AES-based 192-bit key extension system and method
A key expansion and bit-bit technology, which is applied in data encryption, key expansion in Advanced Encryption Standard AES, and network communication, can solve the problems of increasing encryption time, large data volume, and large power consumption, and reduce the number of cycles , The effect of simplifying the judgment conditions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
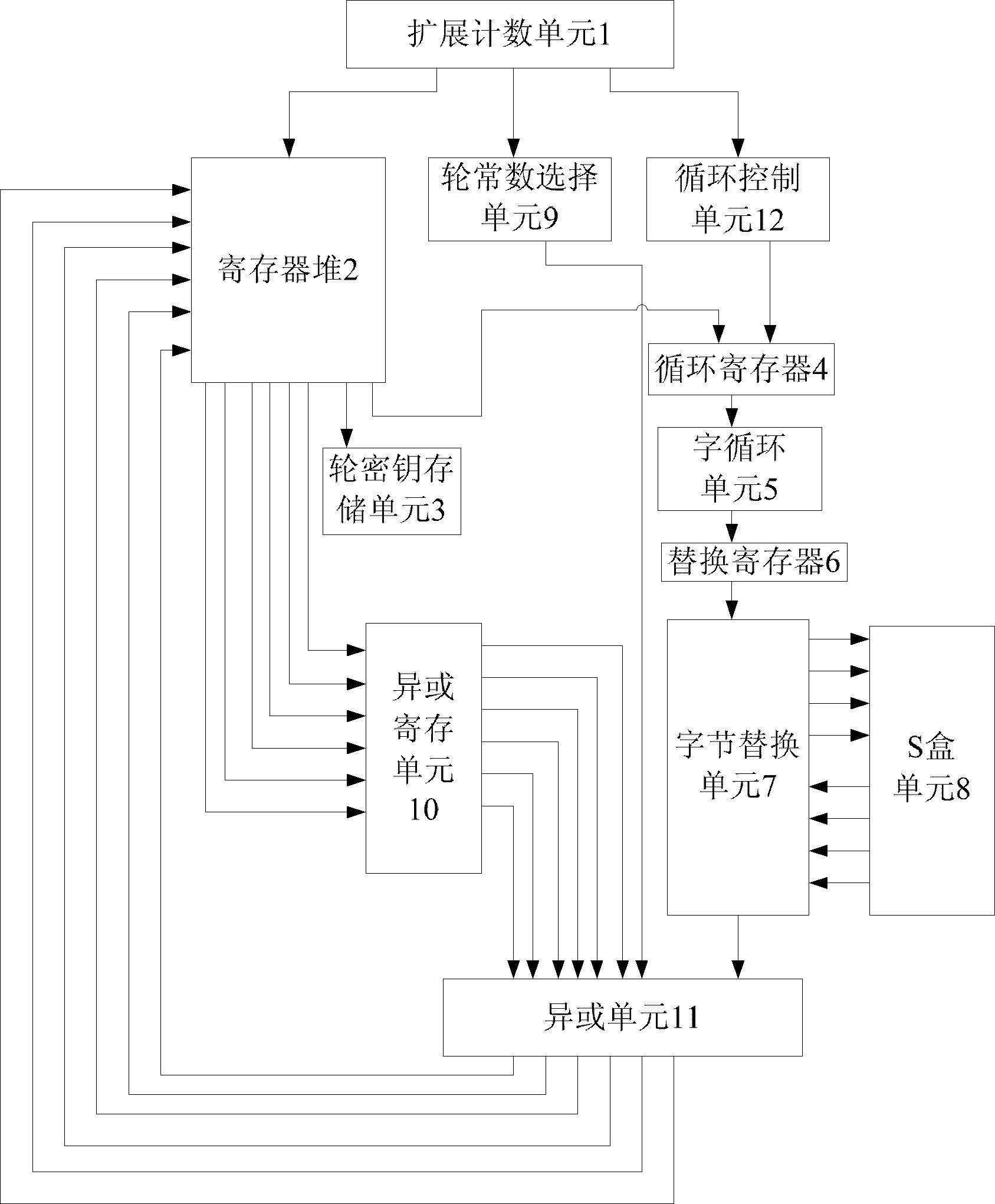
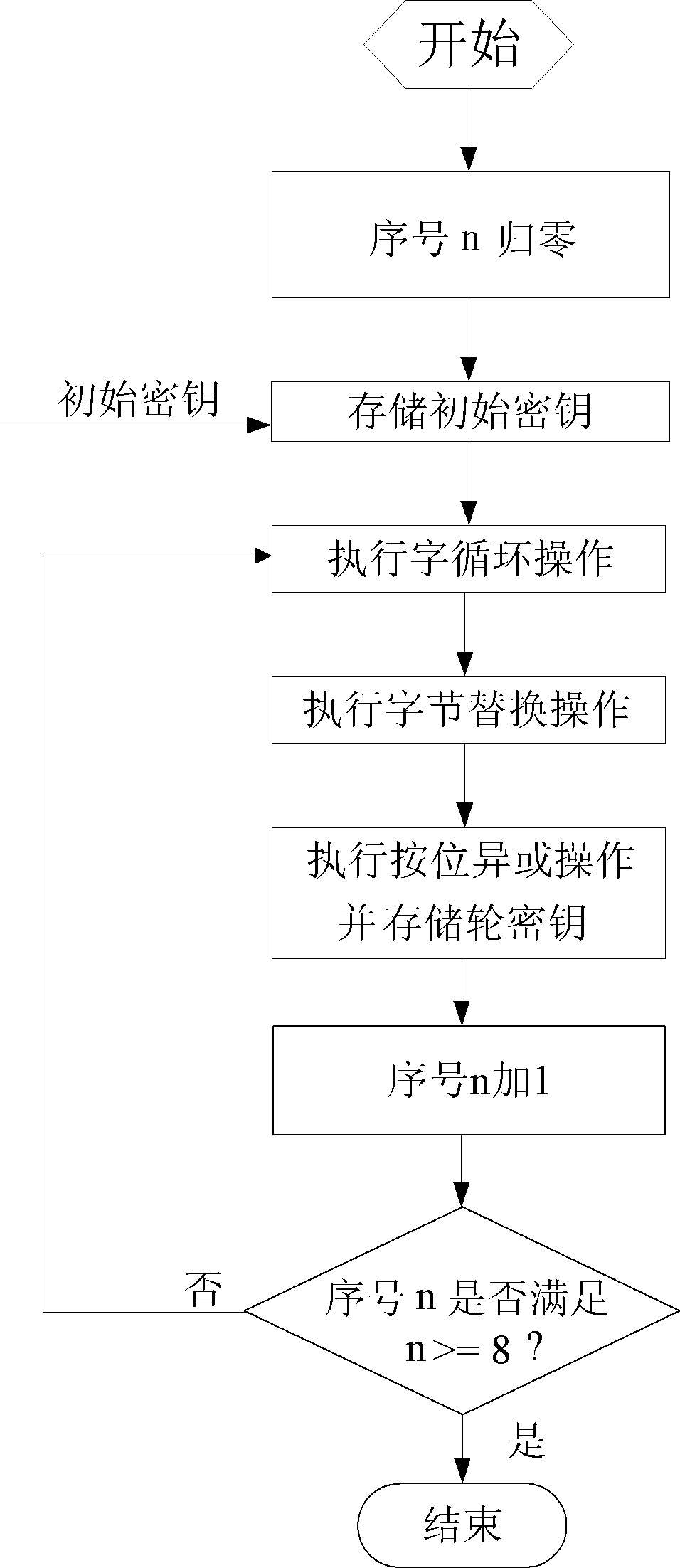
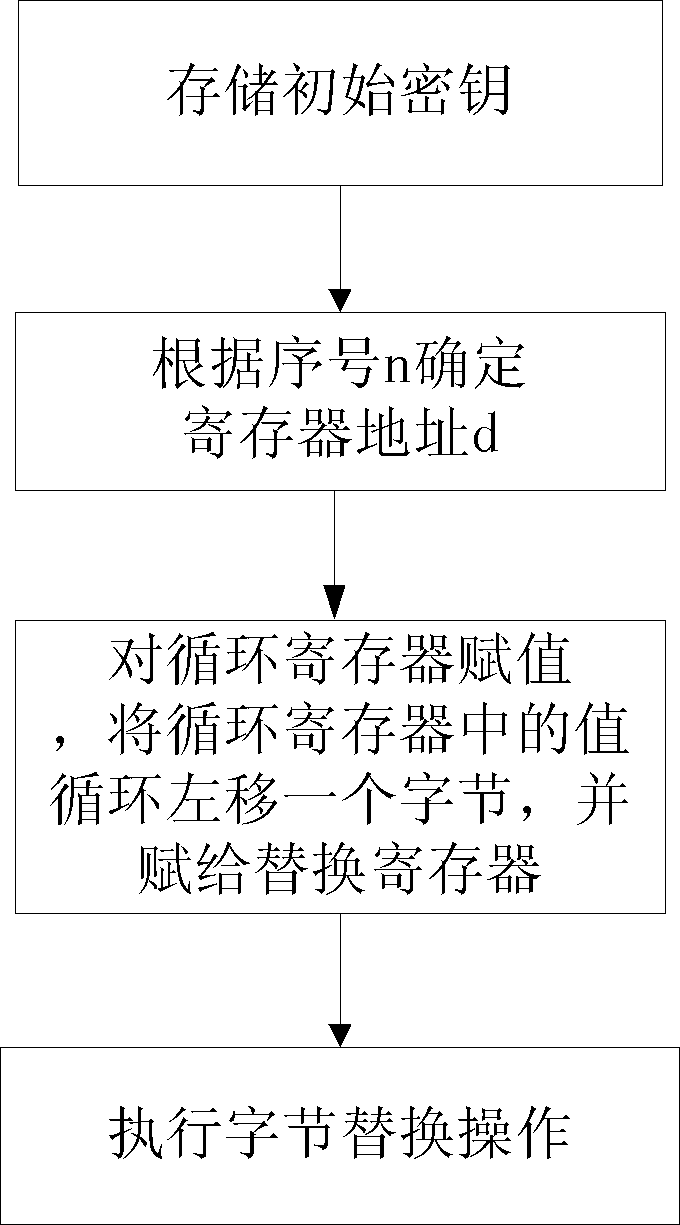
[0062] refer to figure 1 , the present invention is based on the 192-bit key expansion system of the Advanced Encryption Standard AES, comprising: an expansion counting unit 1, a temporary storage unit 2, a round key storage unit 3, a loop register 4, a word loop unit 5, a replacement register 6, a byte Replacement unit 7, S box unit 8, wheel constant selection unit 9, exclusive OR register unit 10, exclusive OR unit 11, loop control unit 12, the S box unit 8 includes 4 pre-stored ROMs with S boxes: No. 0 ROM, No. 1 ROM, No. 2 ROM and No. 3 ROM; the XOR register unit 10 includes 6 registers with a bit width of 32 bits: No. 0 register, No. 1 register, No. 2 register, No. 3 register, No. 4 register and No. 5 register; the XOR unit 11 includes 6 XOR subunits: No. 0 XOR subunit, No. 1 XOR subunit, No. 2 XOR subunit, No. 3 XOR subunit, and No. 4 XOR subunit unit and No. 5 XOR subunit. in:
[0063] The extended counting unit 1 is used to add one to the serial number n, and output...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com