Method and device for detecting intranet Trojans
A detection method and technology for Trojan horses, applied in the field of Internet security, can solve the problems that unknown Trojan horses or potential Trojan horses cannot be found, and it is easy to cause false negatives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
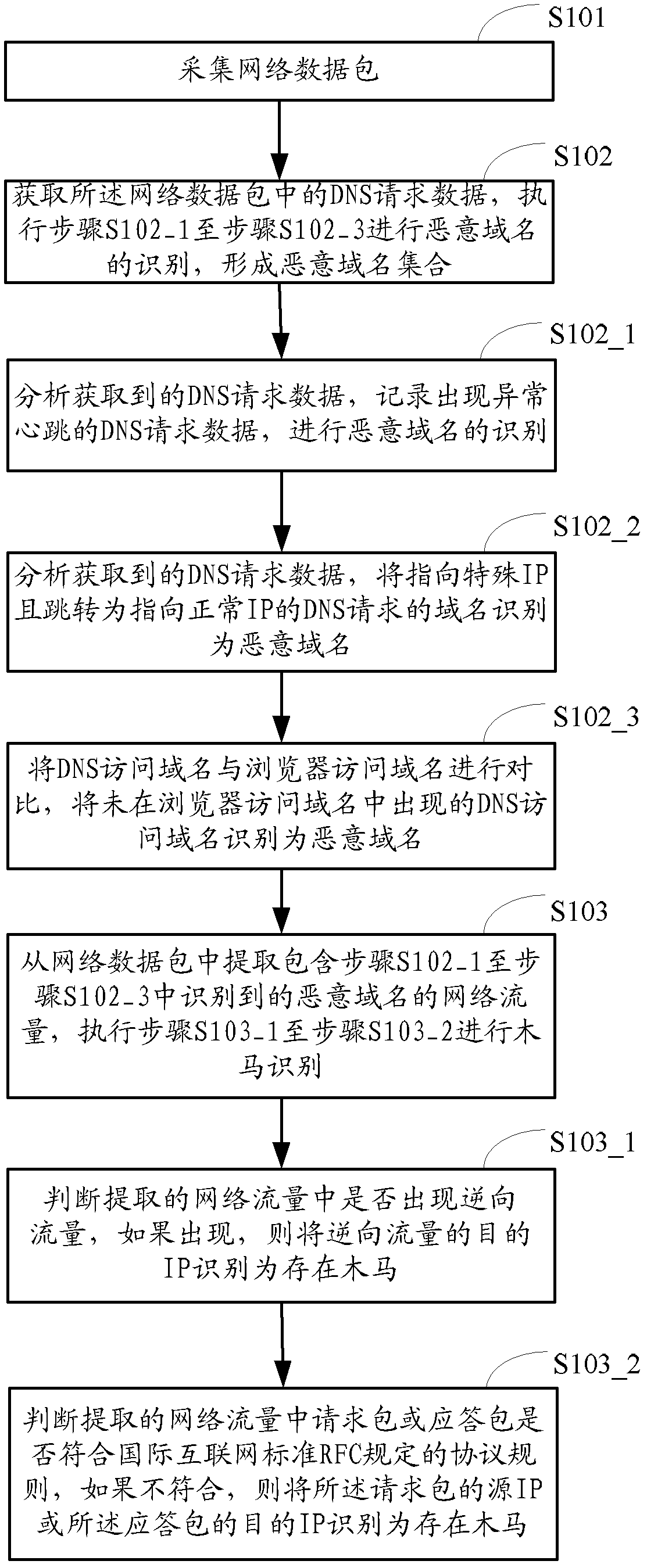
[0081] figure 1 It is the flow chart of the detection method of the intranet Trojan provided by the present embodiment, as figure 1 As shown, the method includes:
[0082] Step S101, collecting network data packets.
[0083] After the Trojan horse is successfully implanted into the target computer, the Trojan horse control terminal must establish a connection relationship with the controlled terminal to communicate, so as to remotely control the controlled host computer to steal information. The controlled end of the Trojan horse sends a DNS (domain name resolution) request to the remote domain name server according to the preset control domain name of the control end, and then resolves the IP address of the control end according to the received DNS request response, and initiates a connection to the IP address of the control end.
[0084] After invading the target system, the Trojan horse uses various means to deceive users and disguise itself, such as packing, adding flowe...
Embodiment 2
[0183] Figure 7 The structure diagram of the detection device for the intranet Trojan horse provided by this embodiment, such as Figure 7 As shown, the device includes: a collection module 10 , a domain name identification module 20 and a Trojan horse identification module 30 . in
[0184] The collecting module 10 is used for collecting network data packets.
[0185] The collection module 10 is used to collect network data packets in real time, so that subsequent modules can extract data conforming to the characteristics of Trojan horse communication behaviors from the collected network data packets, so as to determine whether there is a potential safety hazard. The collected network data packets may include but not limited to: data packets of protocols such as DNS, TCP, or HTTP.
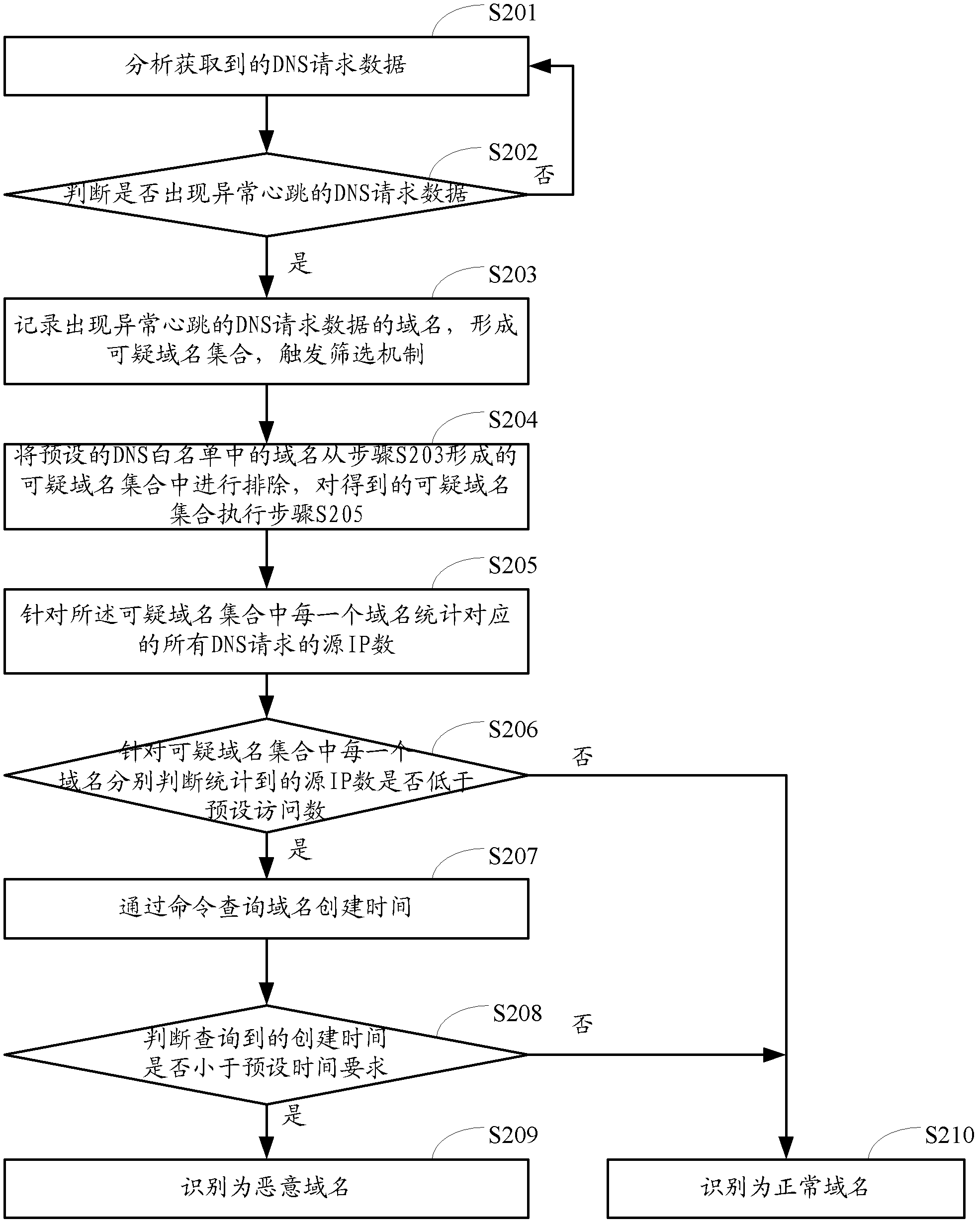
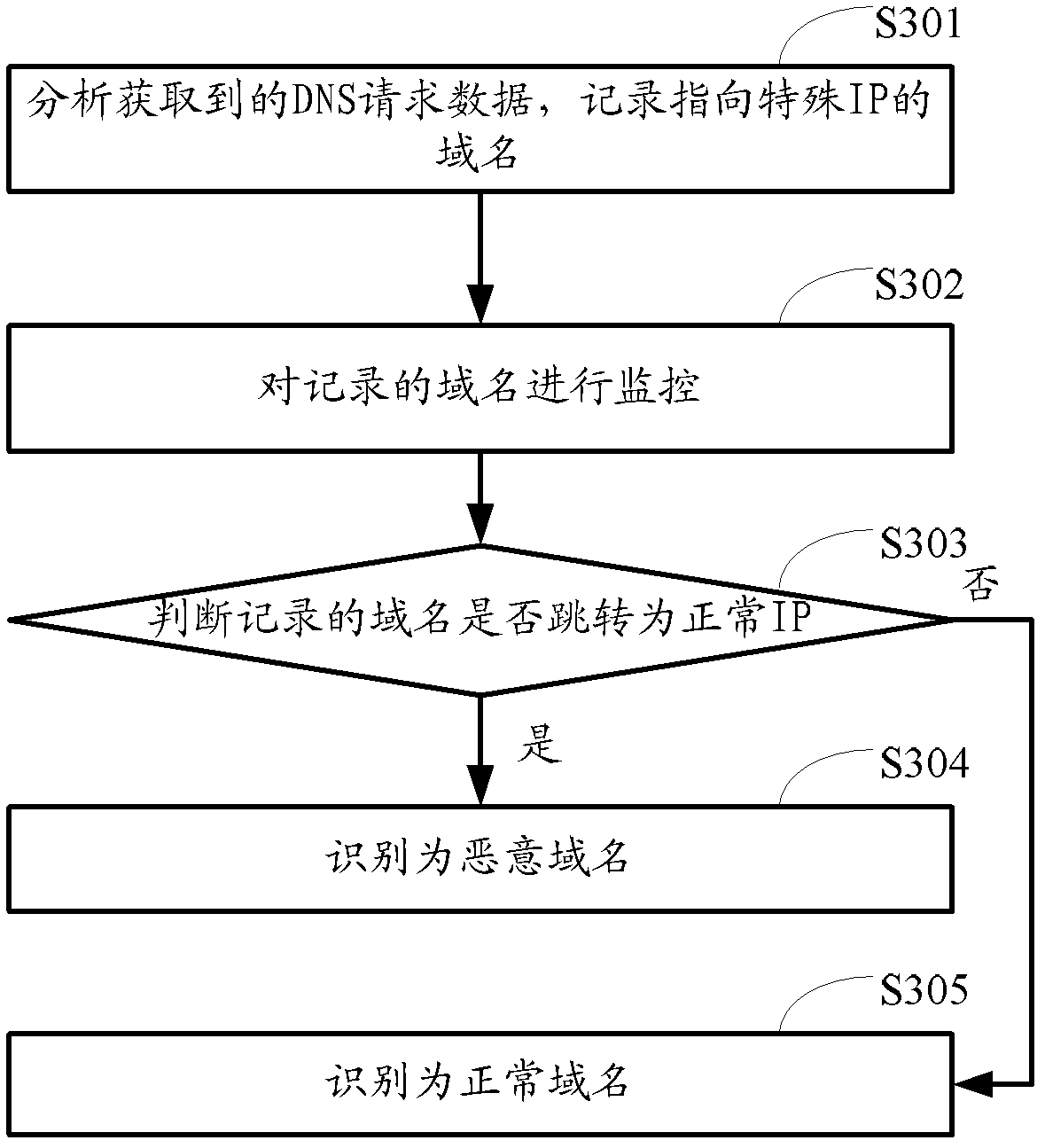
[0186] The domain name identification module 20 is used to obtain the DNS request data in the network data packet, utilize at least one of the first domain name identification module 201 to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com