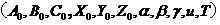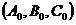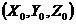Method for carrying out chaotic encryption based on particle travelling
An encryption method, chaotic encryption technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of continuous chaotic systems, discretized chaotic cryptographic systems, etc., and achieve the effect of being difficult to crack and strong confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The embodiments of the present invention will be described in further detail below with reference to the accompanying drawings.
[0030] Following figure 1 Take an example to describe the specific process of embedding information in the text of the document according to the present invention;
[0031] The particle-based nonlinear encryption method is composed of five parts: the encrypted information format conversion module, the information segmentation module processing module, the parameter coordinate conversion module, the nonlinear encryption module, and the encrypted information output module. The specific flow chart of the information encryption is described as follows:
[0032] Before the information is encrypted, first, in step S1, the encrypted information format conversion unit automatically reads the encrypted information, and automatically converts the encrypted information in any format into a binary format. Binary format is a general format for computer storage ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com