A method for WFII/3G router access authentication by using fingerprint
A technology of access authentication and authentication method, which is applied in the field of WFII/3G router access authentication through fingerprints, to achieve the effect of flexible and convenient control and increased security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Further illustrate the present invention below in conjunction with specific embodiment and accompanying drawing:
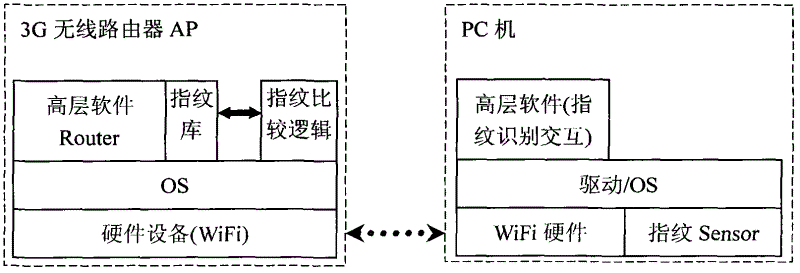
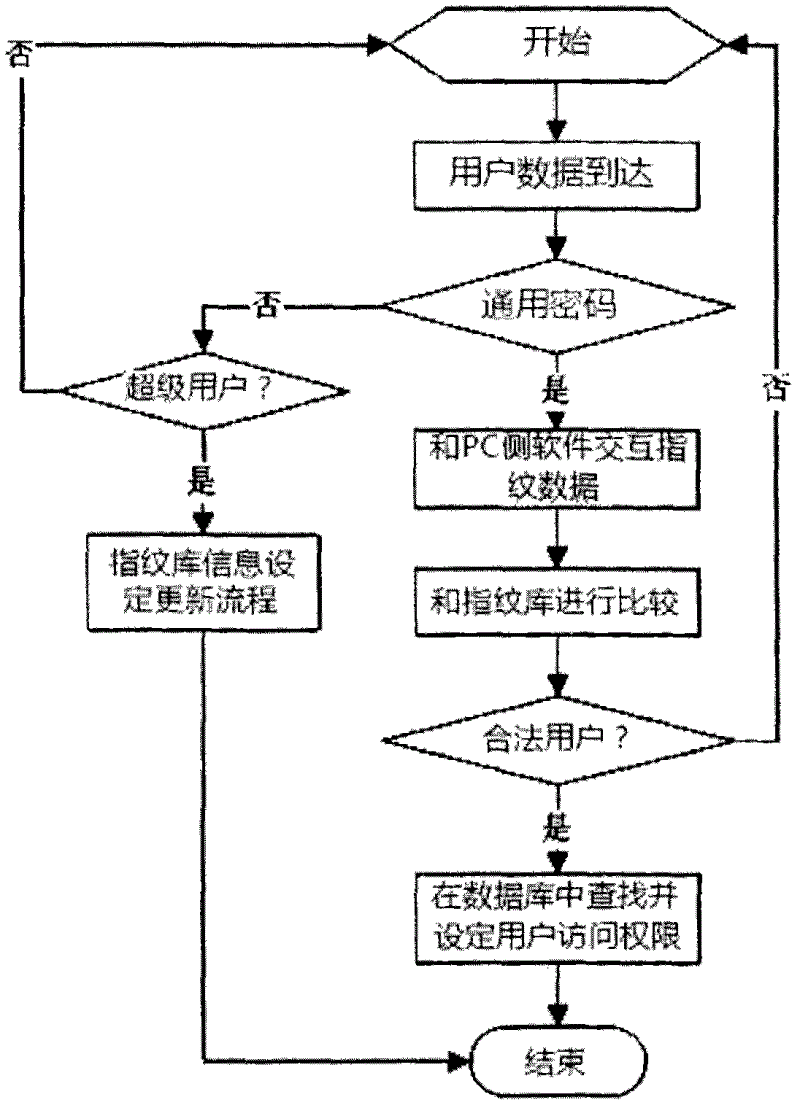
[0020] as attached figure 1 , 2 As shown, the fingerprint sensor is located on the PC or notebook and is used to enter user fingerprint information; the fingerprint database and fingerprint identification mechanism are located in the wireless router to identify user identity; the PC side software and driver provide user authentication and input and delete fingerprint information way. In the whole solution, only the super user needs to use the user name and password to authenticate the identity to add, delete, modify and set the user authority level of the fingerprint database. All the set information is kept in the 3G wireless router; the user uses the PC to open The software on the PC side of the wireless router. At this time, the PC software uses a common user name and password to connect to the wireless router (this user name and password can be set in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com