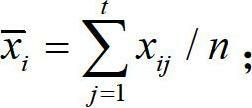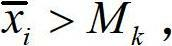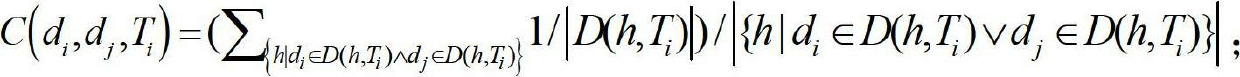Domain name server (DNS) data packet-based bot-net domain name discovery method
A technology of DNS packets and botnets, applied in the field of botnet domain name discovery based on DNS packets, can solve problems such as difficulty in applying large-scale networks, inability to effectively detect botnets, and strong limitations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to understand the method more clearly, the method will be further described in detail below through specific implementation manners in conjunction with the accompanying drawings.
[0045] figure 1 A schematic diagram of the co-occurrence behavior of botnets.
[0046] Regardless of the centralized or distributed structure of the botnet, whether it is IRC or HTTP protocol, they all have the following common features: (1) Spatial groupness. Be controlled by the same hacker or hacker organization, receive the same or coordinated attack commands, and have the same network access rules; (2) Time continuity. Zombie hosts continuously access relevant target servers (including control servers, update servers, etc.) in time, and always keep in touch with the zombie controller. Botnets usually use multiple different domain names in the process of command and control, and bot hosts will continue to access these specific domain names during their life cycle to maintain an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com