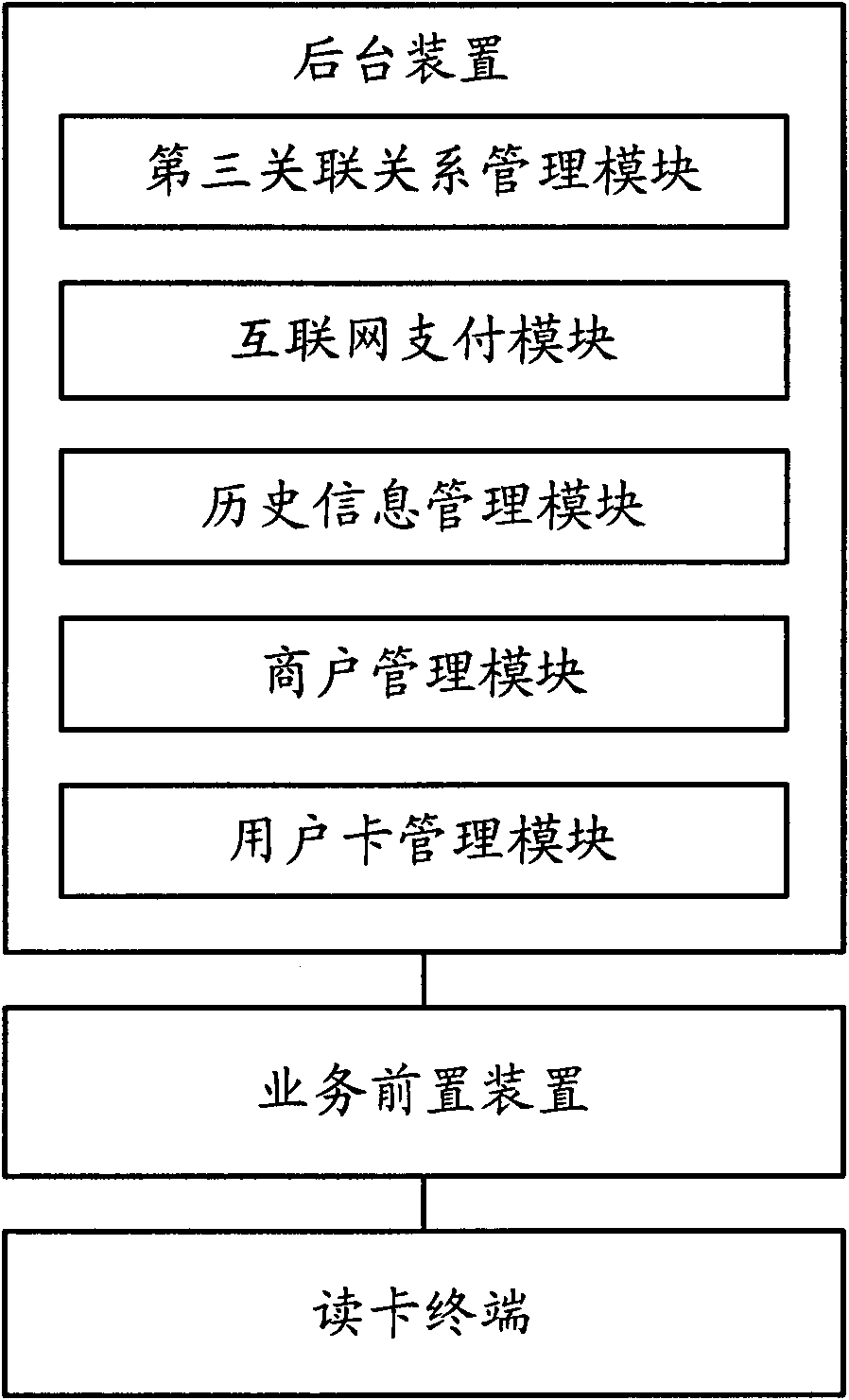
[0026] Such as figure 1 As shown, it is a schematic diagram of the structure of the online transaction system based on the user card in Embodiment 1 of the present application, including a card reader terminal, a business front-end device and a background device. in:
[0027] The card reading terminal is used to read the data stored in the user card, and is connected to the service front-end device through a wired network (such as a dial-up network) or a wireless network (such as GPRS, CDMA, TD-SCDMA, WIFI, etc.), and will read The data stored in the user card is sent to the service front-end device, and the information returned by the service front-end device is received and displayed. Specifically, when the user swipes the card at the card reading terminal, the card reading terminal can obtain the identification information of the user card, and send the identification information of the user card and the identification information of the card reading terminal to the servic...
Embodiment 2
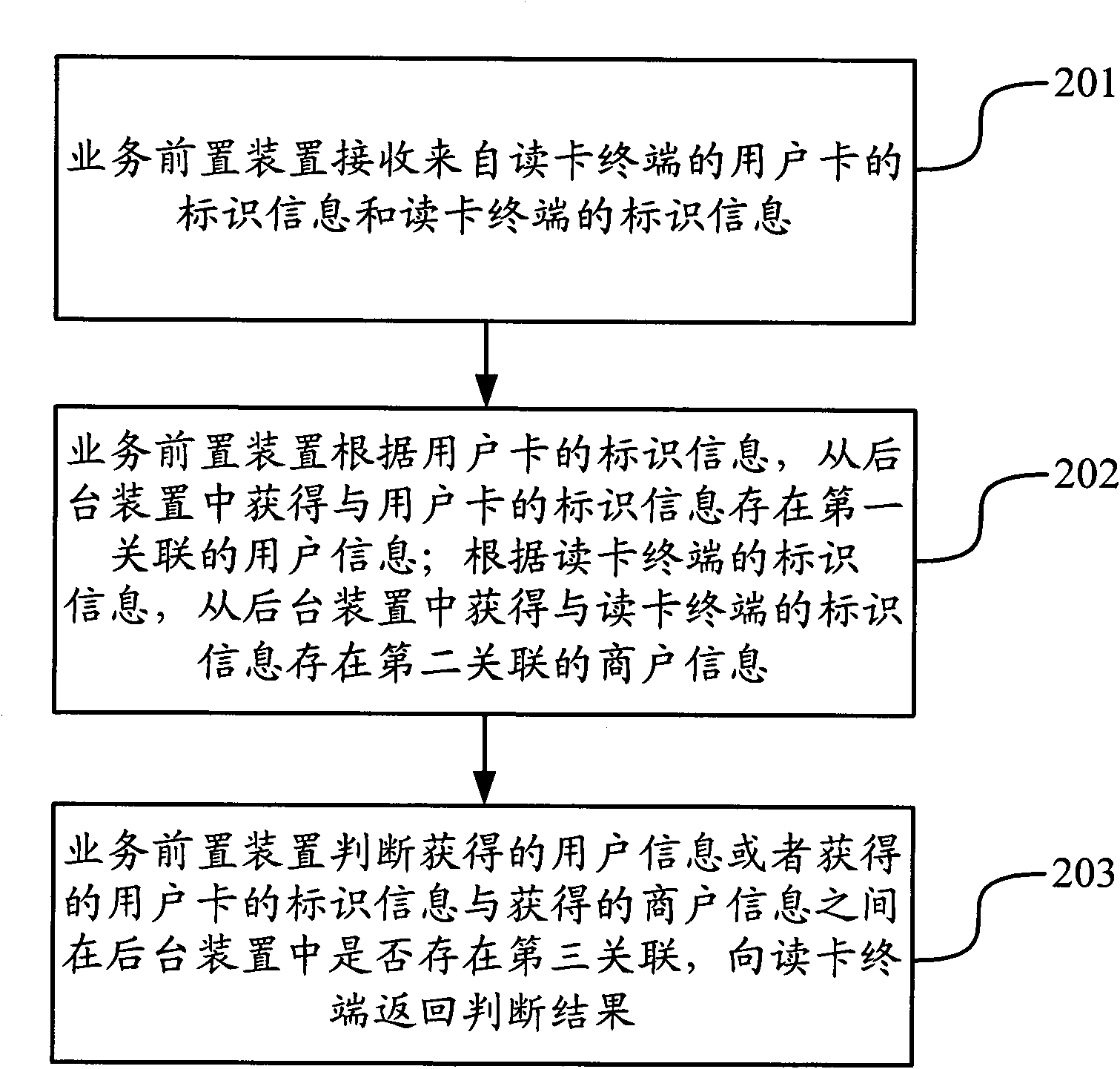
[0055] Based on the above system architecture, Embodiment 2 of the present application provides an online transaction method based on user cards, such as figure 2 shown, including the following steps:
[0056] In step 201, the service front-end device receives the identification information of the user card and the identification information of the card reading terminal from the card reading terminal.
[0057] Step 202, the front-end device of the service obtains the user information associated with the identification information of the user card from the background device according to the identification information of the user card; The second associated merchant information exists in the identification information.
[0058] Step 203, the service front-end device judges whether there is a third association between the obtained user information or the obtained user card identification information and the obtained merchant information in the background device, and returns the...
Embodiment 3
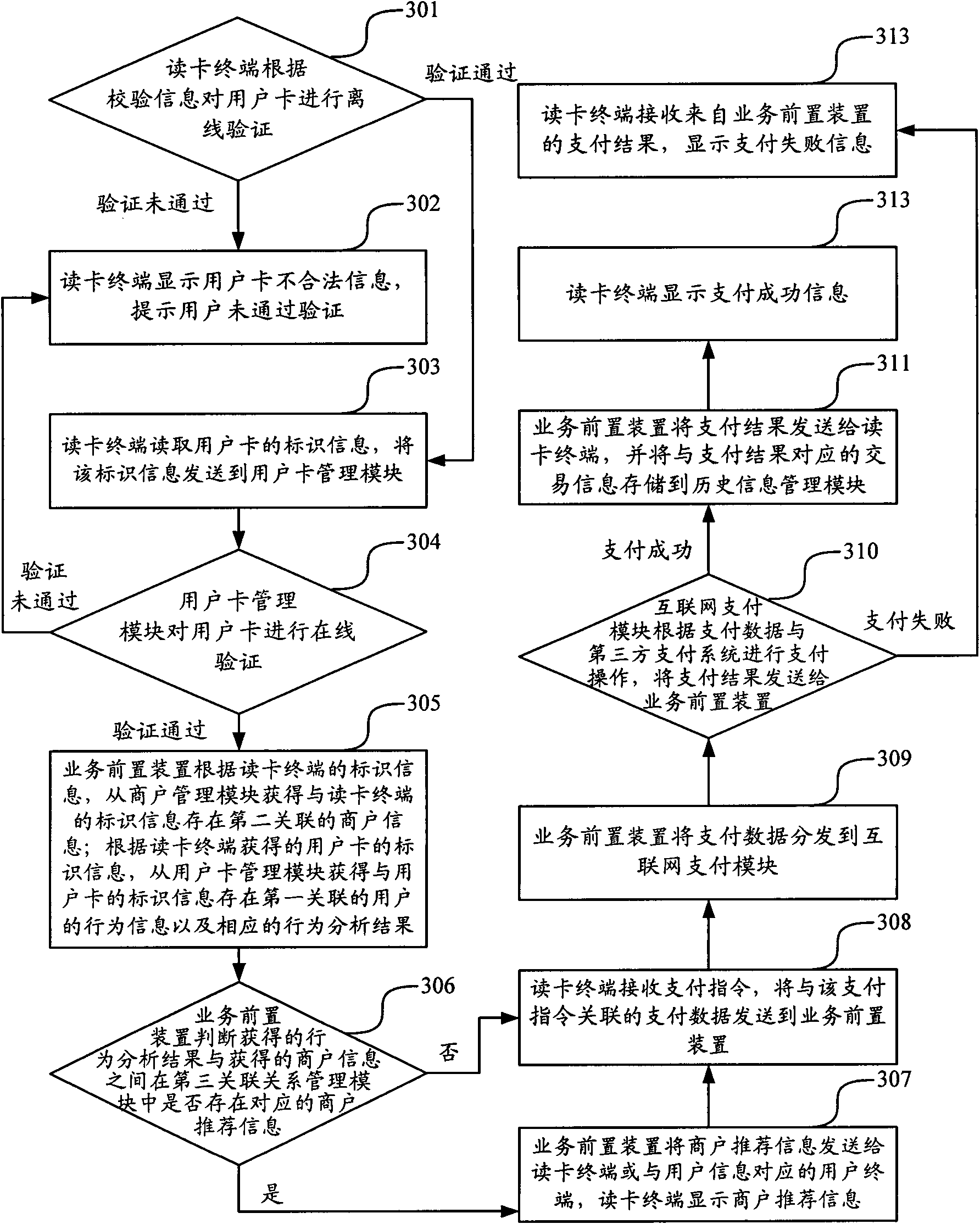
[0066] When merchant recommendation information is stored in the background device, the online transaction method based on the user card provided by Embodiment 3 of the present application, such as image 3 shown, including the following steps:
[0067] In step 301, the card reader terminal reads the verification information of the user card, and performs offline verification on the user card according to the verification information. If the offline verification passes, step 303 is executed; otherwise, step 302 is executed.
[0068] Wherein, the user card is used to store user identity information, and the user identity information may include identification information and verification information. The type of user card can be magnetic stripe card, contact IC card and non-contact card, etc., and the card reading terminal can read and write the information in the user card. When no user swipes the card, the card reader terminal can play the default system information. When t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com