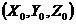Patents
Literature
34results about How to "One-way" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
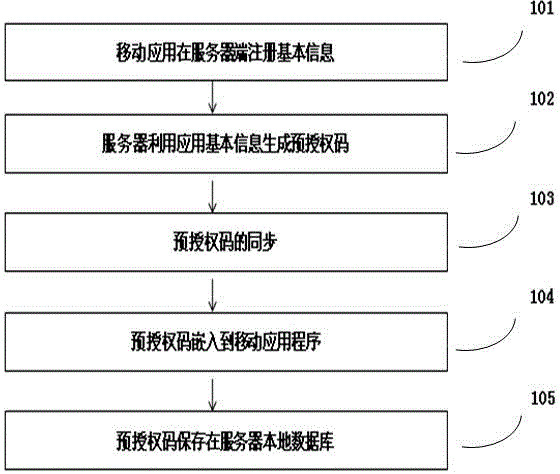
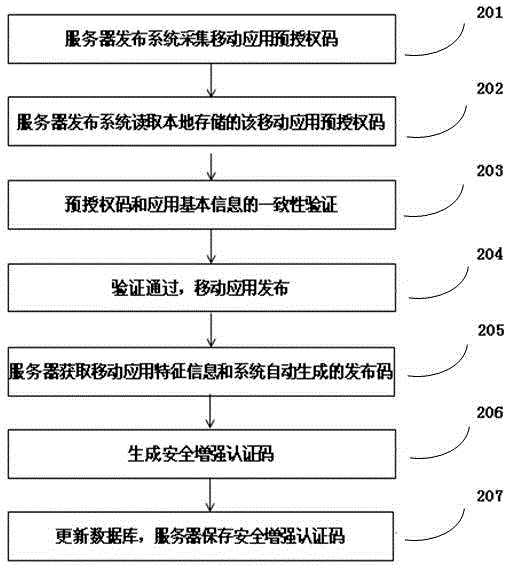
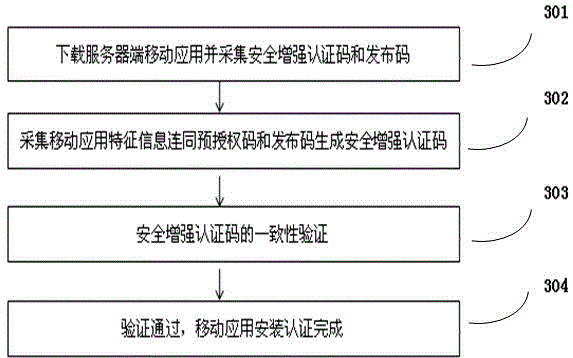
Security-enhanced authorizing and authenticating method of mobile application
ActiveCN104539634AUniqueness guaranteedOne-wayUser identity/authority verificationComputer security arrangementsEngineeringComputer security
The invention relates to a security-enhanced authorizing and authenticating method of mobile application. The security-enhanced authorizing and authenticating method of the mobile application, disclosed by the invention, comprises the following steps: registering, and acquiring basic information of the mobile application by a publishing system; pre-authorizing, generating a pre-authorizing code of the mobile application by utilizing the basic information, and embedding the pre-authorizing code in a mobile application program; performing enhanced publishing and authorizing, automatically detecting whether the pre-authorizing code and the basic information of the mobile application are correct or not by the publishing system, if so, automatically publishing, collecting practical feature information and a publishing code of the mobile application, and generating a security-enhanced authenticating code with the pre-authorizing code; reliably installing, acquiring the practical feature information, the pre-authorizing code and the publishing code of the mobile application while installing the mobile application so as to generate the security-enhanced authenticating code, and authenticating reliable installation; and reliably starting, in the event of starting the mobile application every time, detecting whether the pre-authorizing code is correct, and starting if the pre-authorizing code is correct. The invention provides a method for detecting the security reliability of the mobile application; and therefore, the problem that user information is stolen as the mobile application is maliciously tampered is effectively avoided.
Owner:北京成众志科技有限公司
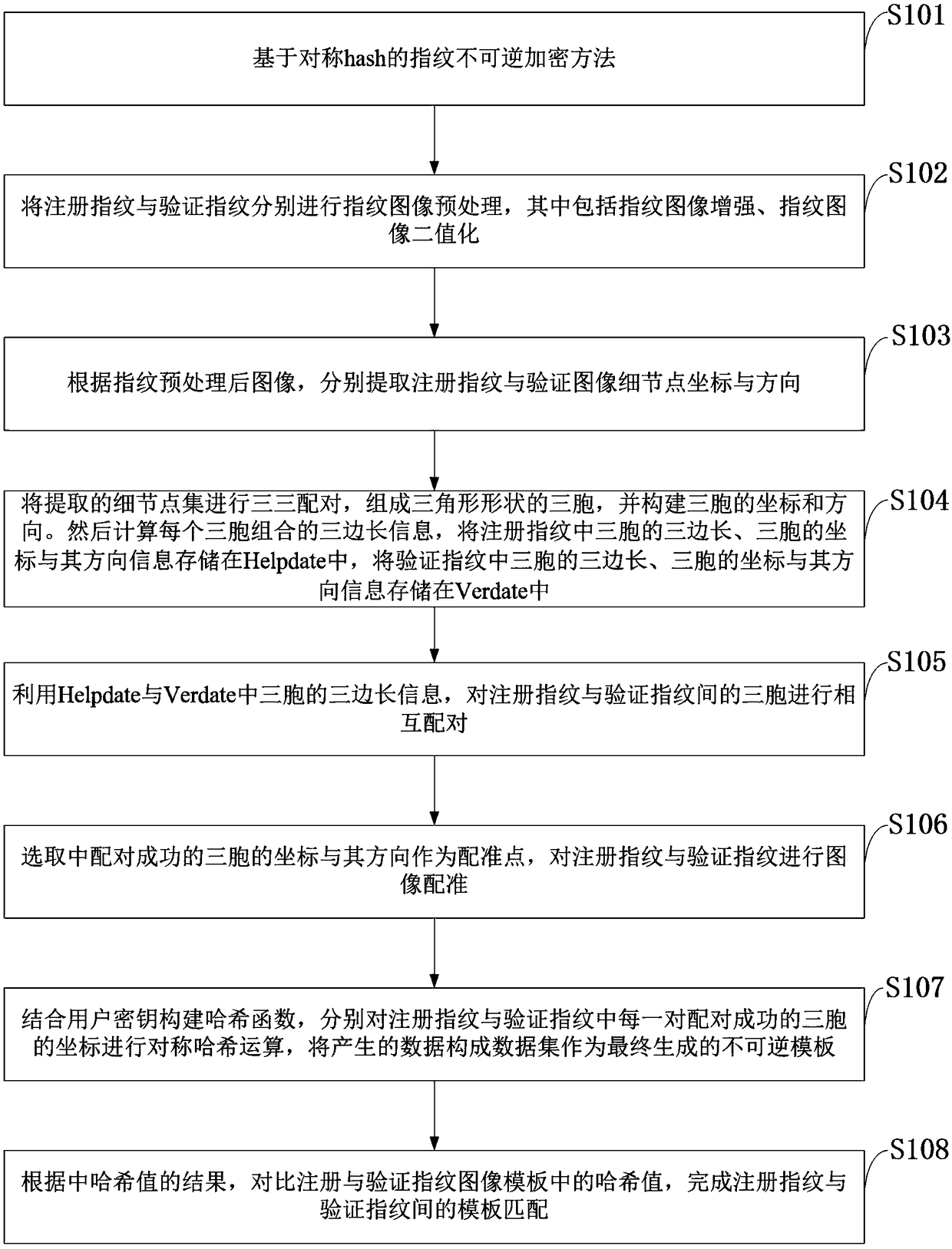
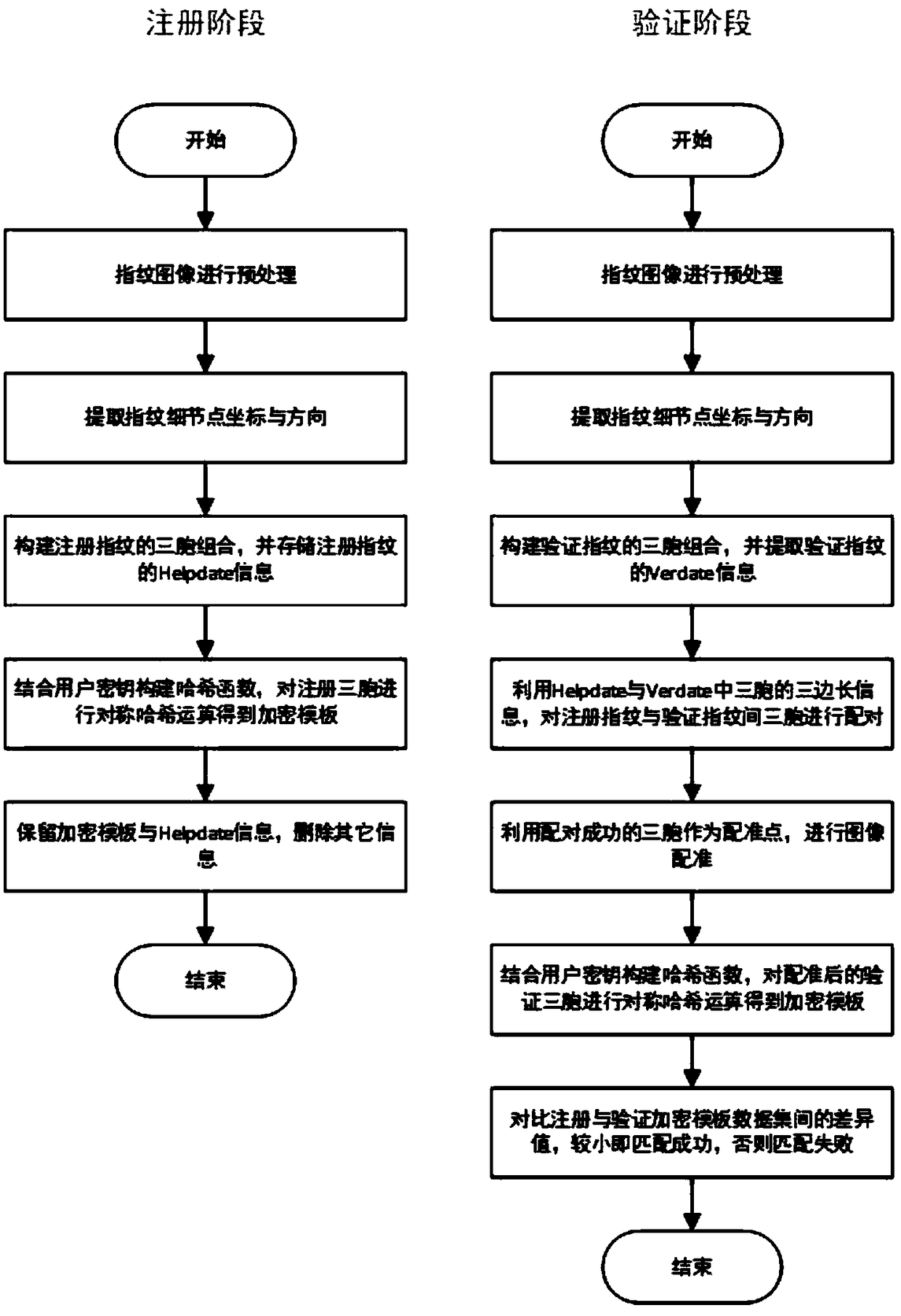
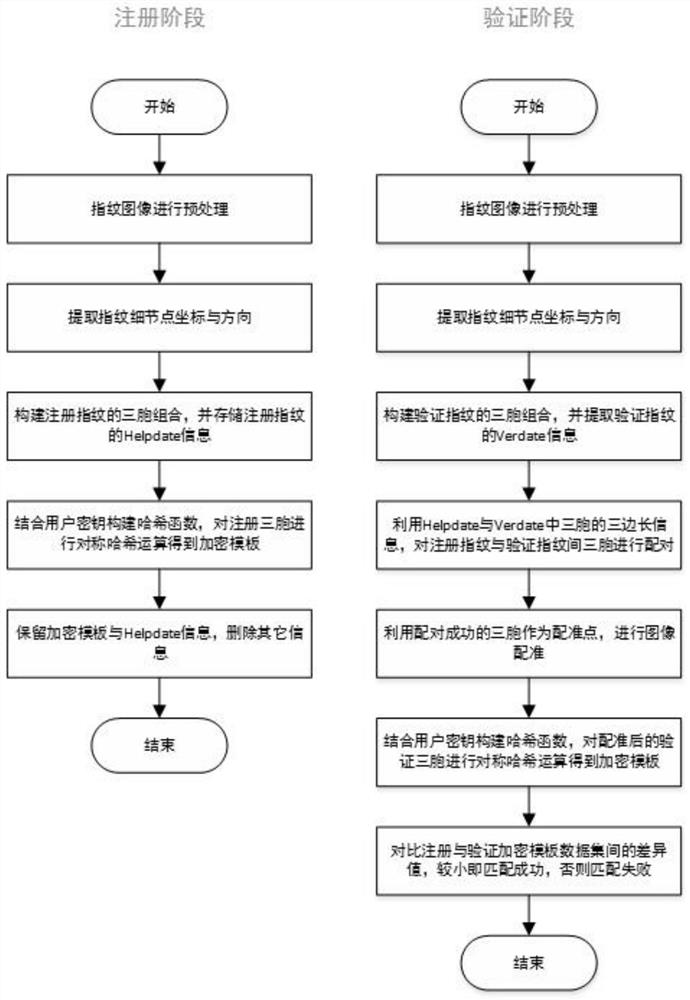
Symmetric hash based irreversible fingerprint template encryption method
ActiveCN108960039AProtect the original fingerprint informationProtect fingerprint information securityMatching and classificationFingerprintCoefficient matrix
The invention discloses a symmetric hash based irreversible fingerprint template encryption method, and belongs to the technical field of fingerprint identification and encryption fusion in mode identification. A symmetric hash function is combined with a sine cosine function to ensure the irreversibility of hash operation strictly and improve the security of the whole encryption algorithm. The number of equation sets of the constructed hash function is lower than that of input, namely, a rank of a inhomogeneous equation set coefficient matrix equals that of an augmented matrix and is lower than the number of the equation sets, the equation sets include infinite solutions theoretically, and input data information cannot be obtained by an inversion method. In addition, output of the sine cosine function corresponds to the characteristic of infinite multiple input, so that the irreversibility of the method is further improved. An original fingerprint of a user cannot be obtained by inversion even if an attacker steals a secret key and template of the user. In the process of hash operation, a secret key manner of the user is combined in a simple and more efficient way, and the cancellation performance is higher.
Owner:XIDIAN UNIV
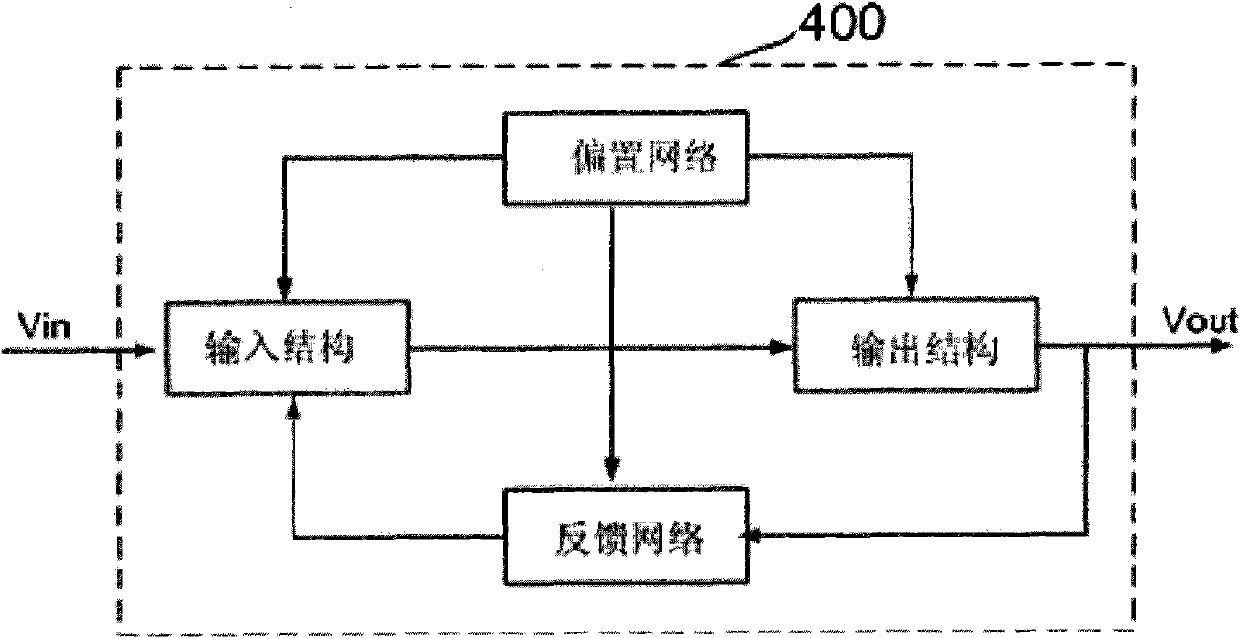
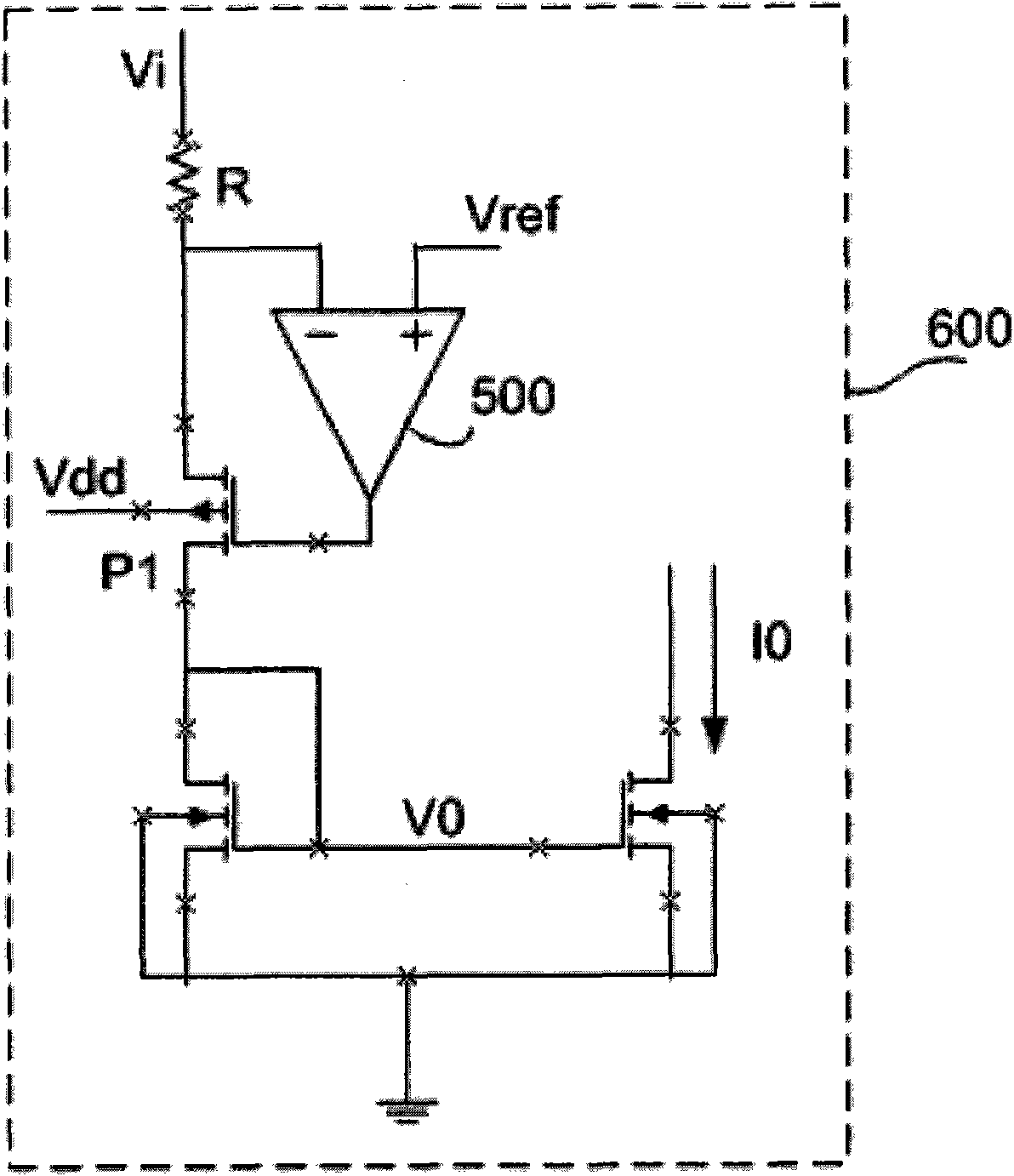
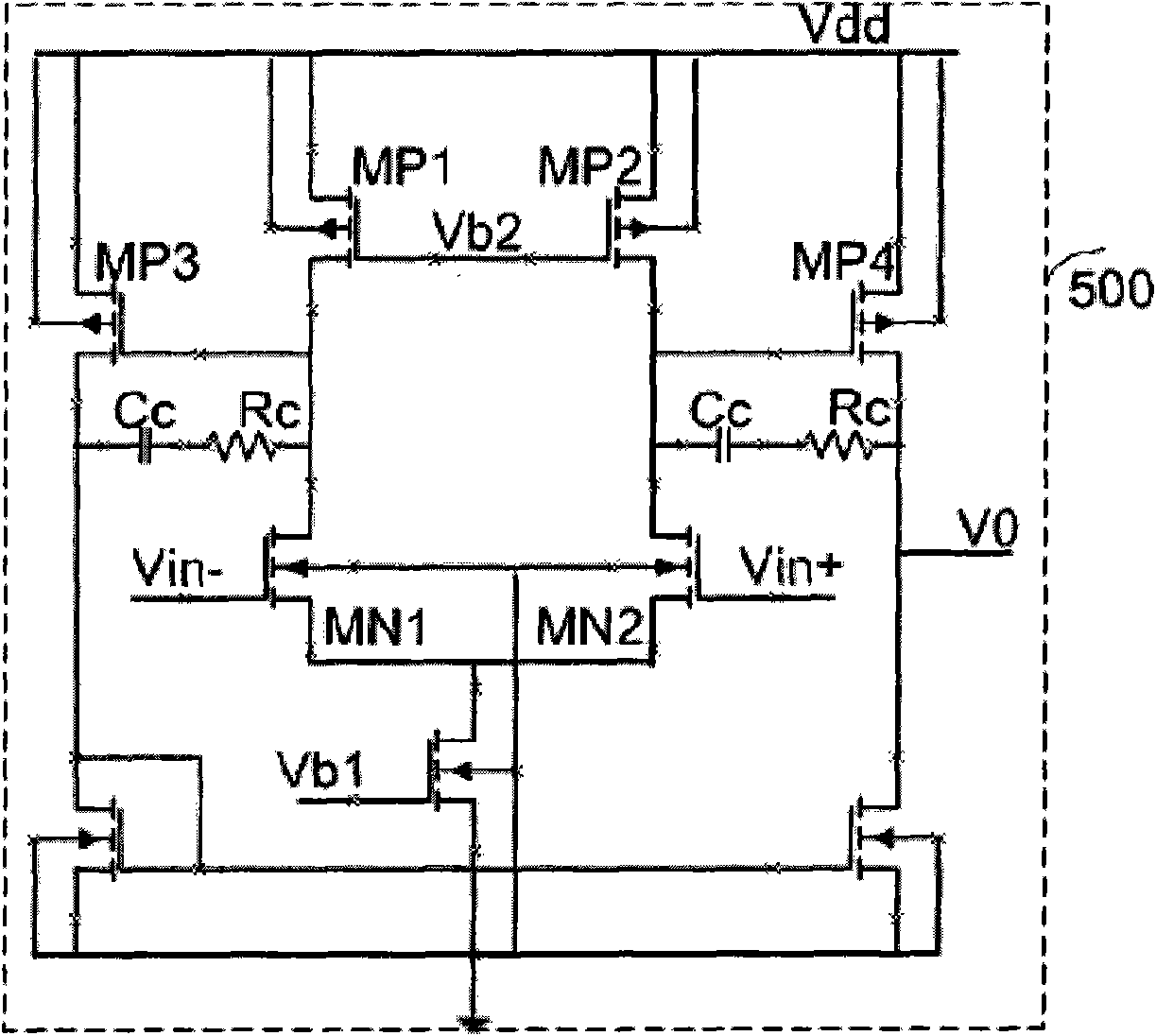
Operational amplifier
ActiveCN102570989AOne-wayGood linear transconductanceAmplifier modifications to reduce non-linear distortionDifferential amplifiersPower flowAudio power amplifier
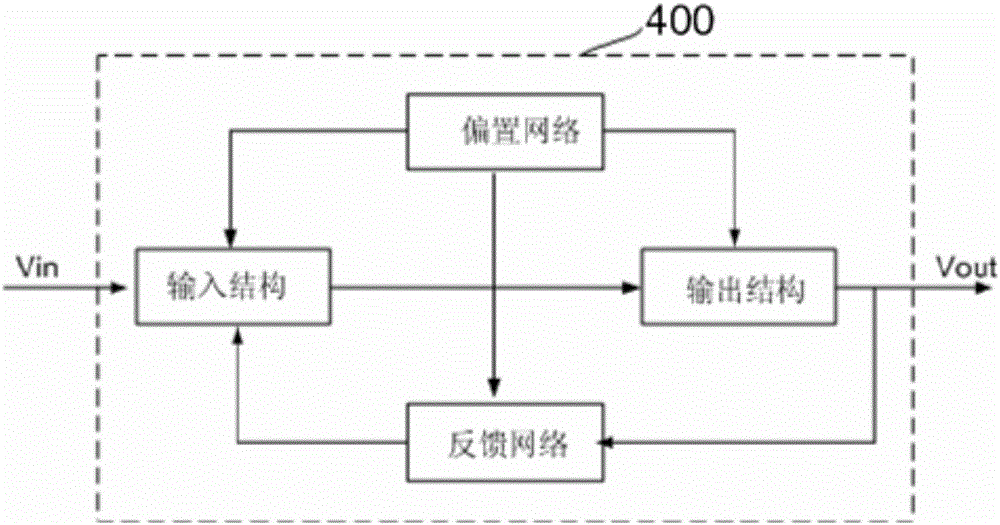
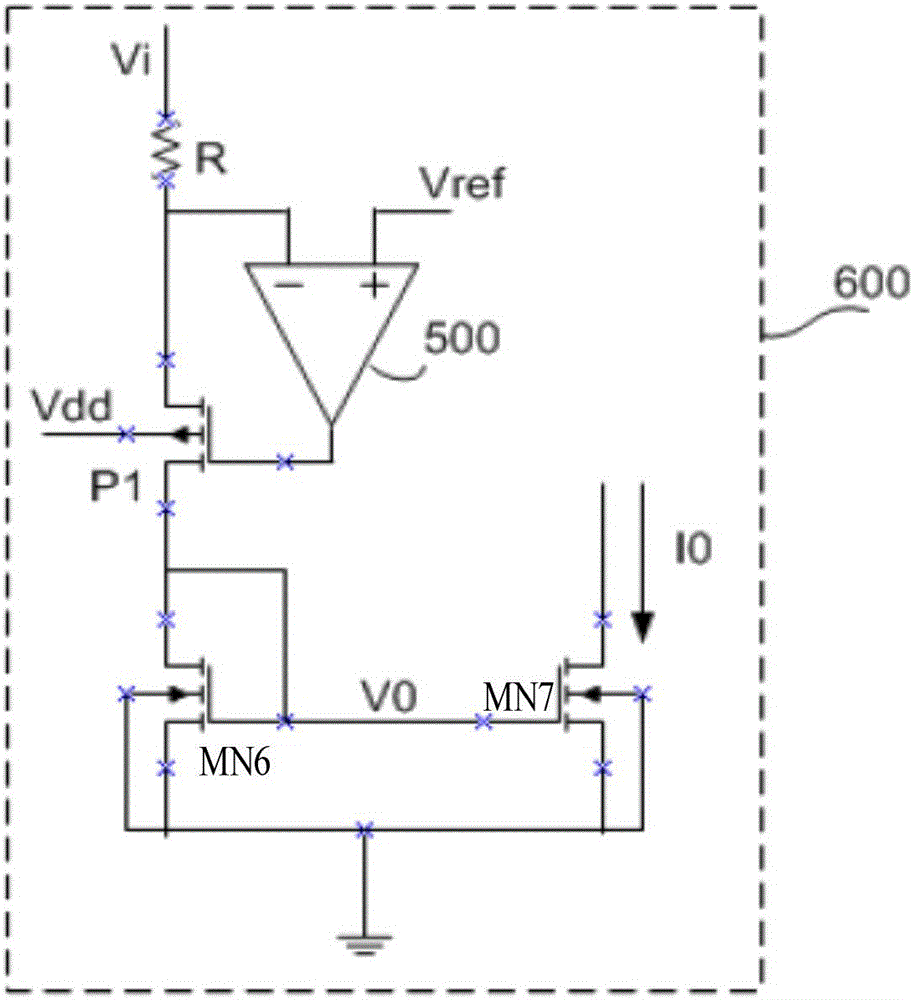
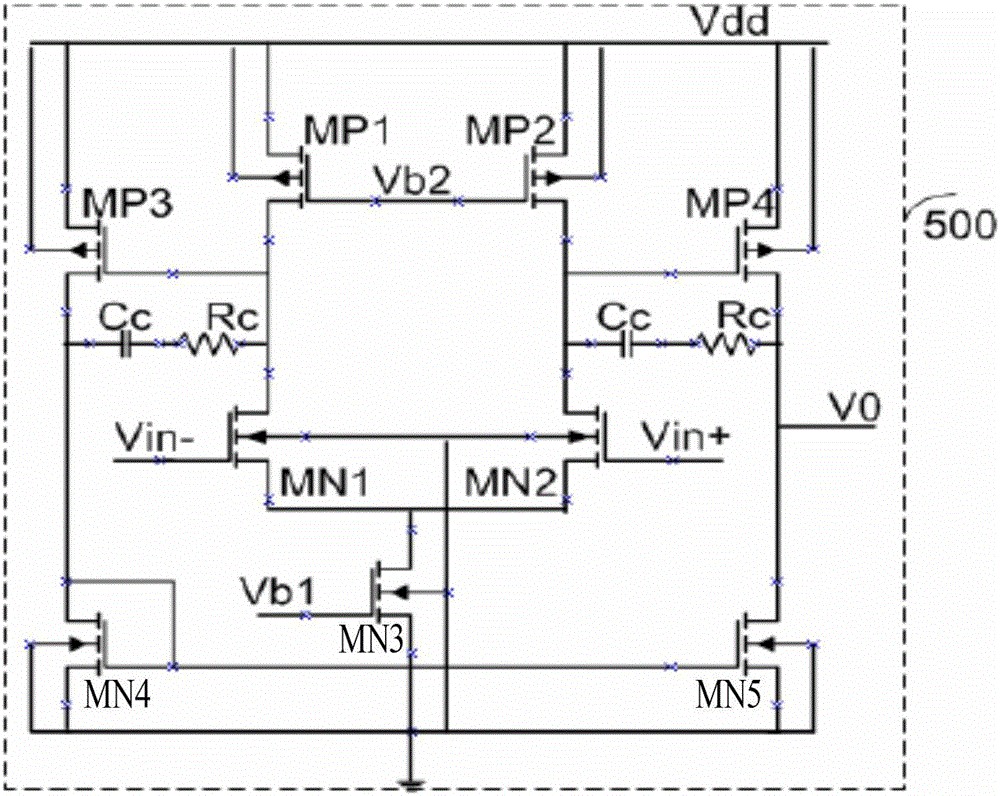
The invention provides an operational amplifier. The operational amplifier is characterized by comprising an input structure, a feedback network, an output structure and a bias network, wherein the input structure comprises an NMOS (N-channel metal oxide semiconductor) input operational amplifying circuit and a PMOS (P-channel metal oxide semiconductor) input operational amplifying circuit; the feedback network comprises an NMOS feedback loop connected with the NMOS input operational amplifying circuit and a PMOS feedback loop connected with the PMOS input operational amplifying circuit; the NMOS feedback loop and the PMOS feedback loop are used for ensuring the current of transistors to depend on the input voltage and the input end resistance under the condition that the input voltage Vi is greater or smaller than the reference voltage Vref; the output structure is used for amplifying signals transmitted by the input structure; and the bias network is used for supplying power to the input structure, the output structure and the feedback network simultaneously. The operational amplifier has the following beneficial effects: the reference voltage is set and the operational amplifier feedback loops with high gains are adopted; the current in the transistors has unipolarity, so good linear transconductance can be obtained; and meanwhile, a large dynamic voltage input range (from the ground to the power voltage) is realized.
Owner:CSMC TECH FAB2 CO LTD
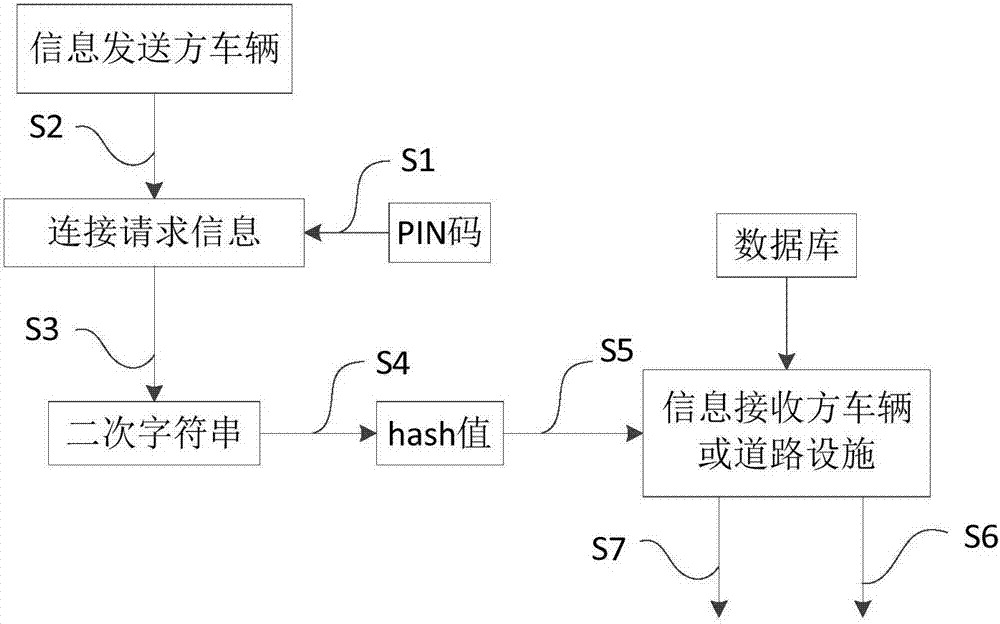
Vehicle infrastructure cooperative security communication method based on hash encryption
ActiveCN107046529AUniqueness guaranteedEasy to controlEncryption apparatus with shift registers/memoriesSecure communicationInformation seeking
The invention relates to a vehicle infrastructure cooperative security communication method based on hash encryption. The method comprises the following steps: step 1), mixing connection request information and a PIN code into a secondary character string by an information sender, wherein the PIN code is a unique identification code corresponding to the information sender; step 2), performing hash encryption on the secondary character string, and generating a corresponding hash value; and step 3), maintaining a database that stores multiple hash values by an information receiver, after receiving the hash value in step 2) by the information receiver, traversing to find the database, and judging whether the received hash value is valid; if yes, then establishing a secure communication connection with the information sender; otherwise, refusing the connection. Compared with the prior art, the vehicle infrastructure cooperative security communication method based on the hash encryption provided by the invention has the advantages of being high in security, and capable of realizing access control and so on.
Owner:TONGJI UNIV
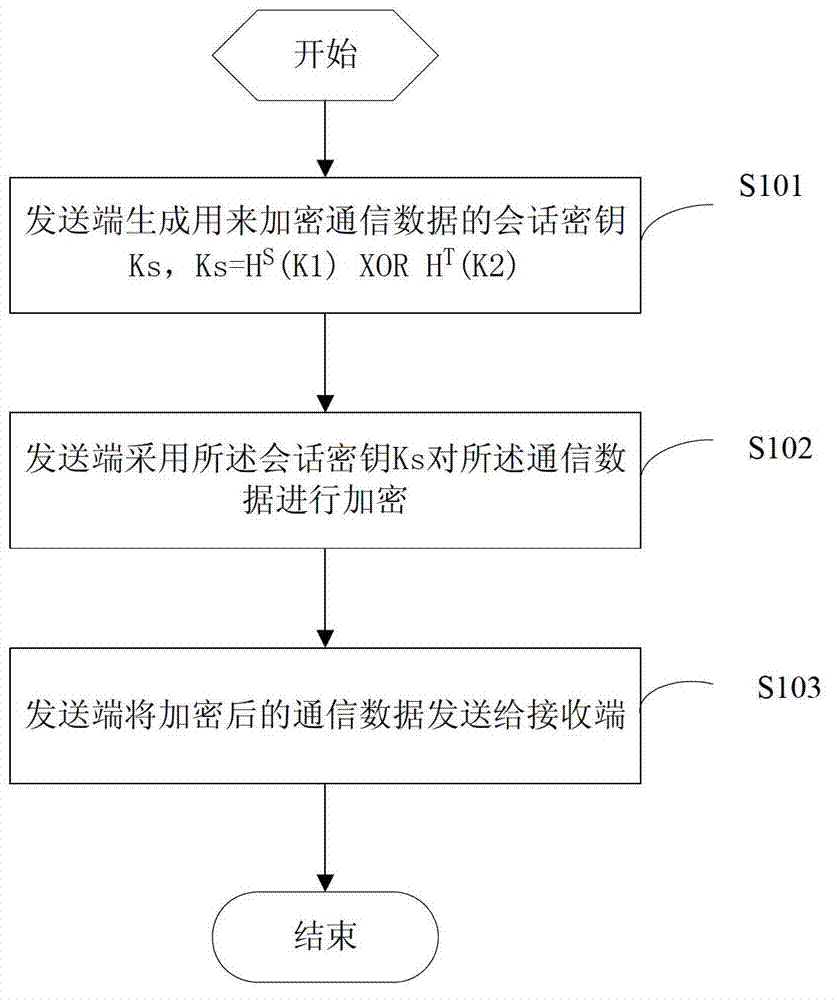
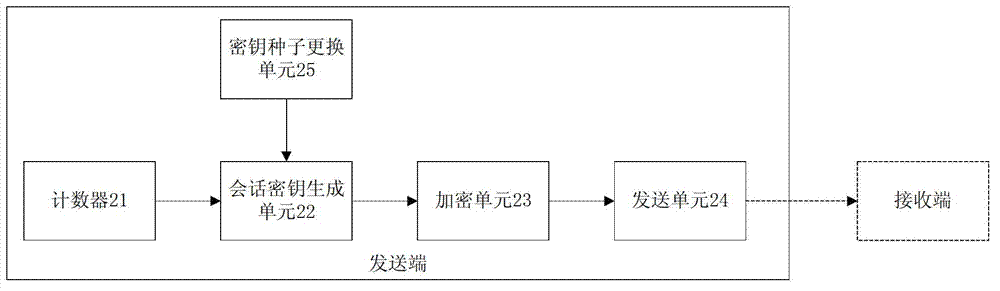
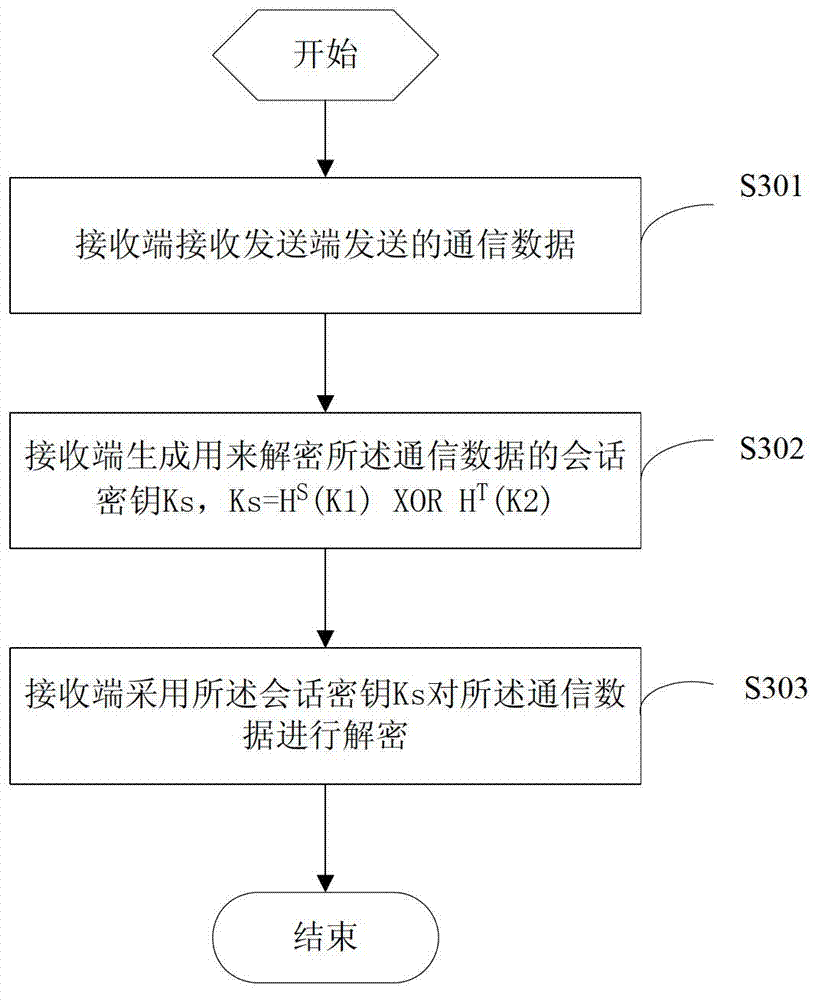
Dynamic secret key based data communication method, transmitting end and receiving end
InactiveCN103036675AOne-wayForward secureKey distribution for secure communicationSession keyShared secret
The invention discloses a dynamic secret key based data communication method, a transmitting end and a receiving end, wherein a transmitting end method comprises the following steps: the transmitting end generates a session key Ks used for encryption of communication data, Ks=HS (K1) * ORHT(K2), wherein the S is the value of a counter in the transmitting end, the initial value of the S is 1, S+T=n, and the value of the counter increases by 1 whenever a session is performed between the transmitting end and the receiving end, K1 and K2 are two parts divided from a secret key seed K, the length of the K1 is the same as the length of the K2, and the secret key seed K is a shared secret key preset for the receiving end and the transmitting end; the transmitting end encrypts the communication data through the session key Ks; and the transmitting end sends the encrypted communication data to the receiving end. According to the dynamic secret key based data communication method, the transmitting end and the receiving end, the forward security and the backward security of the session key are achieved, and therefore the security data communication is guaranteed; and the dynamic variation calculated amount of the session key is small, and the dynamic secret key based data communication method is easy to achieve.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Spinning machine pan head capable of preventing thread disorder
InactiveCN112125069AOne-wayConvenient to control the rotation speedFilament handlingGear wheelEngineering
The invention discloses a spinning machine pan head capable of preventing thread disorder. In the use process of an existing pan head, due to the fact that the rotating speed is not easy to control when the pan head rotates, the rotation has inertia, and the phenomenon of reverse rotation can occur under the action of external force, so that thread winding disorder is easily caused. In view of thetechnical problem, the invention provides the following scheme that the spinning machine pan head comprises a pan sheet and a pan core, wherein the pan sheet is connected with the pan core through abearing; a clamping groove is formed in the outer wall of one side of the pan sheet, and a gear disk is fixed to one end of the pan core through a screw; a one-way rotating mechanism is arranged on the outer wall of one side of the pan sheet, and a sliding groove is formed in the outer wall of one side of the pan sheet; and a sliding block is connected to the inner wall of the sliding groove in asliding mode. By the arrangement of the gear disk, a short shaft, a limiting plate, a limiting spring and a base block, the limiting plate abuts against the gear disk under the action of the limitingspring, so that the gear disk has unidirectionality along with transmission of the pan core, the rotating speed of the pan head is conveniently controlled, and thread disorder is avoided.
Owner:尹冬岩
Multi-signature method and apparatus
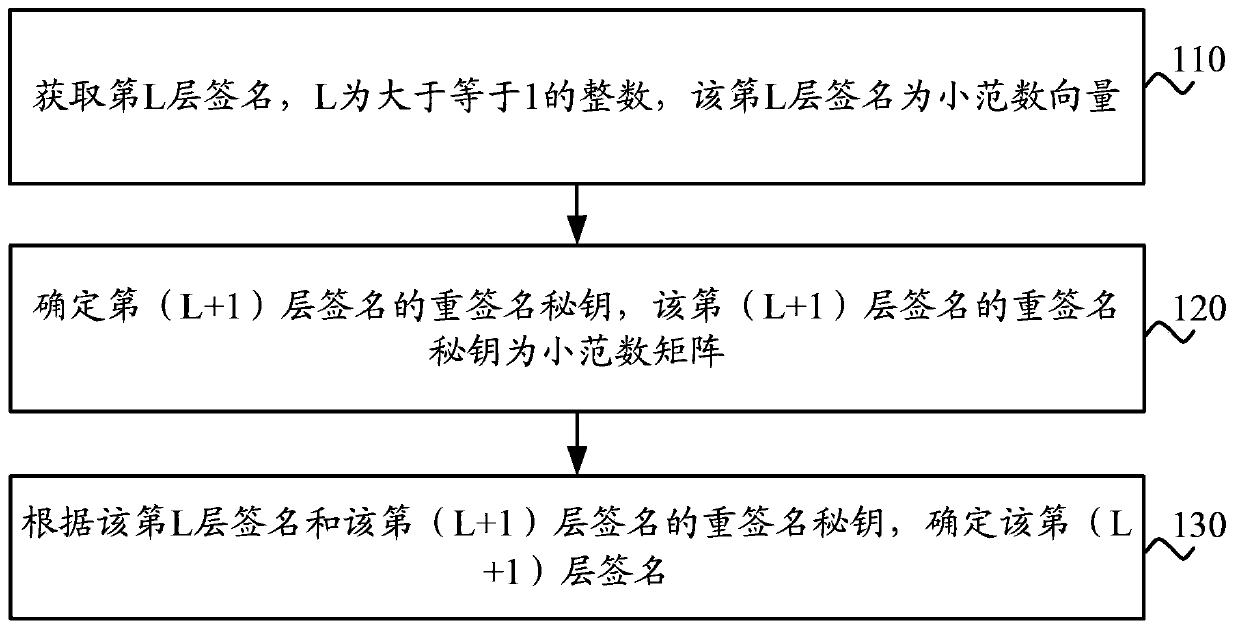
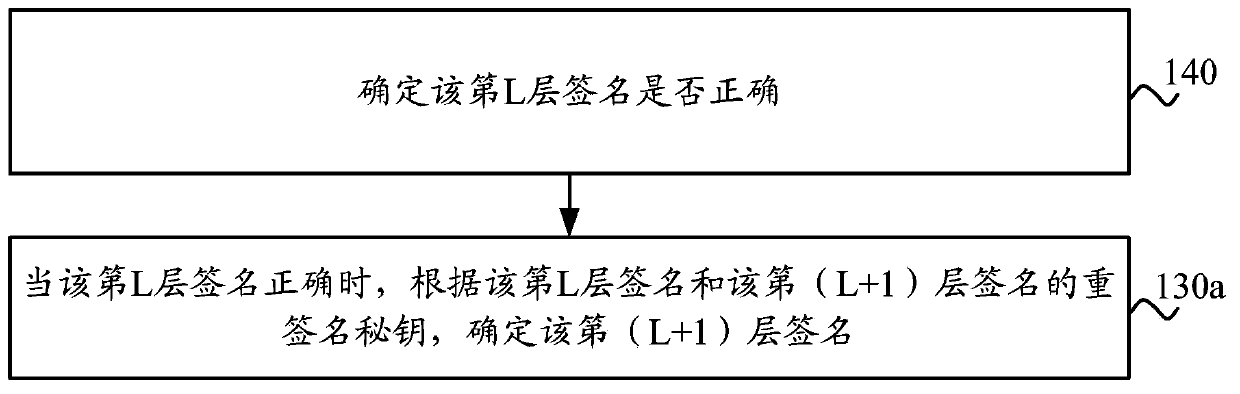
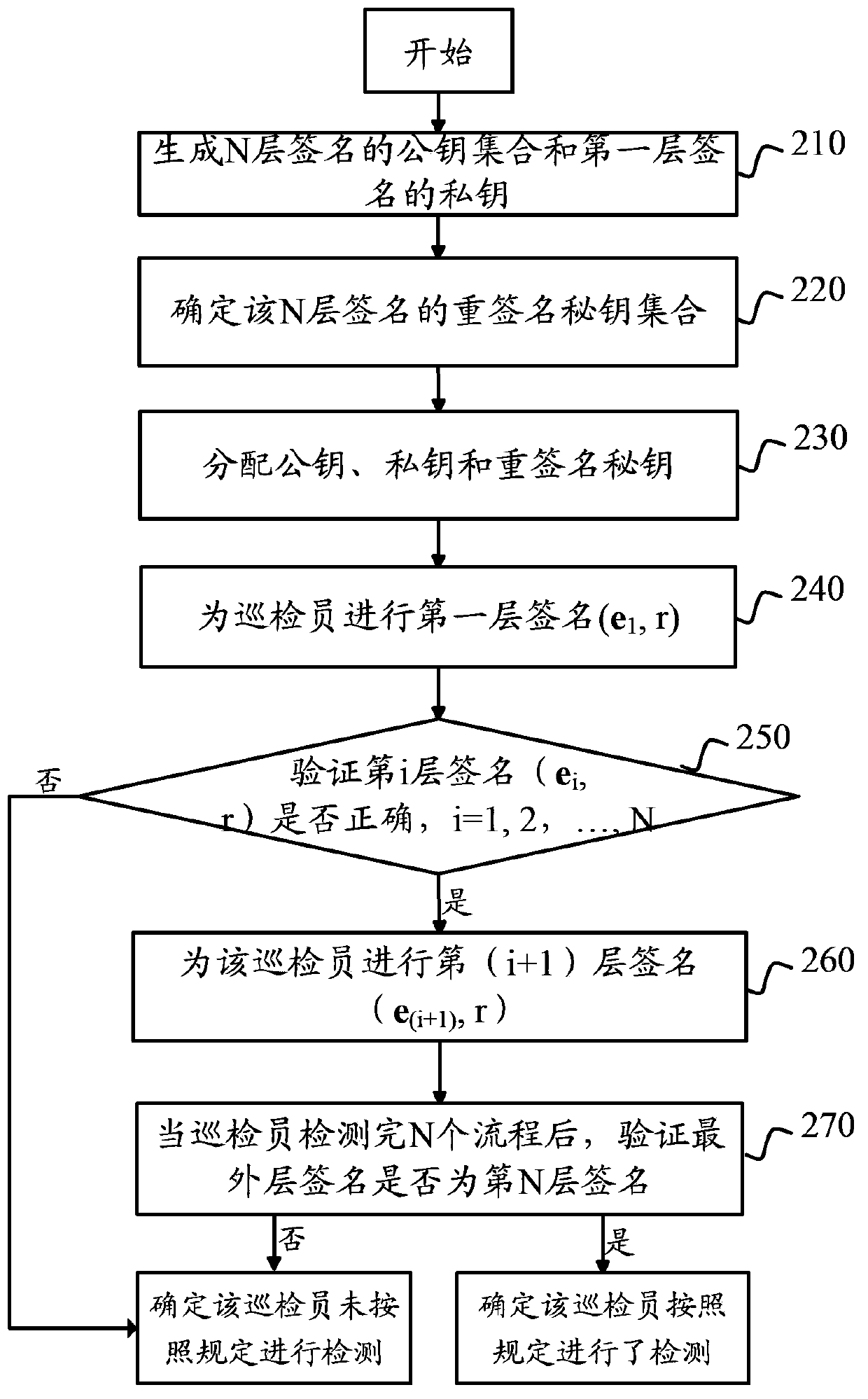
InactiveCN104184584AImprove securityOne-wayUser identity/authority verificationAlgorithmTheoretical computer science
The invention discloses a multi-signature method and apparatus. The method comprises the following steps that: a signature at an Lth layer is obtained, wherein the L is an integer that is larger than or equal to 1 and the signature at the Lth layer is a small norm vector; a multi-signature secret key of a signature at a (L+1)th layer is determined, wherein the multi-signature secret key of the signature at the (L+1)th layer is a small norm matrix; and according to the signature at the Lth layer and the multi-signature secret key of the signature, a signature of the (L+1)th layer is determined. According to the multi-signature method and apparatus provided by the embodiment of the invention, on the basis of the small integer solution (SIS) difficulty problem at the lattice, the signature and the multi-signature unit are set as the small norm vectors at the lattice and the multi-signature secret key is set as the small norm matrix at the lattice, so that signatures at all layers can be generated by using the same algorithm. The algorithm is simple and effective; the security is high; the method has the unidirectionality and irreversibility; the corresponding verification cost is low; and the user experience is improved.
Owner:HUAWEI TECH CO LTD
Method for carrying out chaotic encryption based on particle travelling
InactiveCN102437909AOne-wayImprove confidentialitySecuring communicationAlgorithmTheoretical computer science
The invention relates to a method for carrying out chaotic encryption based on particle travelling, comprising the following steps of: (1) initializing: randomly generating or setting initial parameters according to given information, wherein the initial parameters comprise a reflection container parameter, an initial position, a running speed, running time and a running direction; and (2) computing a track by iteration based on the initial parameters and a reflection law to obtain the final collision position and direction and realize the encryption of the data. The method provided by the invention has the advantages of simplicity in operation, sensitivity on the initial parameters and unilateral directivity of a chaotic encryption algorithm, so that the method can be widely applied to information safety of encrypted data, secret communication and the like.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Segment joint water leakage treatment method of shield tunnel in operation period
ActiveCN110630297AImprove trapping effectGood adhesionUnderground chambersDrainageWater leakageEthylene-propylene-diene-monomer
The invention discloses a segment joint water leakage treatment method of a shield tunnel in an operation period. The segment joint water leakage treatment method of the shield tunnel in the operationperiod takes blocking as the main purpose, combines the blocking with discharging, adjusts measures to local conditions, and comprehensively treats water leakage. In the tunnel maintenance process, the segment joint water leakage treatment method of the shield tunnel in the operation period adopts the comprehensive treatment construction method including the steps of filling segment joints with acrylate in a pouring mode for blocking water, using EPDM (ethylene propylene diene monomer) strips for filling the joints again to achieve water resistance and preforming water outlet channels in thejoints preformed in two sides of the tunnel for discharging water, and achieves good treatment effect.
Owner:中交隧桥(南京)技术有限公司 +1
Upward-sloping drainage structure with self-anchoring function and construction method thereof
The invention discloses an upward-sloping drainage structure with a self-anchoring function. The upward-sloping drainage structure with the self-anchoring function comprises an anchor pipe main body,a water stop body and a grouting pipe; the anchor pipe main body comprises a steel pipe body and a spiral cutter edge; the steel pipe body is divided into a drainage section, a water stop section, ananchoring section and a pile tip which are connected in sequence in the axial direction; a plurality of drainage holes are formed in the pipe wall of the drainage section; a water filtering body is placed in the pipe cavity of the drainage section; a plurality of grouting holes are formed in the pipe wall of the anchoring section; the spiral cutter edge is arranged on the outer pipe wall of the anchoring section in a surrounding manner in a spiral strip shape; the water stop body comprises an inner water stop body and an inner water stop body; the inner water stop body is arranged in the pipecavity of the water stop body; the outer water stop body is arranged on the outer pipe wall of the water stop section annularly; the grouting pipe is arranged in the pipe cavity of the steel pipe body; one end of the grouting pipe is positioned in the anchoring section; and the other end of the grouting pipe penetrates through the inner water stop body and extends out of the end surface of the drainage section. Meanwhile, a matched construction method is provided to simplify the draining and anchoring operation in slope protection, facilitate construction, shorten the working period and reducethe cost.
Owner:CHINA MERCHANTS CHONGQING COMM RES & DESIGN INST
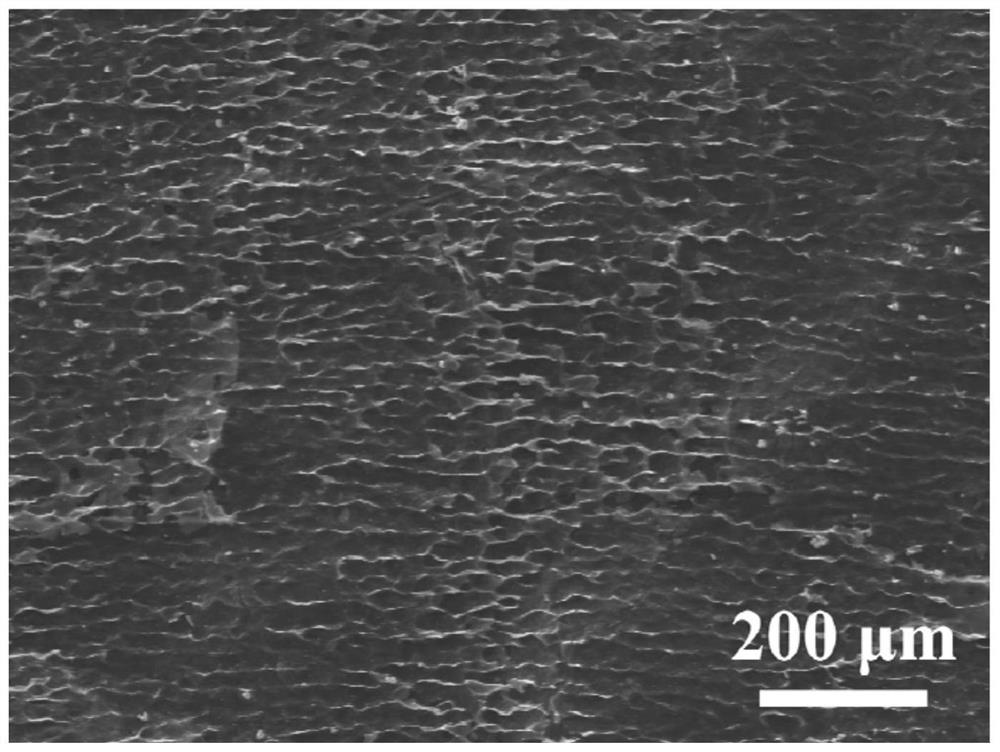
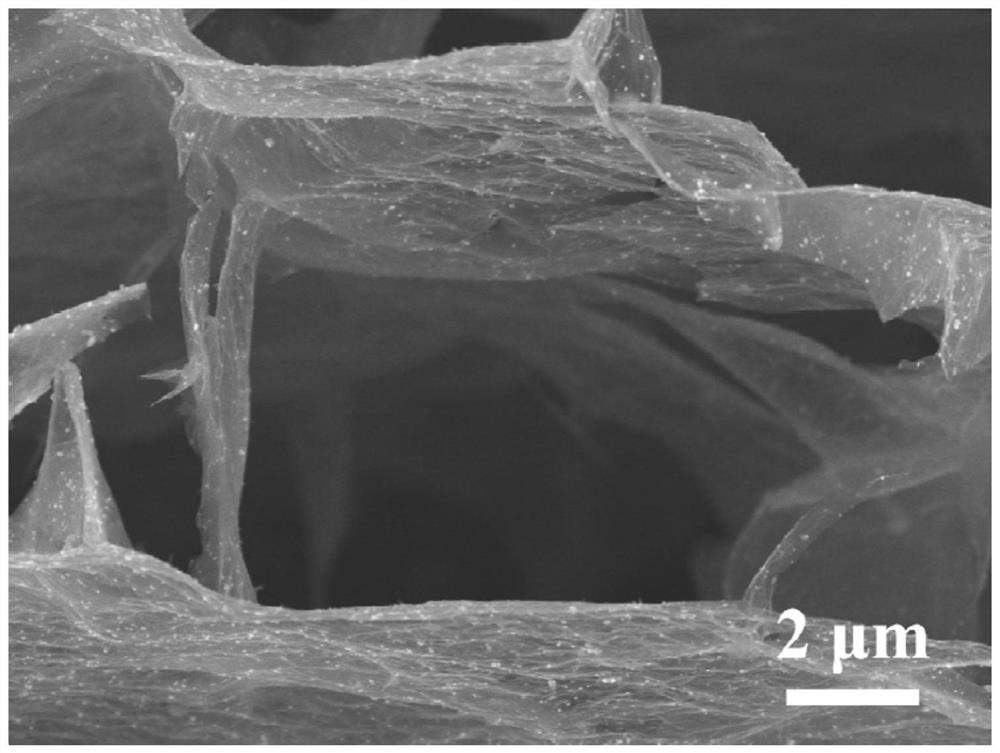
Preparation method and application of unidirectional titanium carbide aerogel
ActiveCN114349007AOne-wayAnisotropicHybrid capacitor electrodesTitanium carbideCapacitanceFreeze-drying
The invention discloses a preparation method and application of unidirectional titanium carbide aerogel, and aims to solve the problem that most of existing aerogel materials are isotropic. The preparation method comprises the following steps: adding LiF into a concentrated HCl solution, stirring, then adding Ti3AlC2 powder, and carrying out water bath stirring reaction to obtain a reaction solution; 2, sequentially carrying out centrifugal treatment by using an HCl aqueous solution and a LiCl aqueous solution; 3, centrifugally cleaning, and collecting to obtain a supernatant liquid; 4, carrying out centrifugal treatment on the supernatant liquid; 5, adding deionized water into the solid-phase precipitate to obtain uniform slurry; 6, directionally freezing the uniform slurry to obtain a solid frozen material; and 7, carrying out freeze drying treatment on the solid frozen substance. The titanium carbide aerogel with the unidirectionality obtained by the preparation method disclosed by the invention has unidirectionality in morphology and anisotropy in property. When the titanium carbide aerogel is used as a working electrode of a supercapacitor, the characteristic of high area specific capacitance is shown.
Owner:HARBIN NORMAL UNIVERSITY
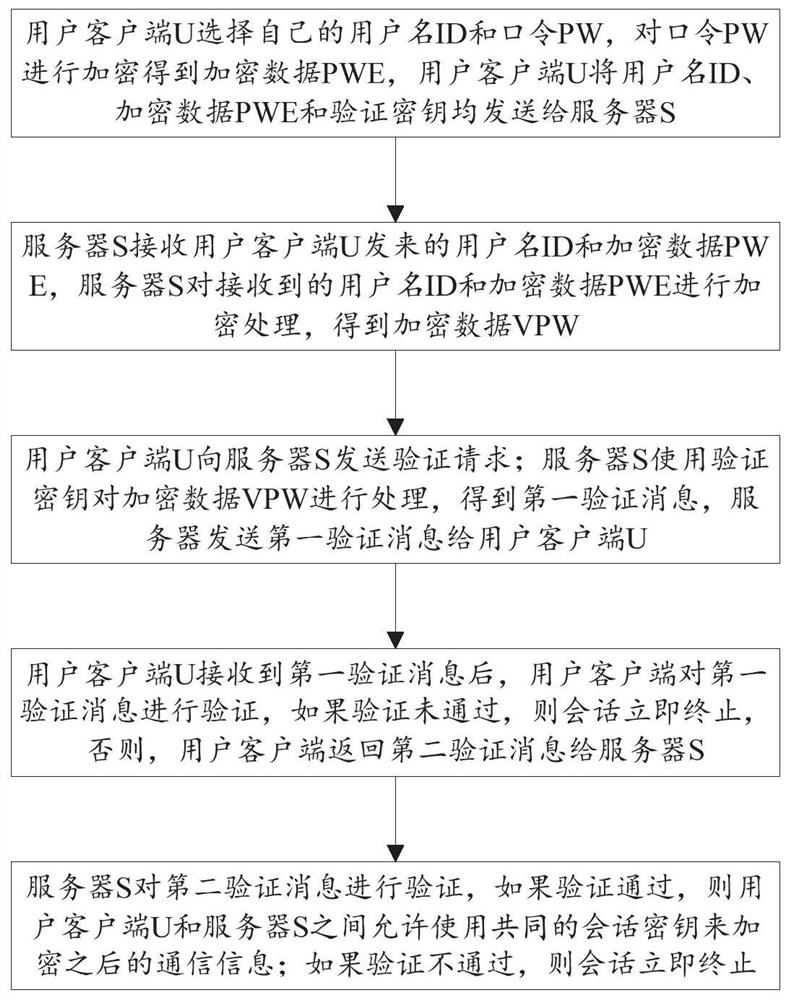
SIP security authentication method and system based on on-loop error learning problem
ActiveCN111970270AStrong resistance to attackOne-wayEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresSecurity authenticationEngineering
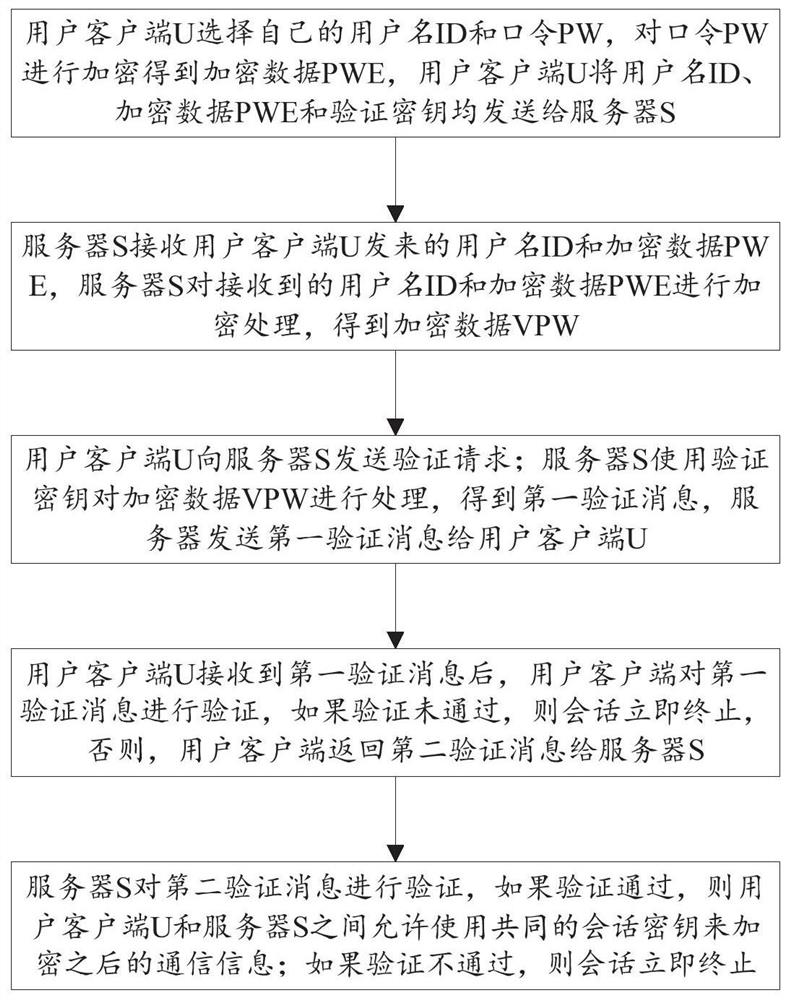
The invention discloses an SIP security authentication method and system based on an on-loop error learning problem, and the method comprises the steps: a user client U encrypts a password PW to obtain encrypted data PWE, and transmits a user name ID, the encrypted data PWE and a verification key to a server S; the server S receives the user name ID and the encrypted data PWE sent by the user client U, and encrypts the received data to obtain encrypted data VPW; the U sends a verification request to the S; the S uses the verification key to process the encrypted data VPW to obtain a first verification message; and the server sends the first verification message to the U; after the U receives the first verification message, the user client verifies the first verification message, and if theverification is passed, the client returns a second verification message to the server S; and the server S verifies the second verification message, and if the second verification message passes theverification, the client U and the server S use a common session key to encrypt the communication information.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
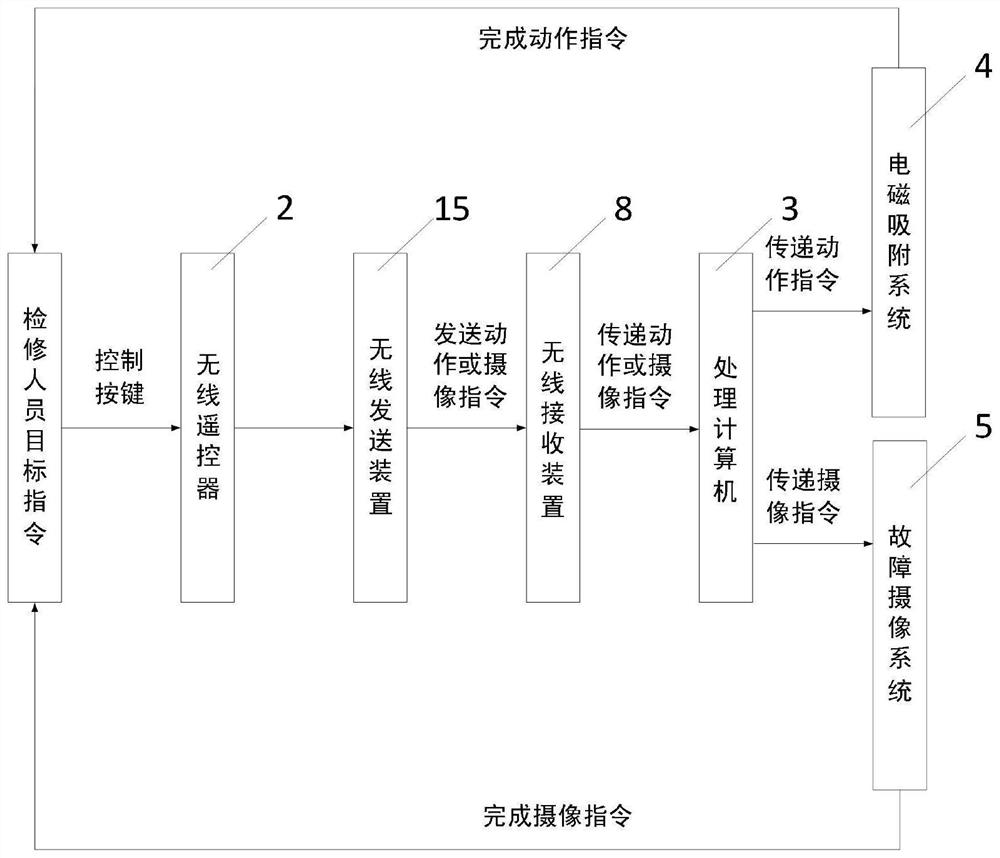
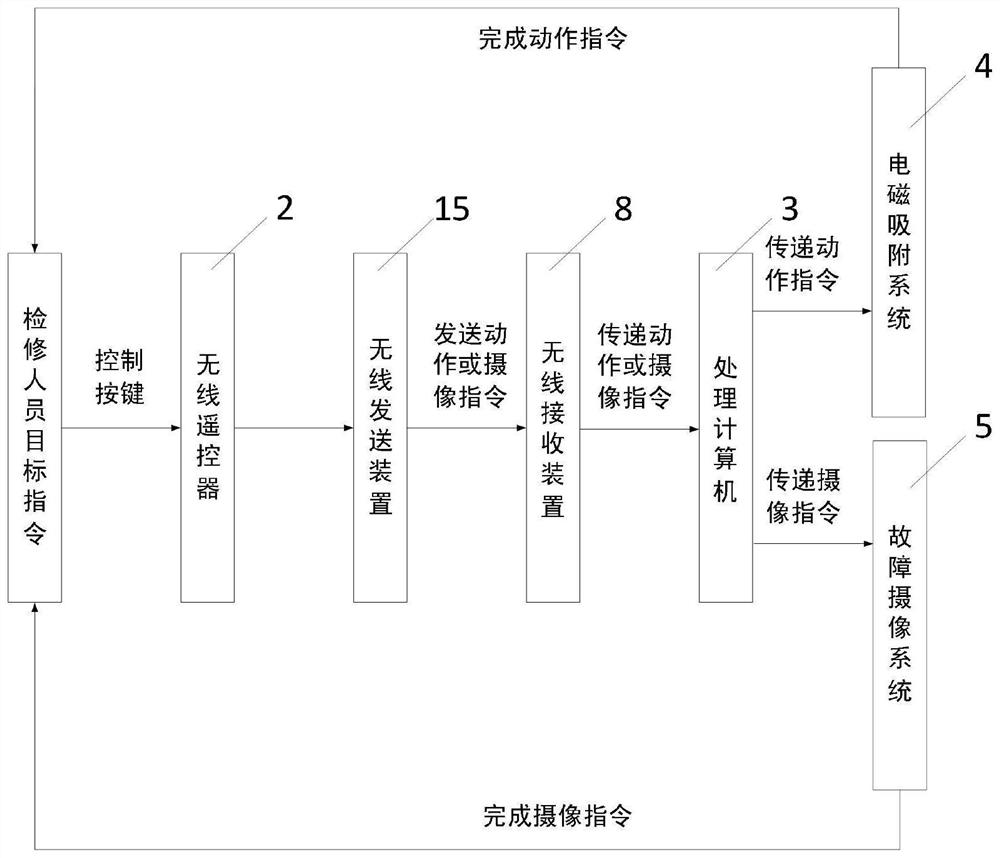
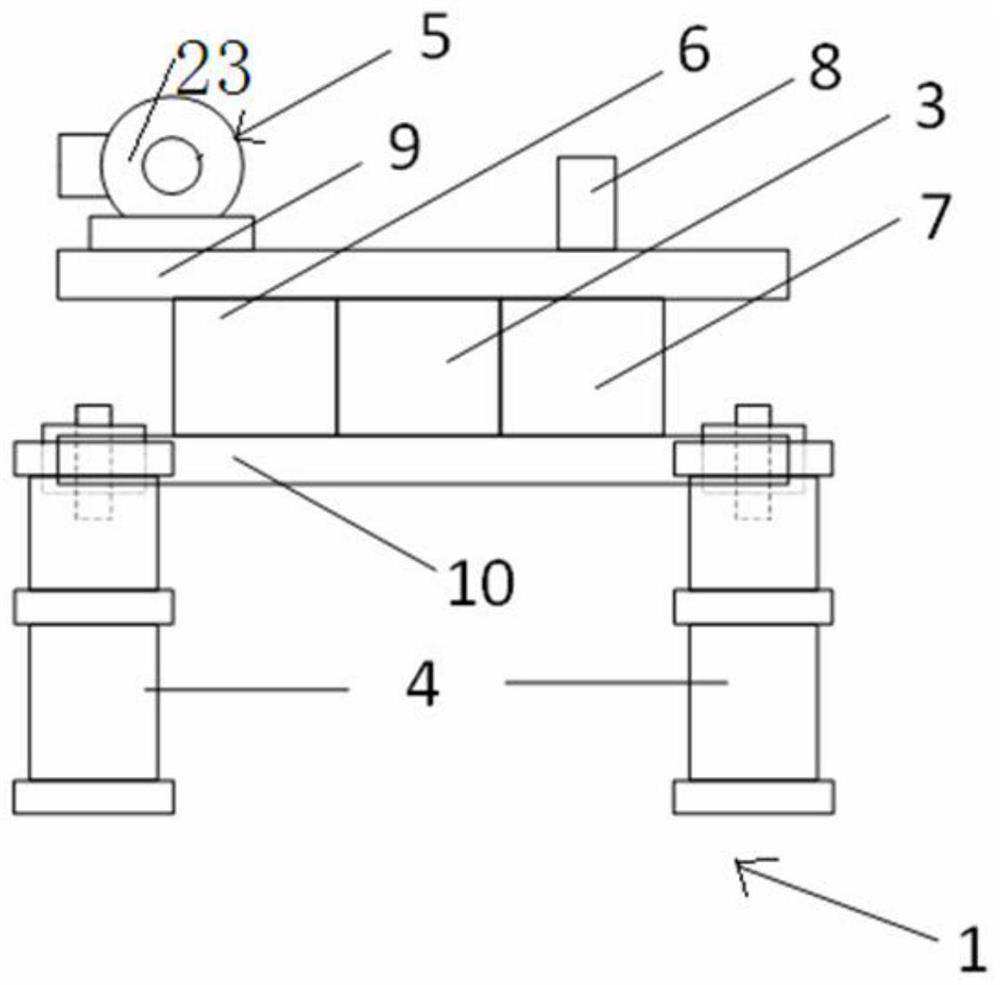
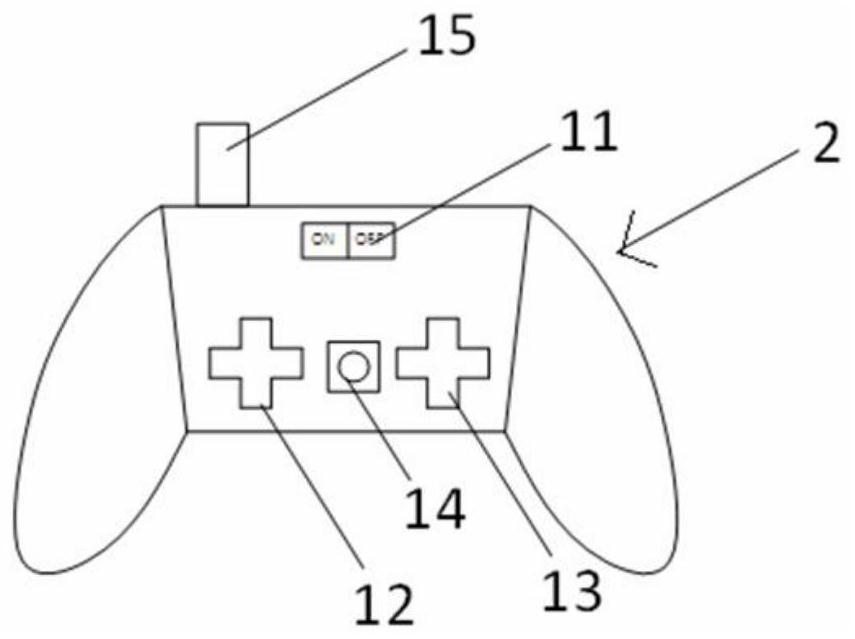
Robot suitable for inner wall of oil-immersed transformer and capable of achieving electromagnetic adsorption and climbing
The invention discloses a robot suitable for an inner wall of an oil-immersed transformer and capable of achieving electromagnetic adsorption and climbing. The robot comprises an electromagnetic adsorption type robot and a remote controller, the electromagnetic adsorption type robot is in communication connection with the remote controller, and the electromagnetic adsorption type robot is providedwith a fault camera system. The robot is small in size and can go deep into the transformer for observation; the robot has an electromagnetic adsorption capacity, can be adsorbed on a wall surface and overcomes gravity to realize climbing; the robot adapts to a complex special environment in the transformer, and can flexibly climb over prominent structural obstacles; a high-definition universal camera is carried so that a fault type and a position of the transformer can be accurately judged; remote control is achieved, and pollution to the transformer due to personnel entering is avoided; thestructure is reasonable and the performance is reliable; and a workload of maintainers is reduced, and working efficiency is improved.
Owner:GUIZHOU POWER GRID CO LTD
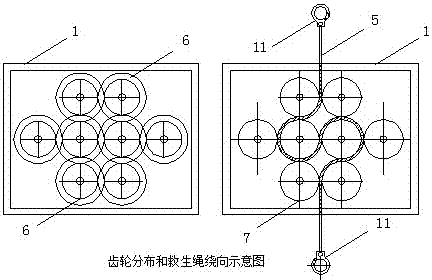
Hand-operated type high-rise lifesaving device capable of lifting in self-controlled mode
InactiveCN106983962AGreat driving forceIncreased frictional driving forceBuilding rescueGear wheelFixed frame
The invention provides a hand-operated type high-rise lifesaving device capable of lifting in a self-controlled mode, and the hand-operated type high-rise lifesaving device can manually lift in the self-controlled mode. Staff on a high building can be safely rescued without depending on a power supply when a disaster happens. A lifting device comprises an assembly housing, a lifesaving hanging basket, a lifesaving rope and the like, wherein a transmission mechanism fixing frame is fixedly arranged inside a lifting device assembly housing; a transmission gear group and a lifesaving rope friction wheel group are arranged on the fixing frame; and gears in the transmission gear group are coaxially connected with friction wheels in the lifesaving rope friction wheel group correspondingly. One of the lifesaving rope friction wheels is coaxially connected with one of the transmission gears and a transmission worm; the transmission worm is engaged with worm wire teeth through wheel teeth; and the worm is connected with a hand-operated handle by passing through the assembly housing. The lifesaving rope passes through gaps among the friction wheel group and penetrates through the middle part of the lifting device assembly housing. The two ends of the lifesaving rope are connected with safety hooks which can be hooked on the high building. The lifesaving hanging basket is connected with a fixed ring on the lifting device assembly housing through the rope. In use, one end of each safety hook is fixedly arranged on the high building, a passenger stands in the lifesaving hanging basket, and the handle is operated by hands to be controlled to lift, so that safe lifesaving is realized. The hand-operated type high-rise lifesaving device capable of lifting in the self-controlled mode is simple in structure, is convenient to operate, and is safe and reliable.
Owner:徐晓峰
Barn solar direct heating device and solar auxiliary direct heating barn
InactiveCN103062918BEmission reductionReduce coal consumptionTobacco preparationSolar heating energyInsulation layerEngineering
The invention discloses a direct solar heat supply device of a curing barn and the curing barn with an auxiliary direct solar heat supply function. The direct solar heat supply device of the curing barn comprises light transmission plates, hollow light transmission heat-insulation layers, a solar heat collecting panel and a radiating component; the curing barn with the auxiliary direct solar heat supply function comprises a baking chamber of the curing barn, a heat supply chamber, a circulating fan and a plurality of direct solar heat supply devices of curing barns; and the direct solar heat supply devices of the curing barn are mounted on the top of the baking chamber of the curing barn and can directly replace a roof of the baking chamber of the curing barn to directly supply heat to the baking chamber of the curing barn. The direct solar heat supply device and the curing barn have the advantages that solar energy can be transmitted from the outside of the curing barn to the inside of the curing barn in a one-way manner by the aid of the direct solar heat supply device of the curing barn, the multiple direct solar heat supply devices of the curing barn are mounted on the top of the baking chamber of the curing barn, the thick roof which is commonly adopted for realizing a heat-insulation effect for a curing barn and is high in manufacturing cost is omitted, and effects of effectively and directly utilizing the solar energy and saving baking energy can be realized.
Owner:KUNMING 750 HIGH TECH +2
Code responsibility investigation method and system based on block chain technology
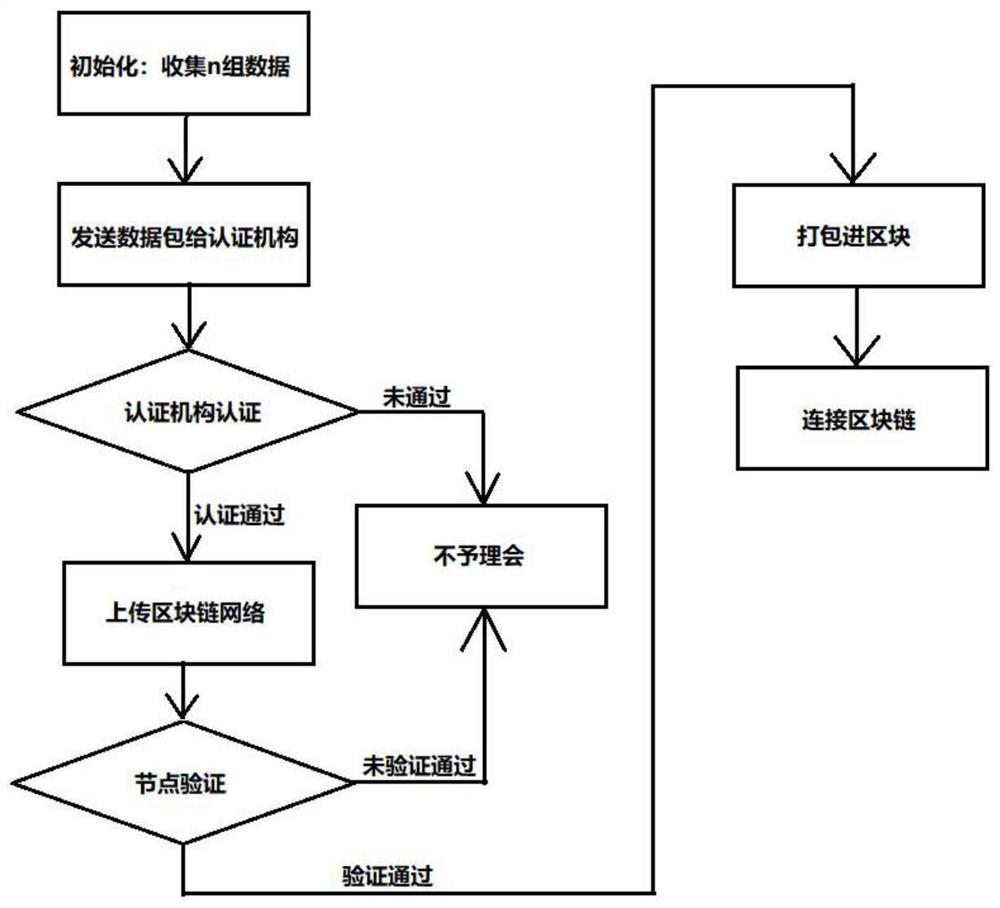
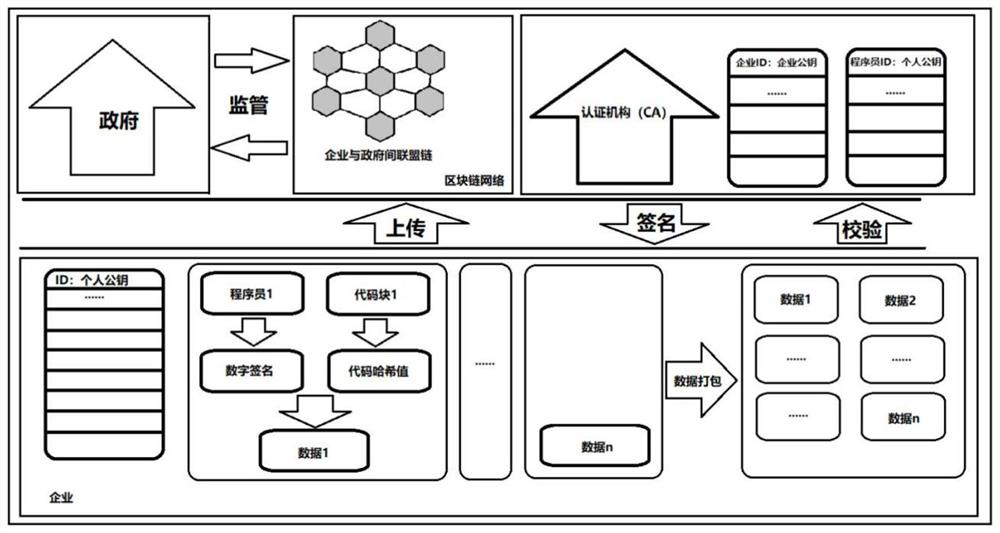
PendingCN112015460AWith decentralizationReliable basisDigital data protectionSoftware maintainance/managementData packConfidentiality protection
The invention discloses a code responsibility investigation method based on a block chain technology. The method comprises the following steps: encrypting collected N groups of code related data containing corresponding programmer information by adopting an enterprise private key to generate corresponding data packets, sending the data packets to an authentication institution, and verifying the enterprise information to which the data packets belong and the programmer information corresponding to each group of code related data contained in the data packets by the authentication institution; if the verification is passed, enabling the certification authority to digitally sign the data packet and transmit the data packet back to the enterprise; and after hash processing is carried out on the data packet digitally signed by the certification authority, uploading the data packet and the enterprise public key to a P2P network together for node verification, and if the verification is passed, packaging the data packet and sending to the blockchain through the node. The invention can provide a code tracing system model for increasingly programmed society, and has the characteristics of reliability, credibility, decentralization and privacy and confidentiality protection.
Owner:NANJING INST OF TECH
Multi-channel switching value input circuit system with novel structure
PendingCN114189235AOne-wayImprove insulation performanceLogic circuit coupling arrangementsElectronic switchingHemt circuitsEngineering
The invention discloses a multi-channel switching value input circuit system with a novel structure, and relates to the technical field of switching value output channels, the multi-channel switching value input circuit system comprises an optical coupler, a light emitting diode, a control power supply and a driving power supply, the optical coupler is composed of a light emitting part, a light receiving part and a signal amplification part; the input end of the optical coupler belongs to a low-resistance element working in a current mode, so that the optical coupler has very strong common-mode rejection capability; therefore, the signal-to-noise ratio can be greatly improved when the antenna is used as a terminal isolation element in long-line information transmission; an interface device is used for signal isolation in computer digital communication and real-time control, so that the working reliability of the computer can be greatly improved; and an optocoupler feedback circuit formed by a linear optical coupler is utilized, the duty ratio is changed by adjusting the current of a control end, the purpose of precise voltage stabilization is achieved, a high-voltage power supply can be fundamentally prevented from being connected into DCS and PLC clamping pieces in series, and the protection performance and reliability of the DCS and the PLC are improved.
Owner:BAIYANGHE POWER PLANT OF HUANENG SHANDONG POWER GENERATION CO LTD
Language card
The present invention discloses a language card, and relates to the electronic field. The language card comprises a word-to word card, a word-to-pronunciation card, a pronunciation-to-word card and apronunciation-to-pronunciation card. The language card is characterized in setting of a corresponding relation. The corresponding relation is set in that: the corresponding relation can express the same thing, can express the same meaning, can express similar or opposite meanings, explanation, word combination and sentence making, can be extended and even can be a corresponding relation defined bytwo things having no corresponding relation by a user himself; the corresponding card is established to establish a corresponding relation between words and pronunciation, a language card is established to combine things except the words and the pronunciation with the words and pronunciation to establish a connection therebetween so as to create a condition for conversion of two things and establish a wider language card.
Owner:陈勇
Distributed data transaction payment method
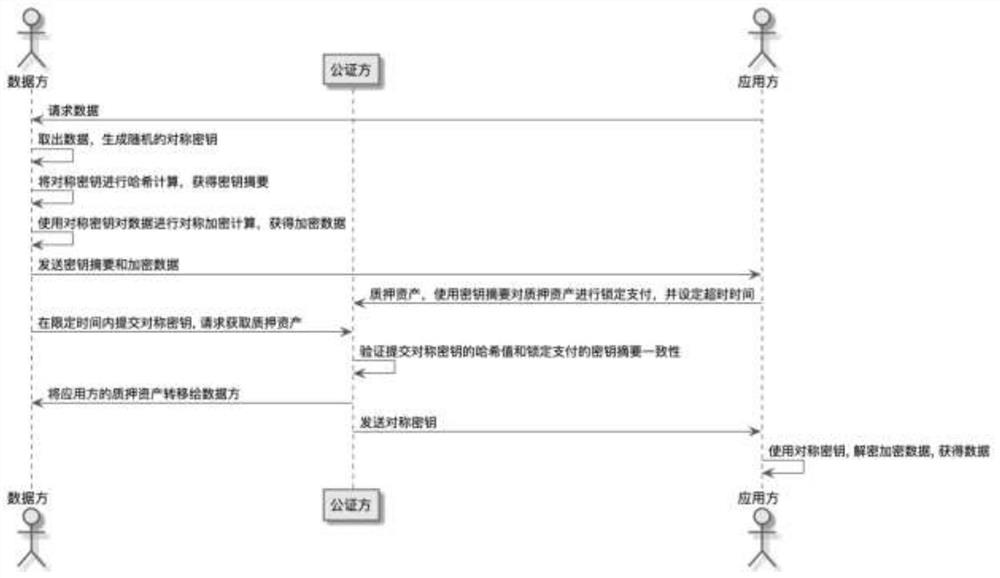
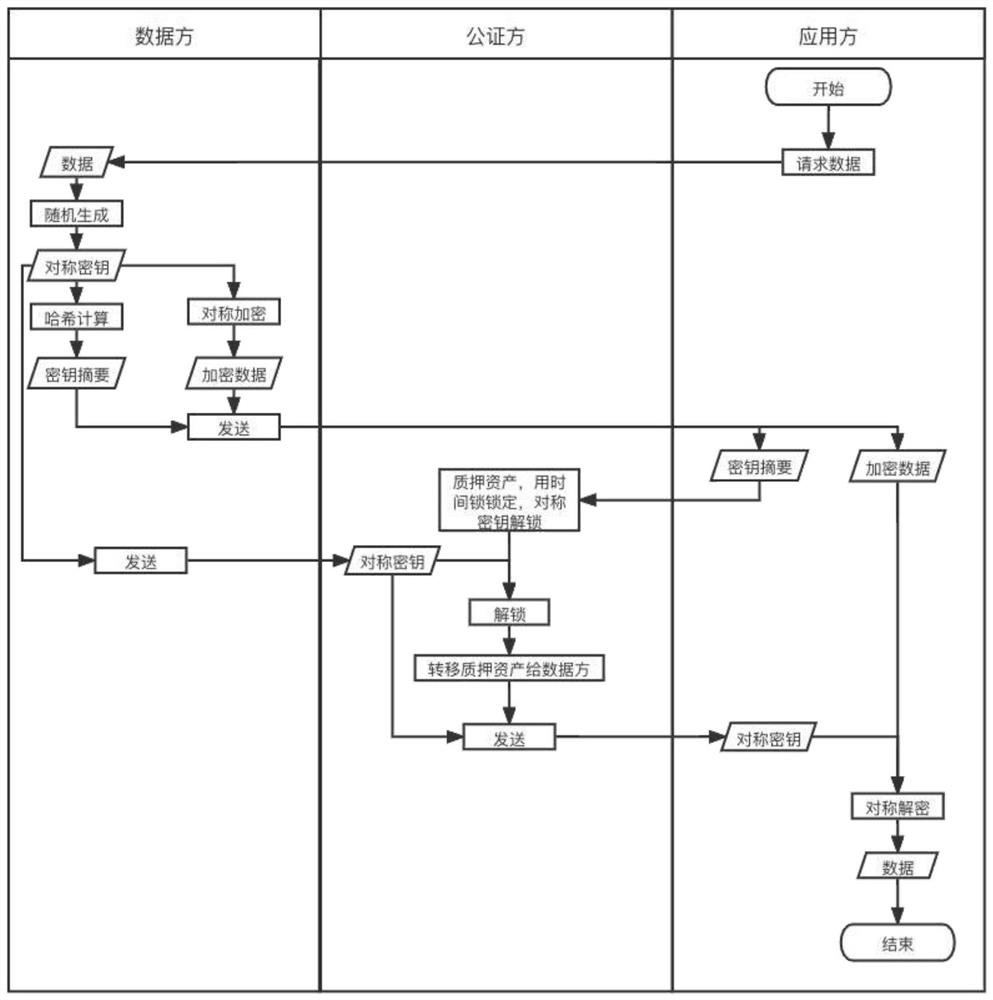
InactiveCN114529296AConfidentialityDeterministicFinancePayment protocolsPayment transactionConfidentiality
The invention discloses a distributed data transaction payment method. The distributed data transaction payment method is as follows: an application party requests data M from a data party; after the data party obtains the data M required by the application party, a random symmetric key K is generated; the data party performs hash calculation on the symmetric key K to obtain a key abstract e; the data party performs symmetric encryption calculation on the data M by using the symmetric key K to obtain encrypted data ME; the data party sends the key abstract e and the encrypted data ME to the application party; the application party pledges assets at the notarization party and sets timeout time; the data party sends a symmetric key to the notarization party, and the pledged assets are transferred to the data party; the application party obtains data M from the notarization party; according to the invention, in a specific scene, the data party and the application party carry out data payment transaction through the notarization party, and the notarization party completes verification on the premise of not obtaining data, so that the security of the transaction and the confidentiality of the data to the notarization party are both considered.
Owner:南京隐私遁区块链科技有限公司
A Hash fingerprint based on position information and DNA information, and a construction method and application thereof
ActiveCN109214831AImprove recognition rateBroad market spaceGeographical information databasesCommerceGeographic sitePlaintext
The invention discloses a Hash fingerprint based on position information and DNA information and a construction method and application thereof. The Hash fingerprint of the invention is obtained by collecting plant geographic position information and DNA characteristic coding information, digitally marking the characteristic information and constructing the Hash fingerprint. The method comprises the following steps of: firstly, carrying out one-way Hash code (an irreversible mapping from plaintext to ciphertext) on the plant geographic position information (obtained through a global positioningsystem) and DNA information, and storing and encrypting the one-way Hash code, the process only encrypts, not decrypts, any length of the input after the change to a fixed length of the output. The algorithm of the invention can extract the traceability characteristic information of the plant according to the difference of the position information and the DNA information of the plant, and carry out the Hash fingerprint identification, and the identification rate is high.
Owner:云智前沿科技发展(深圳)有限公司
operational amplifier circuit
ActiveCN102570989BOne-wayGood linear transconductanceAmplifier modifications to reduce non-linear distortionDifferential amplifiersAudio power amplifierPower flow
An operational amplifier, characterized in that it includes: an input structure, which includes an NMOS input operational amplifier circuit and a PMOS input operational amplifier circuit; a feedback network, which includes an NMOS feedback loop connected to the NMOS input operational amplifier circuit and a PMOS input operational amplifier circuit. The PMOS feedback loop connected to the discharge circuit, the NMOS feedback loop and the PMOS feedback loop are used to make the current of the transistor depend on the input voltage and the input The size of the terminal resistance; the output structure, which amplifies the signal transmitted from the input structure; and the bias network, which supplies power to the input structure, output structure and feedback network at the same time. The invention sets a reference voltage and adopts a high-gain operational amplifier feedback loop, and the current in the transistor has unidirectionality, which can obtain good linear transconductance and simultaneously realize a large (from ground to power supply voltage) voltage input dynamic range.
Owner:CSMC TECH FAB2 CO LTD
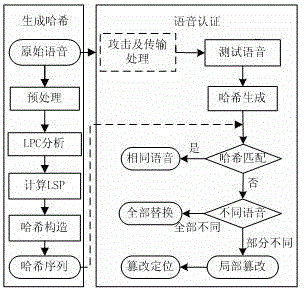
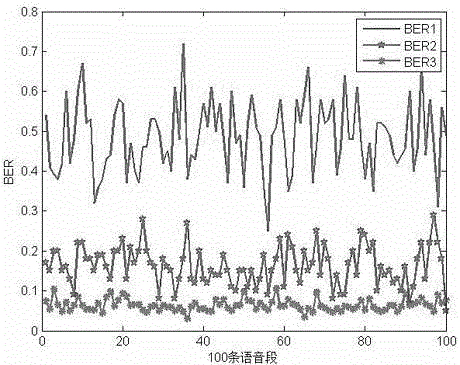
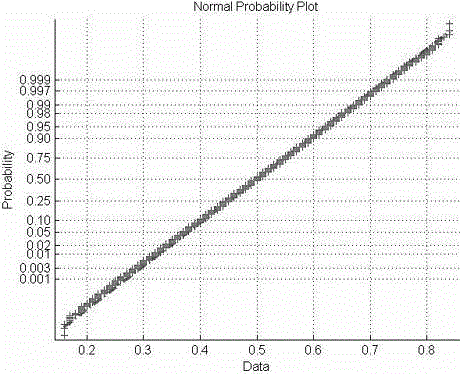
Phonetic empathy Hash content authentication method capable of implementing tamper localization
InactiveCN102915740BSimple structureImprove authentication efficiencySpeech analysisAlgorithmVoice communication
A voice-aware hash content authentication method that can realize tampering and positioning. First, the voice signal is preprocessed, and each frame of voice signal is subjected to 10-order linear predictive analysis, and the line spectrum pair LSP coefficient is obtained by the discrete Fourier transform method. As a perceptual feature; then the voice data is grouped sequentially, and the expected sequence weighted by the LSP coefficients of each group of voices is combined as the final authentication data, and the amount of authentication data is compressed by hash construction; finally, the voice content is realized by hash matching. fast authentication. This method is robust to content maintenance operations such as changing volume, echo, and resampling, and is sensitive to malicious operations such as replacement and deletion. It can accurately locate tampered areas, and has the characteristics of small authentication data and high operating efficiency. For resource-constrained voice communication terminals.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
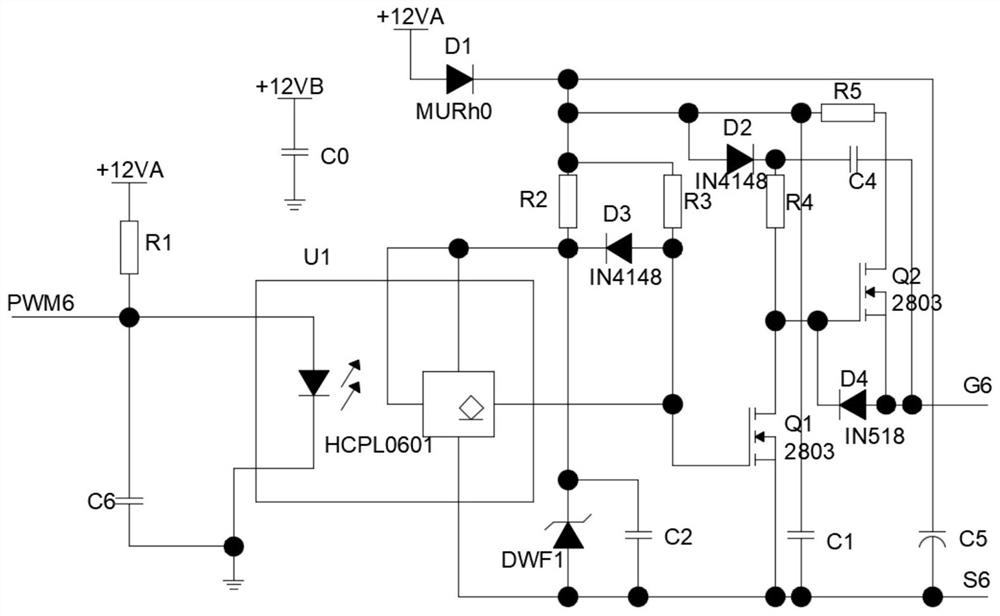
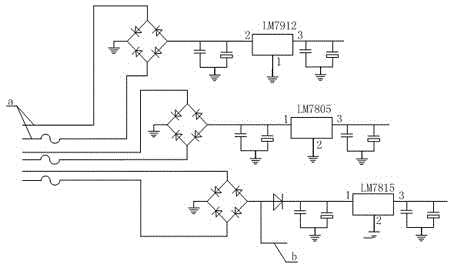
Suitable for power supply circuit of intermediate frequency electrotherapy instrument
The invention discloses a power supply circuit suitable for an intermediate frequency electrotherapy instrument, comprising a first power supply circuit, a second power supply circuit and a third power supply circuit, the first power supply circuit comprising a first bridge rectifier circuit electrically connected and the first three-terminal voltage regulator, the second power supply circuit includes a second bridge rectifier circuit and a second three-terminal voltage regulator electrically connected, and the third power supply circuit includes a first A three-bridge rectifier circuit, a diode and a third three-terminal regulator, the voltage input terminals and the voltage output terminals of the first three-terminal regulator, the second three-terminal regulator and the third three-terminal regulator All are connected with decoupling circuits, the input terminals of the first bridge rectifier circuit, the second bridge rectifier circuit and the third bridge rectifier circuit are all connected with resettable fuses, and the decoupling circuit includes the first A capacitor and a second capacitor, the first capacitor and the second capacitor are connected in parallel and a common terminal is grounded. It can provide a variety of voltages to optimize the performance of each electronic component of the intermediate frequency electrotherapy instrument.
Owner:CHENGDU TRINIDAD ELECTRONICS EQUIP
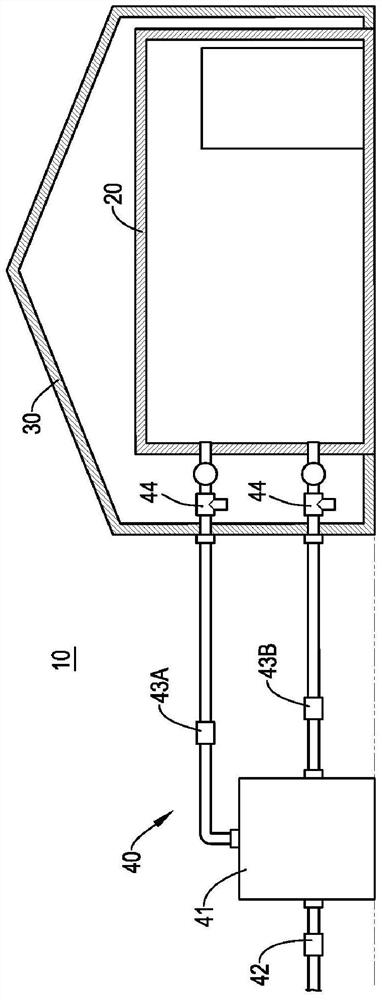
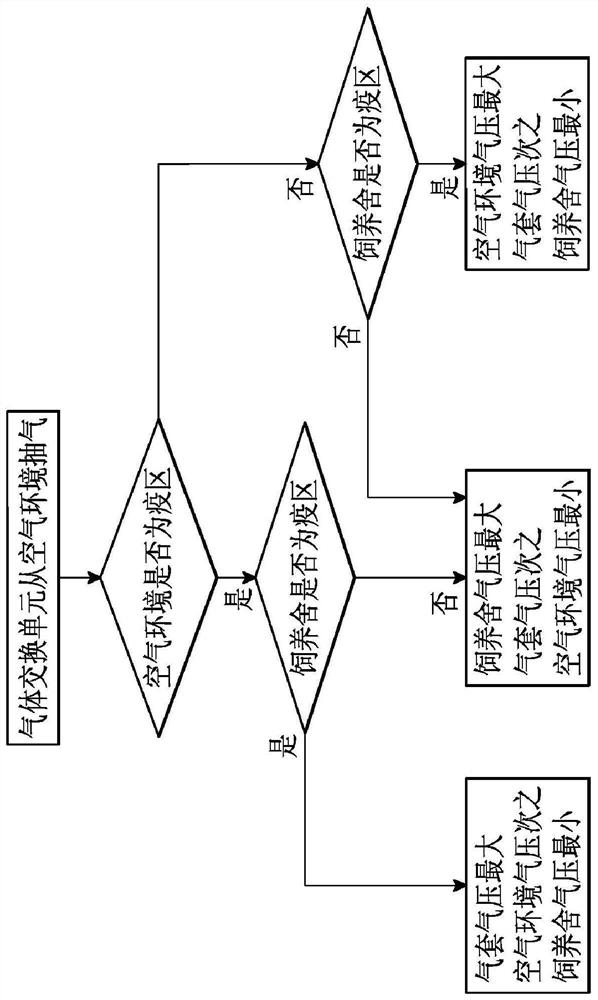
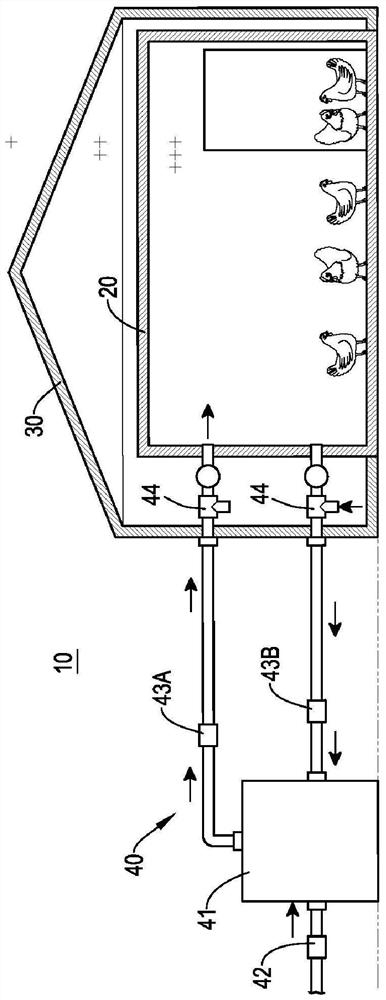
Environmental cleaning system for animal farms
ActiveCN106665370BImprove efficacyOne-wayAnimal housingBird housingsFisheryEnvironmental engineering
The present invention is an environment cleaning system for an animal breeding house, comprising an air environment, a feeding house and a cleaning treatment equipment, the breeding house is a closed space, the cleaning treatment equipment is connected to the air environment and the breeding house, and includes A gas exchange unit, which exchanges gas with the air environment and the breeding house, so as to control the relative air pressure between the breeding house and the air environment, so the present invention can make the gas between the breeding house and the air environment Circulation is one-way, and achieves the effect of epidemic prevention.
Owner:张家铭
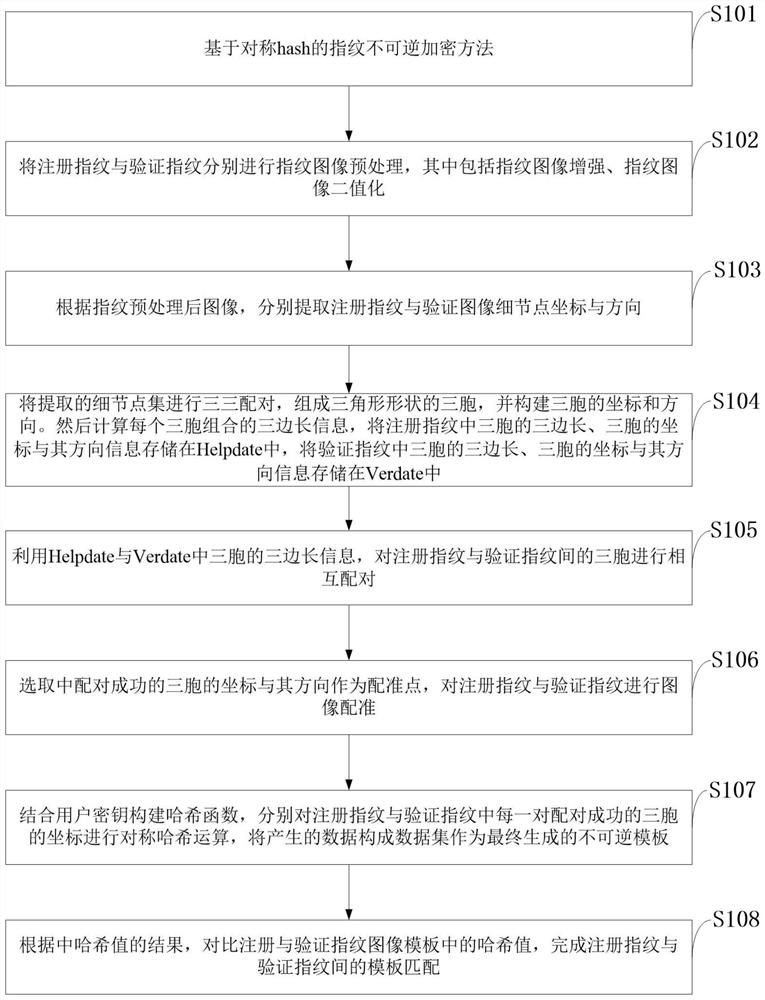
An irreversible fingerprint template encryption method based on symmetric hash
ActiveCN108960039BProtection securityRevocableMatching and classificationHash functionRemainder function
The invention belongs to the technical field of fingerprint recognition and encryption fusion in pattern recognition, and discloses an irreversible fingerprint template encryption method based on symmetric hash. The method of combining symmetric hash function with positive remainder function can strictly guarantee the irreversibility of hash operation. The security of the entire encryption algorithm is improved. Because the number of equations of the constructed hash function is less than the number of inputs, that is, the rank of the coefficient matrix of the non-homogeneous equations is equal to the rank of the augmented matrix, and is smaller than the number of equations, there are infinitely many equations in theory solution, so the input data information cannot be pushed back through the result. In addition, due to the characteristic that the output of the sine and cosine functions corresponds to infinitely many inputs, the irreversibility of the algorithm of the present invention is raised to a higher level. Even if an attacker steals the user's key and template, it cannot push back the user's original fingerprint. At the same time, in the process of hash operation, the method of combining user keys is simpler, more efficient, and more revocable.
Owner:XIDIAN UNIV
A Treatment Method for Water Leakage in Segment Joints in Shield Tunnel During Operation Period
ActiveCN110630297BImprove trapping effectGood adhesionUnderground chambersDrainageLeaking waterArchitectural engineering
The invention discloses a treatment method for leaking water from segment joints in a shield tunnel during an operation period. The invention focuses on blocking, combines blocking and draining, adapts measures to local conditions, and comprehensively treats the leaking water. During the maintenance of the tunnel, a comprehensive treatment construction method of "filling the seams with acrylate grouting to block water, re-sealing waterproofing with EPDM strips, and reserving joints on both sides of the tunnel to reserve water channels for drainage" was adopted. , and achieved a better governance effect.
Owner:中交隧桥(南京)技术有限公司 +1
A robot suitable for electromagnetic adsorption and climbing on the inner wall of oil-immersed transformer
The invention discloses a robot suitable for electromagnetic adsorption and climbing on the inner wall of an oil-immersed transformer. system. The invention is small in size and can be observed deep inside the transformer; it has electromagnetic adsorption ability, can be adsorbed on the wall and overcome gravity to achieve climbing; adapts to the complex special environment inside the transformer, and can flexibly climb over prominent structural obstacles; carries a high-definition universal camera , can accurately determine the type and location of transformer faults; remote control operation will not cause pollution to the transformer due to personnel entering; reasonable structure, reliable performance; reduce the workload of maintenance personnel and improve work efficiency.
Owner:GUIZHOU POWER GRID CO LTD
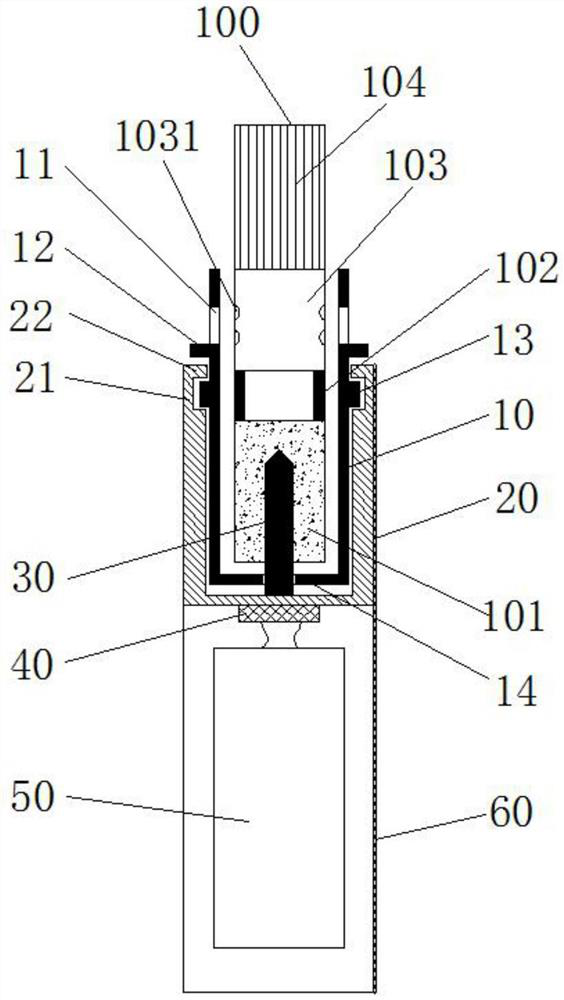
Electric heating smoking set with movable inner smoke cup, fuming system and using method thereof
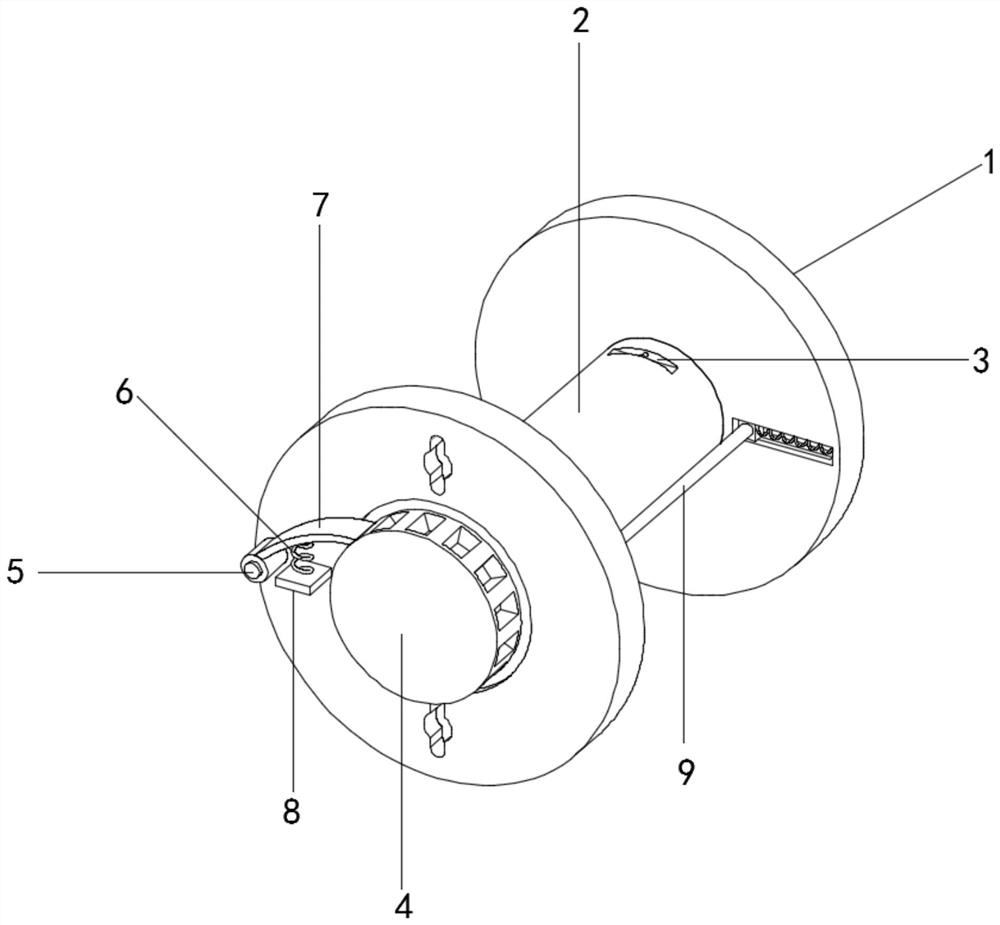
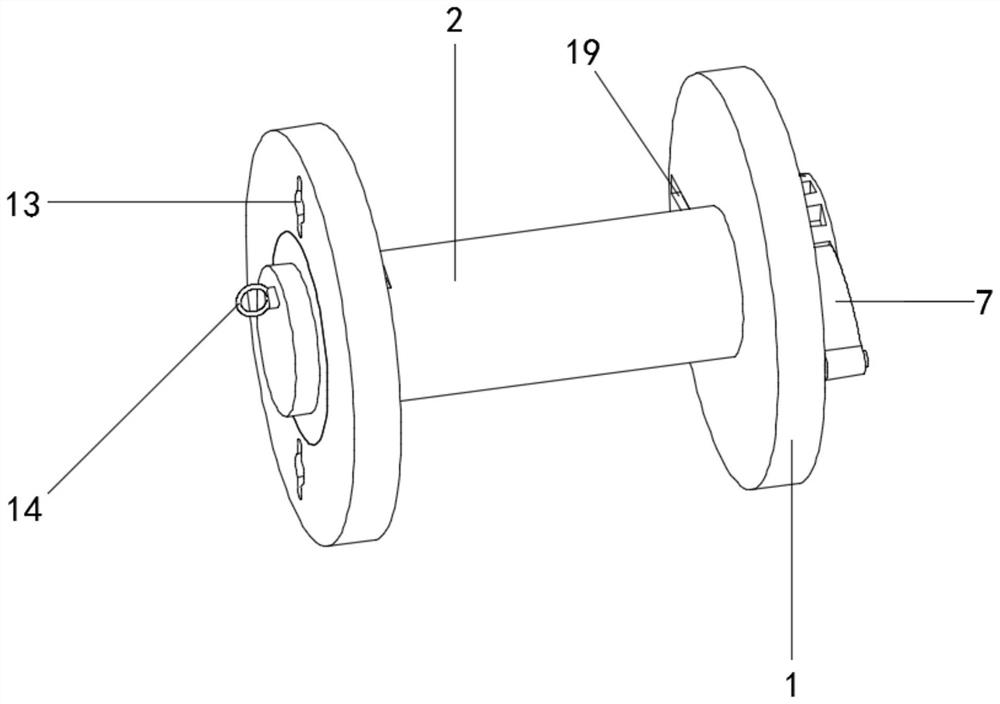
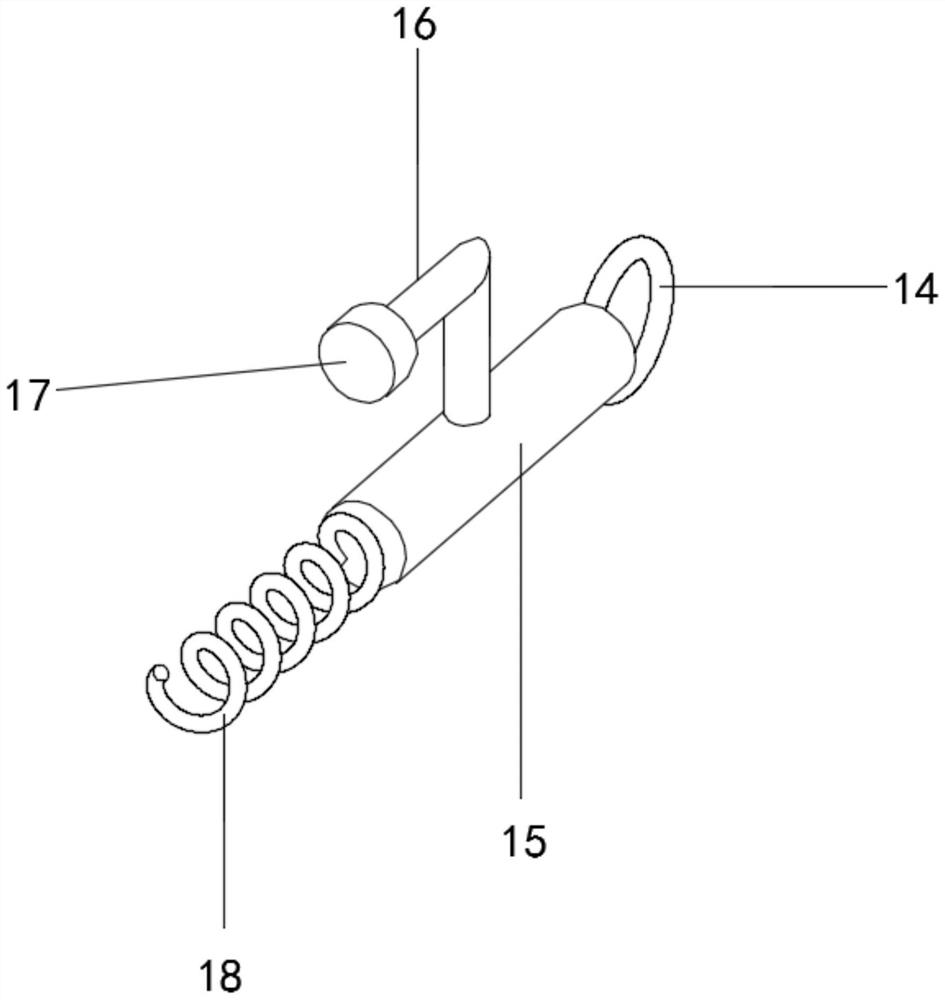
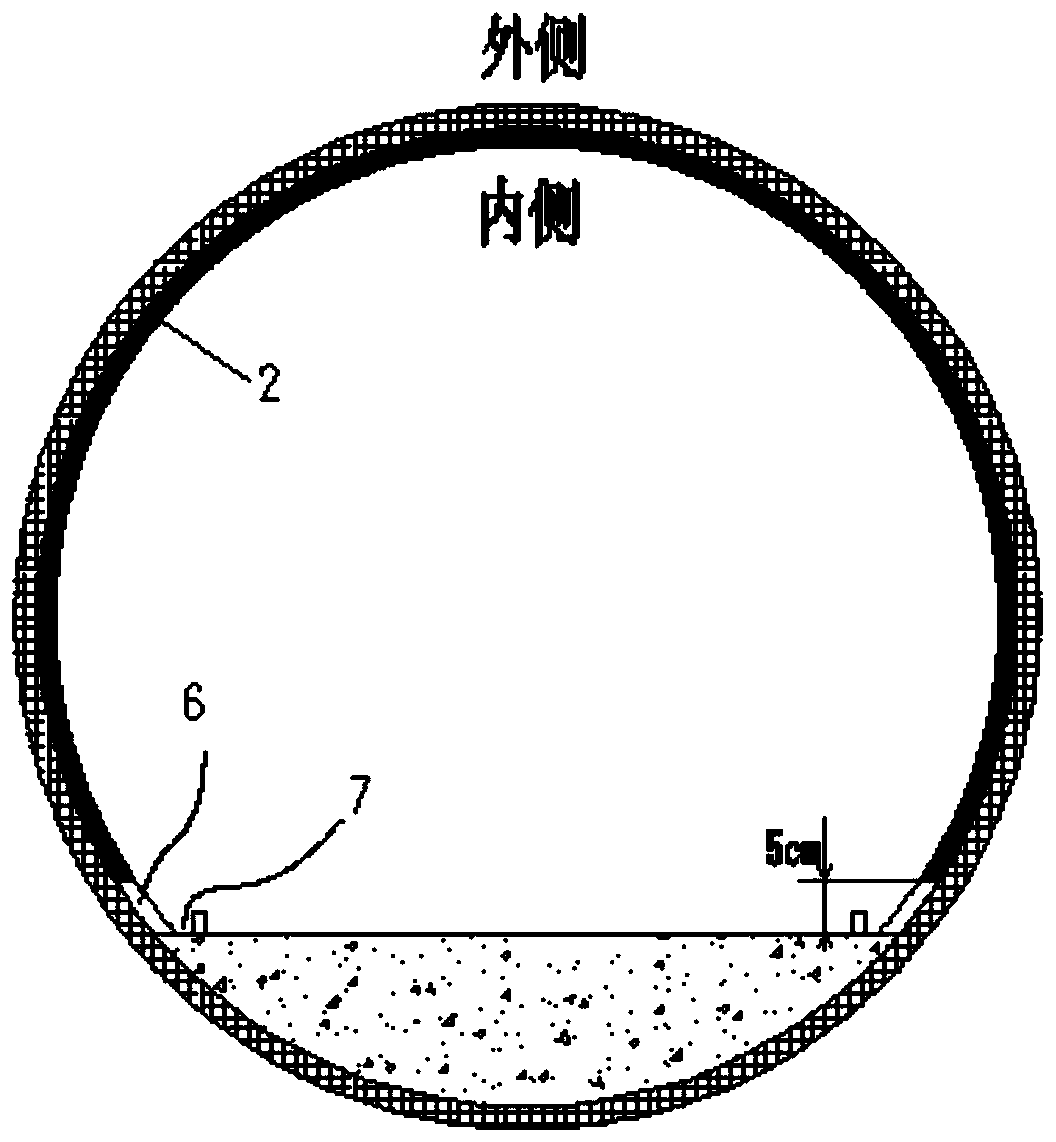
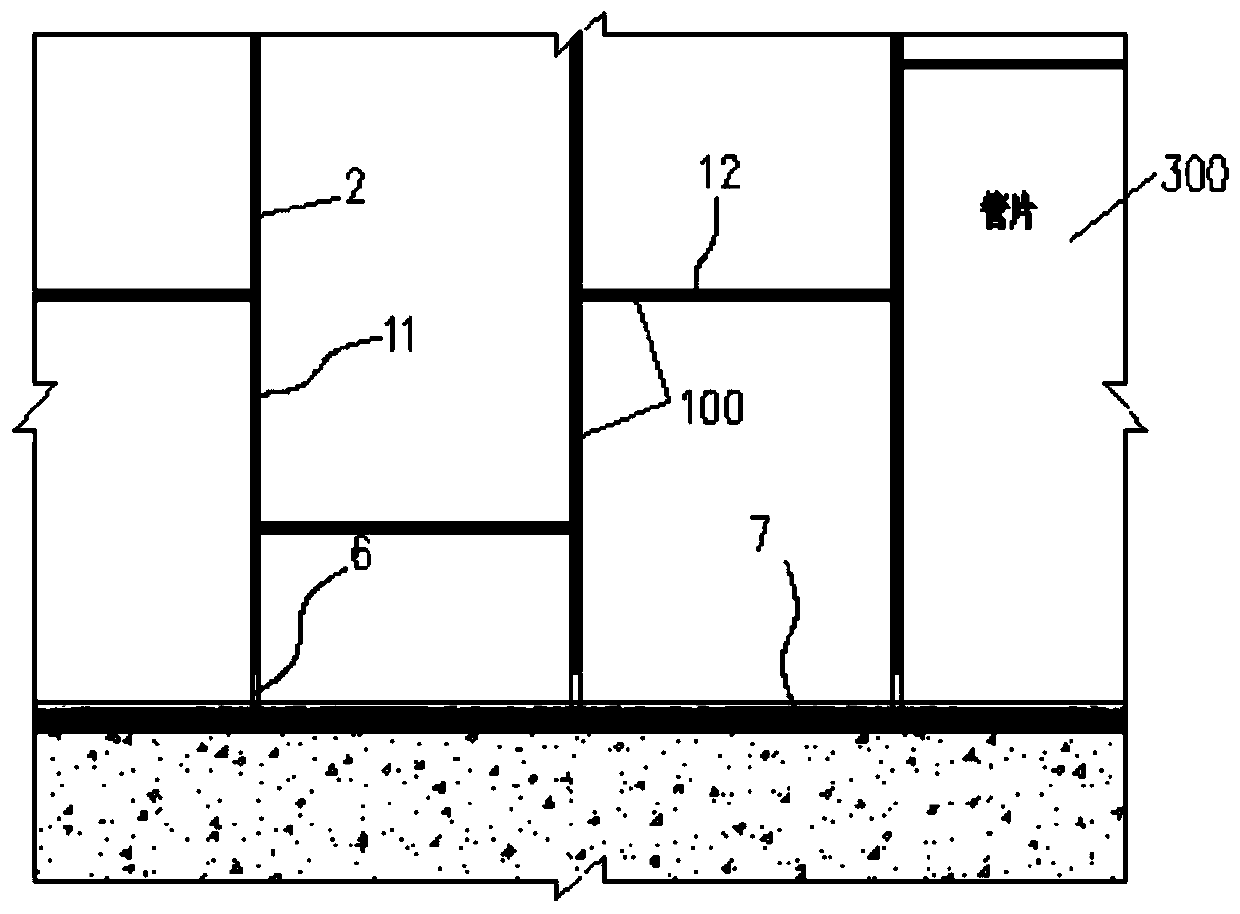
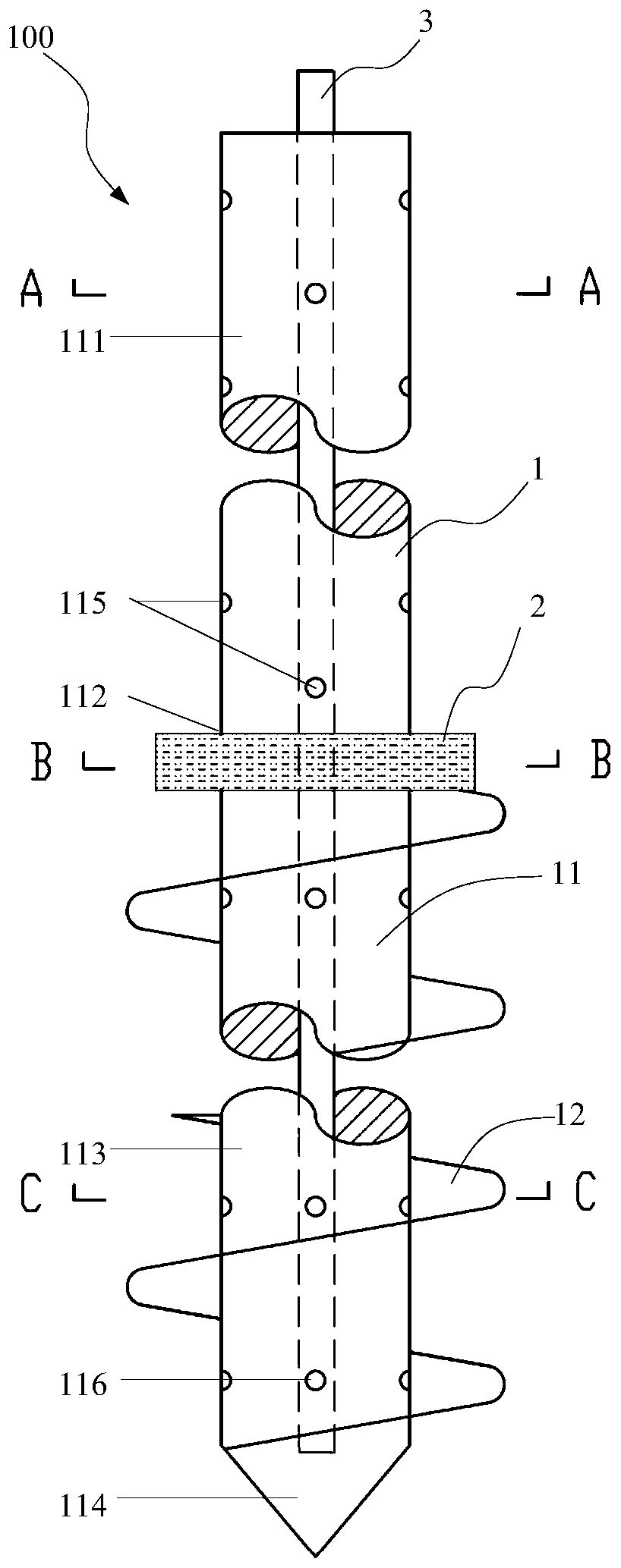
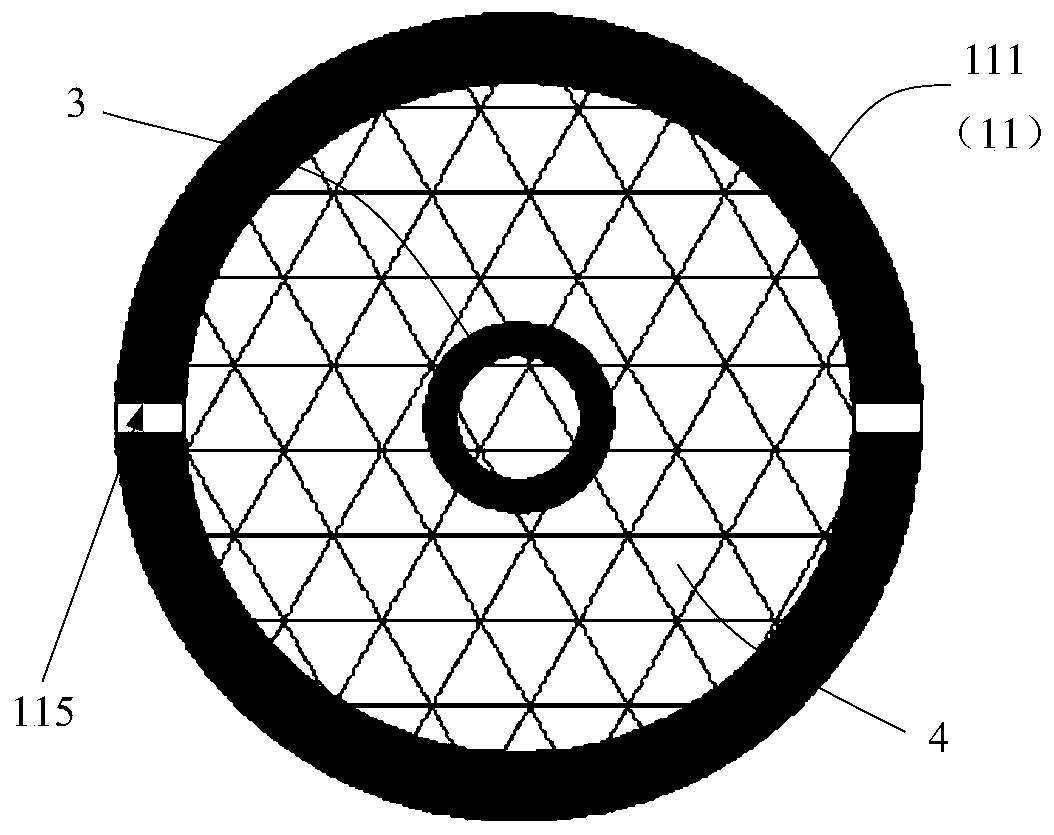
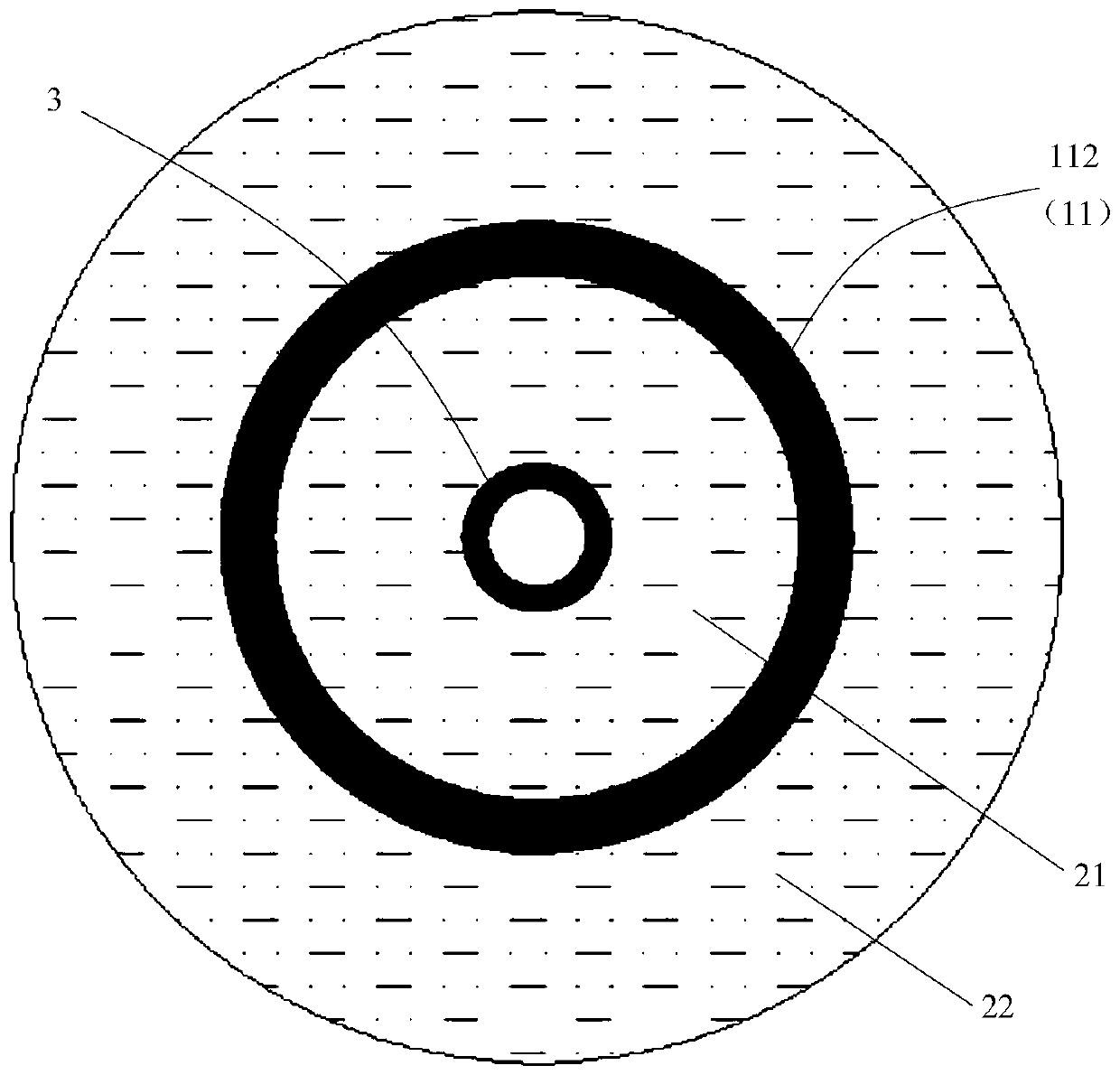
The invention belongs to the technical field of heating smoking sets, and particularly relates to an electric heating smoking set with a movable inner smoke cup, a fuming system and a using method thereof. The electric heating smoking set comprises an inner cigarette cup (10) and an outer cigarette cup (20). The inner cigarette cup (10) is formed by combining a plurality of components, the combined whole is of a hollow cylinder structure, the bottom of the inner cigarette cup (10) is sealed, and the outer wall of the inner cigarette cup (10) is provided with point-shaped protrusions (13). The outer cigarette cup (20) detachably surrounds the periphery of the inner cigarette cup (10) by means of matching of the clamping grooves (21) and the point-shaped protrusions (13). After the inner cigarette cup is inserted into the outer cigarette cup, the smoke generating section of the cigarette can be sealed by the inner cigarette cup. In the smoking process, the oxygen content in the smoking set can be reduced, so that the heating temperature can be greatly increased, aroma components in tobacco can be released more sufficiently, the taste is closer to that of traditional tobacco, and the smoking set is easier to accept by traditional smokers.
Owner:CHINA TOBACCO YUNNAN IND +1
SIP security authentication method and system based on learning problem with errors on the loop
ActiveCN111970270BOne-wayStrong resistance to attackEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPasswordEngineering
The present application discloses a SIP security authentication method and system based on the learning problem with errors on the ring. The user client U encrypts the password PW to obtain the encrypted data PWE, and sends the user name ID, the encrypted data PWE and the verification key to the server S The server S receives the username ID and the encrypted data PWE sent by the user client U, encrypts the received data, and obtains the encrypted data VPW; U sends a verification request to S; S uses the verification key to process the encrypted data VPW, After obtaining the first verification message, the server sends the first verification message to U; after U receives the first verification message, the user client verifies the first verification message, and if the verification passes, the client returns the second verification message to the server S; the server S verifies the second verification message, and if the verification passes, the client U and the server S use a common session key to encrypt subsequent communication information.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Hash fingerprint based on location information and dna information and its construction method and application
ActiveCN109214831BImprove recognition rateBroad market spaceGeographical information databasesCommercePlaintextAlgorithm
The invention discloses a Hash fingerprint based on location information and DNA information, a construction method and application thereof. The Hash fingerprint of the present invention is obtained by collecting plant geographical location information and DNA feature coding information, digitally marking the feature information, and constructing a Hash fingerprint. The method described is to first store and encrypt the geographical location information of plants (acquired through the global satellite positioning system) and DNA information with a one-way Hash code (an irreversible mapping from plaintext to ciphertext). There is only encryption, no decryption, and a fixed-length output is obtained after changing the input of any length. The algorithm of the invention can extract the traceability characteristic information of the plant according to the difference of the position information of the plant and the DNA information, and carry out Hash fingerprint identification, and the identification rate is high.
Owner:云智前沿科技发展(深圳)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com