Efficient cloud storage data possession verification method
A technology of possession verification and cloud storage, which is applied in the field of cloud computing security, can solve the problems that hinder the implementation of cloud architecture and cannot guarantee data integrity and availability, and achieve reduced computing overhead, small data volume, and high confidence Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
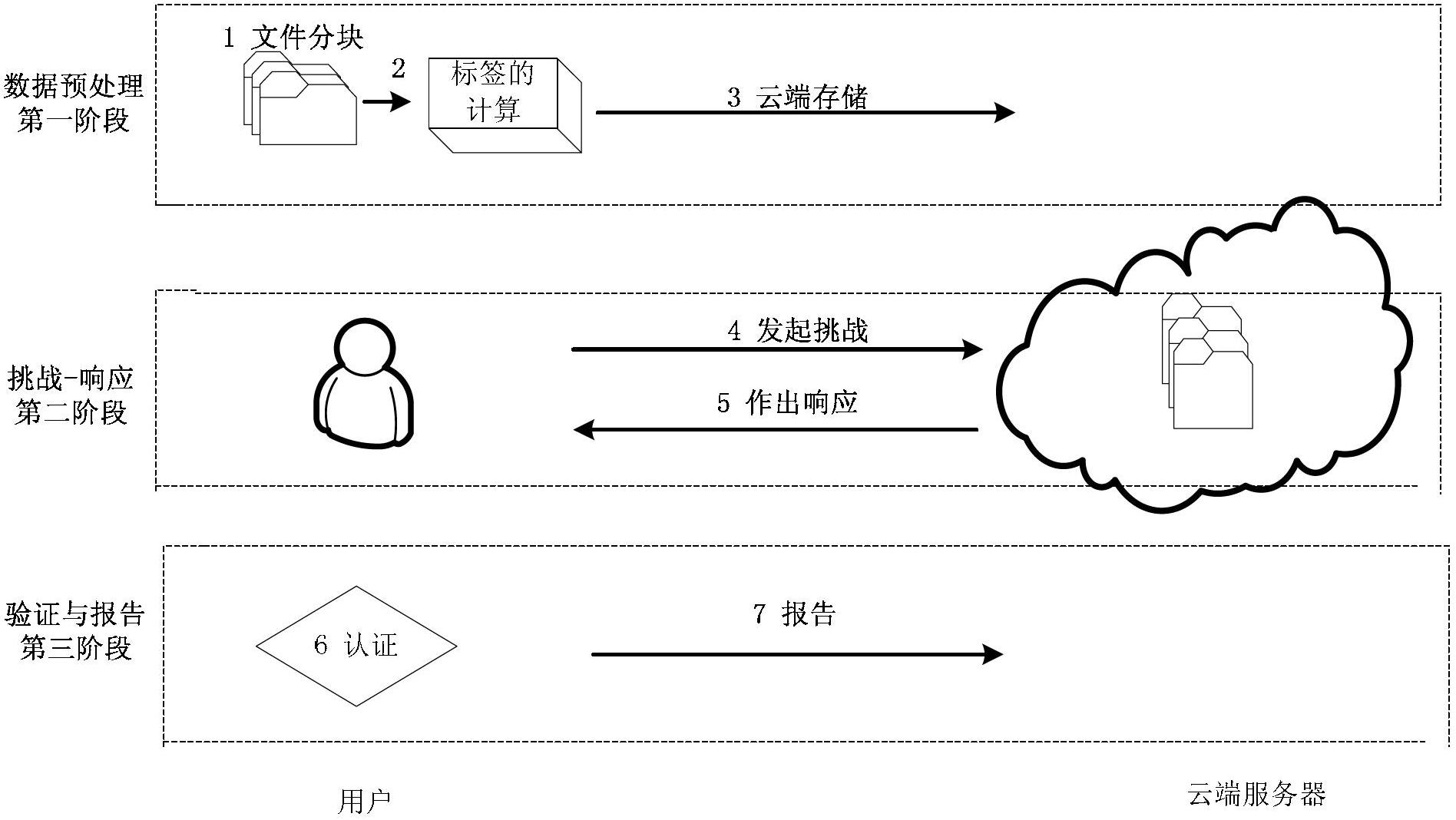
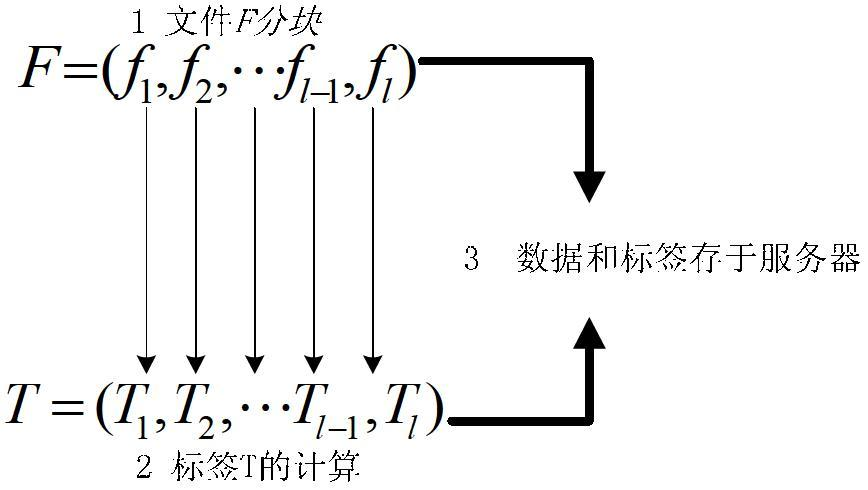
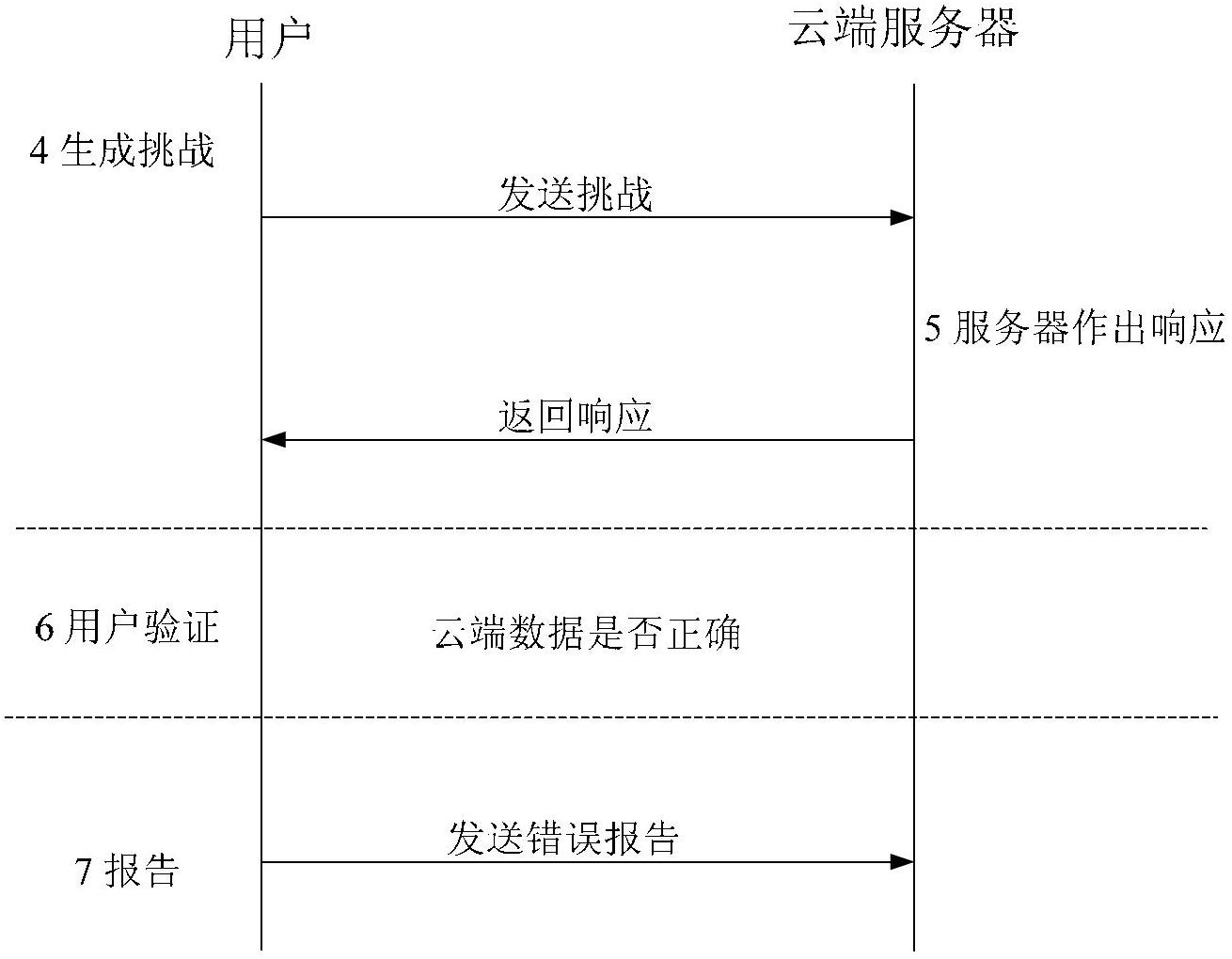
[0034] The present invention includes two entities, a user and a cloud server. The effective verification method for the data holder will be described in detail below in conjunction with the accompanying drawings. figure 1 It is a flow chart of the present invention; figure 2 is the calculation graph of the data block label in the present invention; image 3 It is an interaction flowchart of data possession authentication in the present invention.
[0035] Main symbols and algorithm explanations:
[0036] (1) π=(p,G,G T ,e,g) are system parameters, where p is a large prime number and is the order of the cyclic group G; e:G×G →G T is a non-degenerate bilinear map. G= , g is the generator of G;
[0037] (2)x 1 , x 2 ,...x l , is a random number in the group G, which is generated by a pseudo-random number generator with a key, and the user only needs to store the corresponding key k 1 ;
[0038] (3) π k ( ) is a pseudorandom permutation (PRP), which satisfi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com