Phonetic empathy Hash content authentication method capable of implementing tamper localization
A technology for perceiving hashing and authentication methods, applied in speech analysis, instruments, etc., can solve problems such as low efficiency and inability to achieve tampering and positioning, and achieve the effect of simple construction process and high authentication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
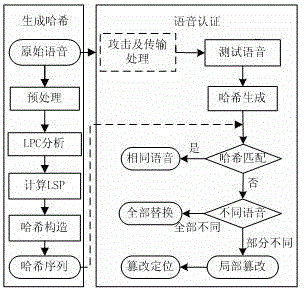
[0019] The present invention is a voice perception hash content authentication method that can realize tampering and positioning, and the steps are as follows:
[0020] (1) Divide the speech signal A into frames, divide it into equal-length frames of 20 ms, use the Hamming window for windowing, and frame shift to 15 ms;
[0021] (2) Perform LPC analysis on each frame of speech signal to obtain its 10th order LPC coefficient;
[0022] (3) Convert each frame of LPC coefficients into LSP coefficients, and the LSP coefficients of each frame of speech signals are combined into matrix A for one row;
[0023] (4) Group the LSP coefficients sequentially, and decompose the weighted matrix A of each group to obtain a new matrix A J ;
[0024] (5) Generate hash vector h, ;in is the value of the nth-order LSP coefficient of the i-th frame data;
[0025] (6) Hash matching: According to the above steps, first extract the perceptual features from the sender, perform calculations and c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com