Access controlling method and device using virtualization
An access control and virtualization technology, applied in the field of virtualization, can solve the problems of high deployment cost, vulnerable to attack, poor performance, etc., achieve the effect of high forwarding performance, avoid attack risks, and save procurement costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
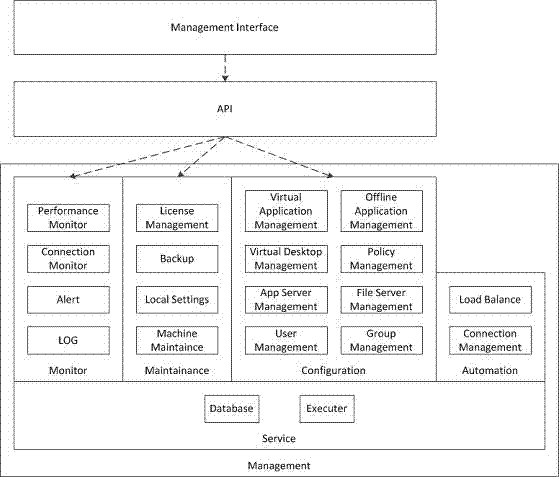
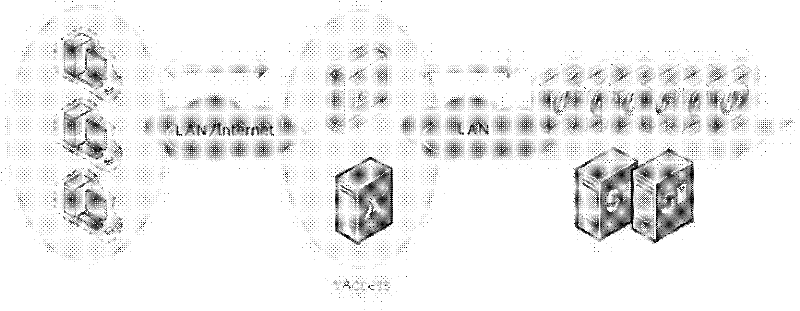
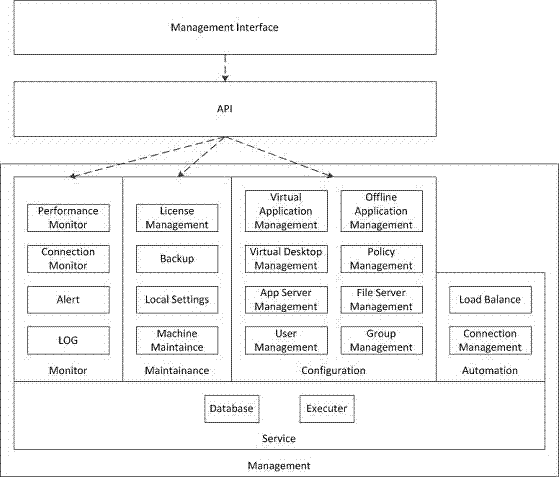
[0015] In the existing network environment, the access control software is usually installed on the application server (Windows Sever) as a Windows application program. The virtualization client plug-in on the user terminal side directly accesses the access control software running on the application server, and performs processing such as access control and virtualization protocol communication. However, there are many developers who are familiar with the Windows system, and there are many corresponding attackers. Therefore, the Windows system naturally faces higher security threats. In addition, the virtualization access control software as an application can also be installed on an independent Windows Server to perform virtualization access control. After the user is authenticated and authorized, he can directly access the desktop virtual machine through the client plug-in, and the protocol communication does not go through Virtualization access control software. In this ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com