System and method for remotely controlling mobile terminal
A technology for remote control systems and mobile terminals, applied in electrical components, wireless communication, network data management, etc., can solve the problems of data control of non-mobile terminals, easy data theft, inappropriate use of personal information, etc., to achieve protection Safe, avoid the effects of improper deletion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
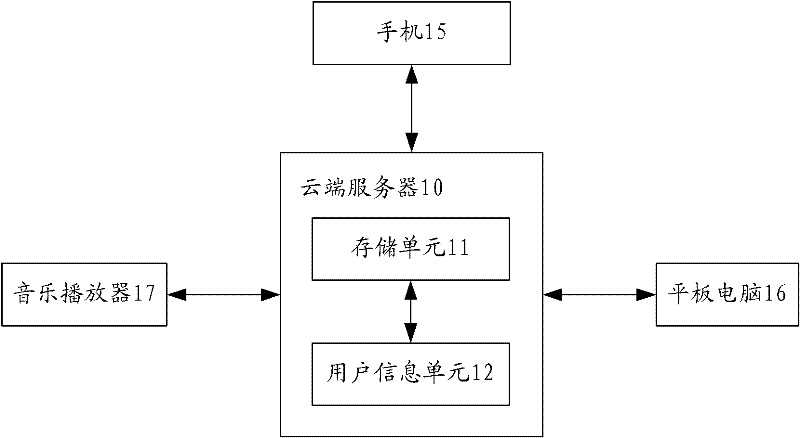
[0025] The mobile terminal control system of the present invention is used to remotely control mobile terminals, including mobile phones, tablet computers, and music players, so as to protect the data stored in the mobile terminal from being lost and prevent the data stored in the mobile terminal from being stolen.
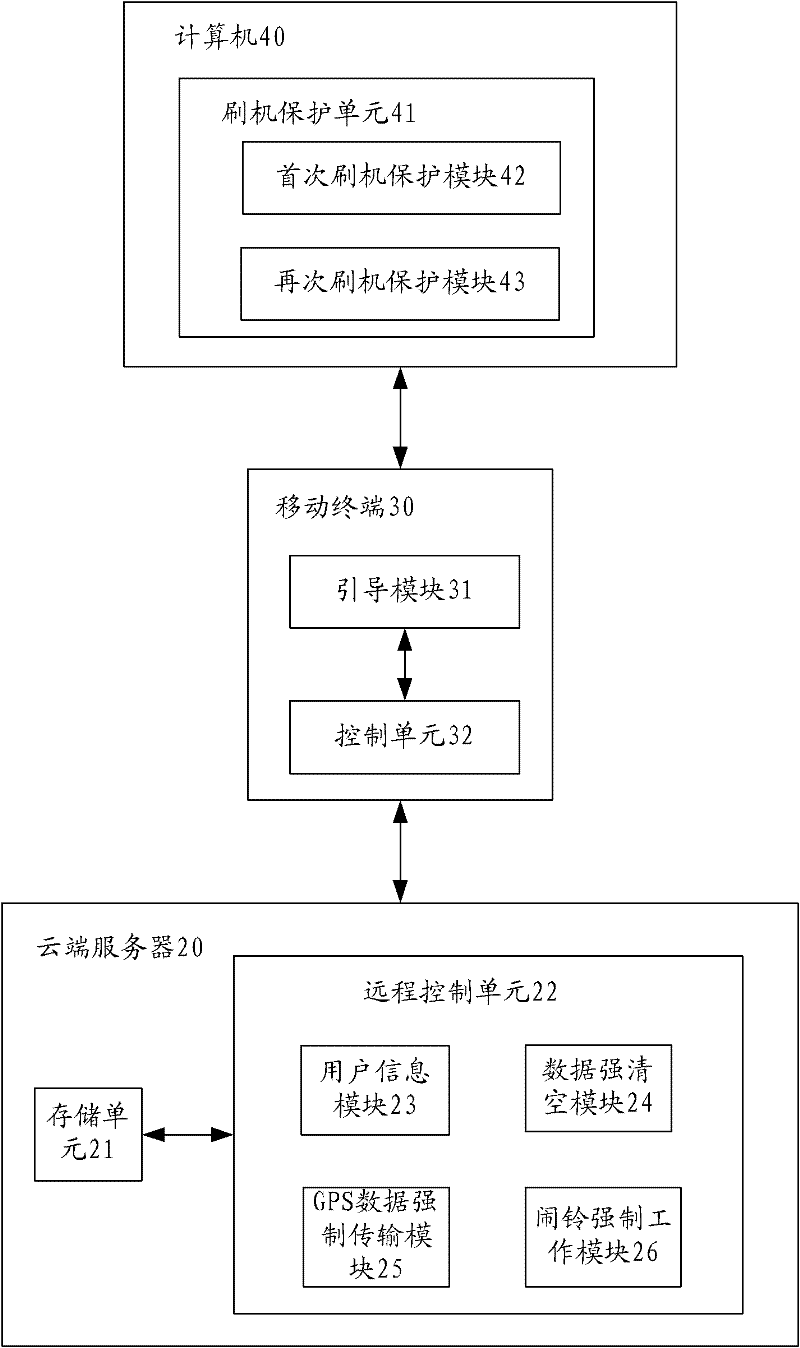
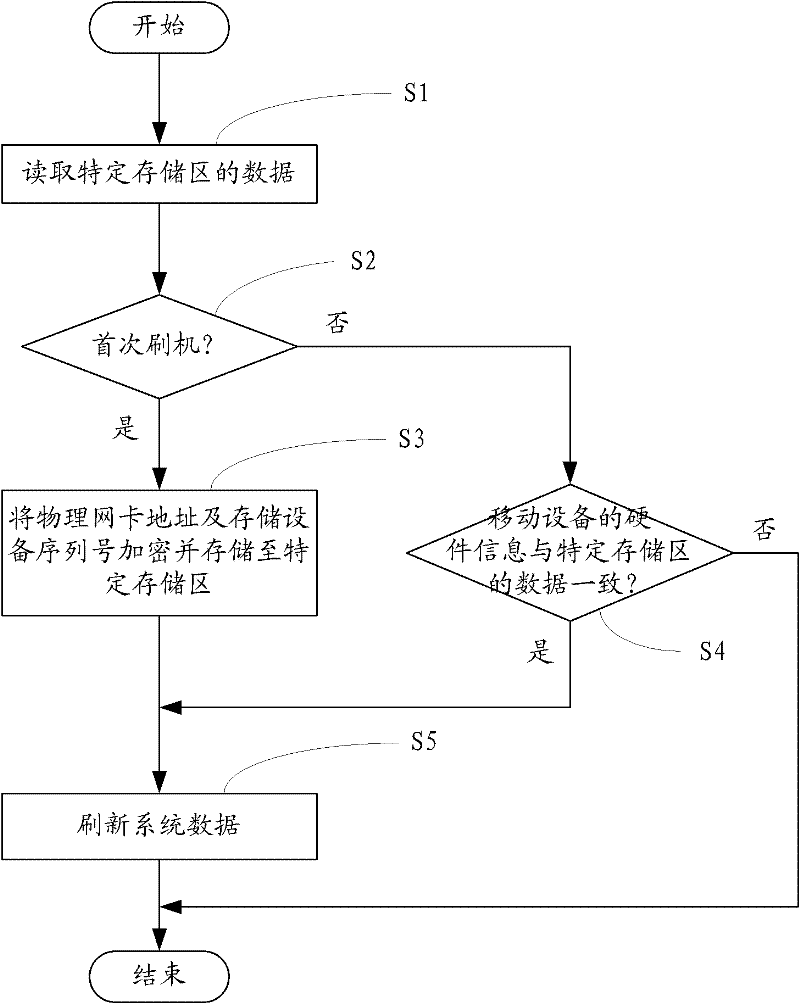
[0026] see figure 2 , the present embodiment has the remote control unit 22 installed in the cloud server 20 and the flashing protection unit 41 installed in the computer 40, wherein the flashing protection unit 41 has a flashing protection module 42 for the first time and a flashing protection module 43 again, and the remote control unit 22 A user information module 23, a data forced clearing module 24, a GPS data forced transmission module 25 and an alarm clock forced working module 26 are provided inside. Moreover, the cloud server 20 is also provided with a memory 21 for storing personal data uploaded by users.
[0027] The computer 40 can transmit data with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com