Code reuse attack detection system based on dynamic binary translation framework
A dynamic binary and attack detection technology, which is applied in the field of code reuse attack detection system, can solve the problems of high performance overhead and achieve the effect of ensuring operating efficiency and optimizing execution performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and examples.
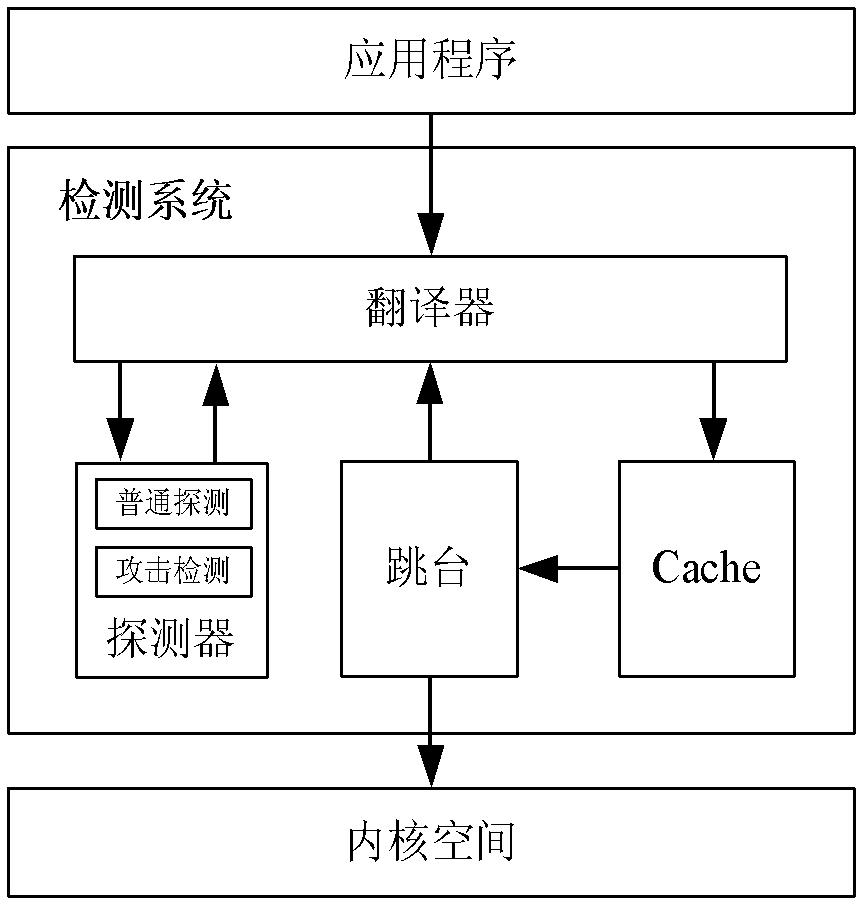
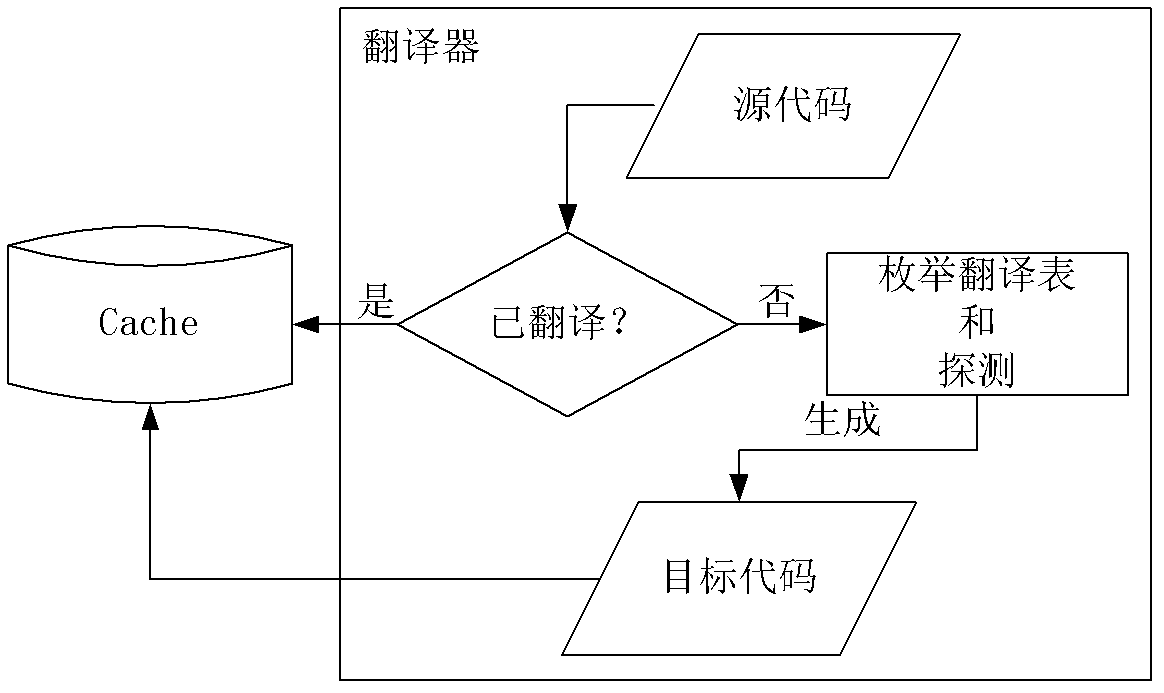
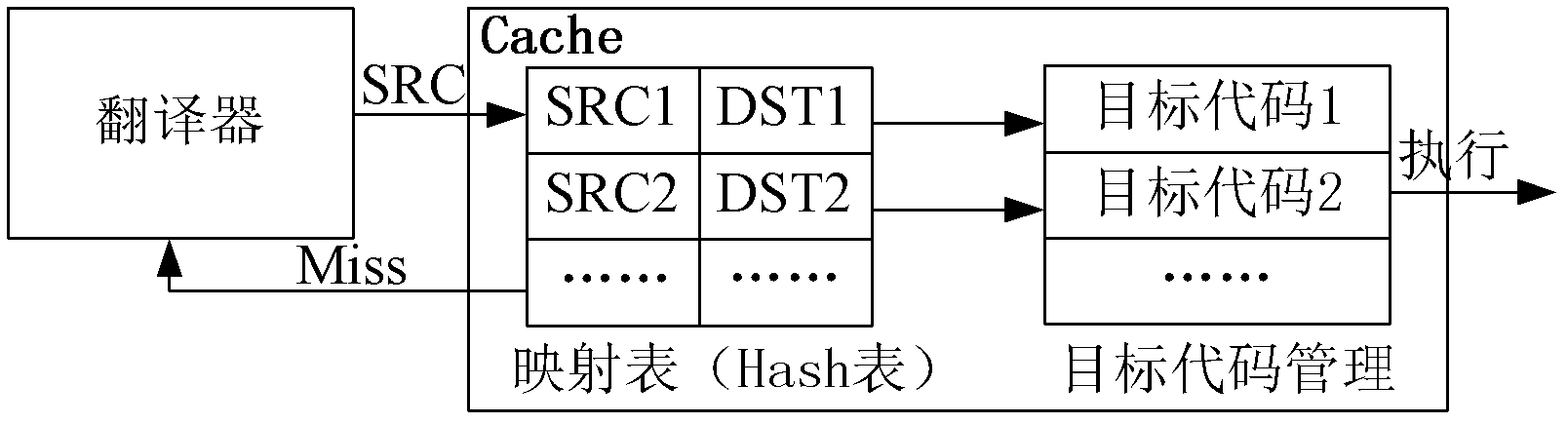
[0021] like figure 1 As shown, from the perspective of architecture, the computer system used in the present invention is mainly composed of application program, detection system and kernel space. After the application program is translated and detected by the detection system, the program is executed in the kernel space. The detection system includes four modules: translator, detector, cache, and platform. The workflow of the detection system of the present invention is as follows:
[0022] (1) The application program is loaded into the detection system of the present invention, and the detection system takes over the control right of the application program completely, and completes the system initialization work, such as Cache memory space allocation, creation and initialization of platforms, etc.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com