Deep recovery method for database content
A database, deep technology, applied in digital data protection, electronic digital data processing, special data processing applications, etc., to achieve the effect of ensuring security and effectively monitoring access behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
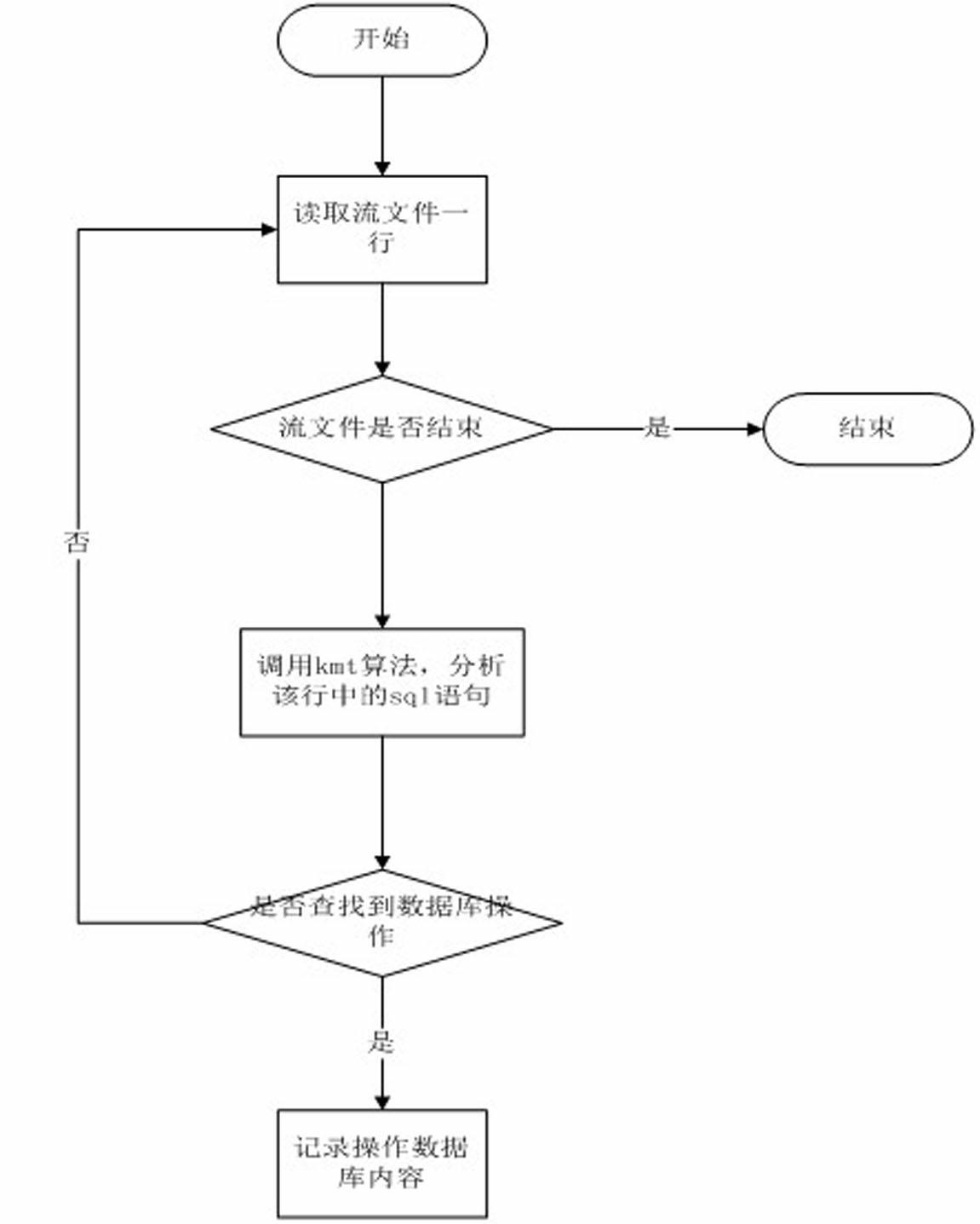
[0024] see figure 1 , the invention is realized through the following steps:
[0025] (1), preprocessing stage:
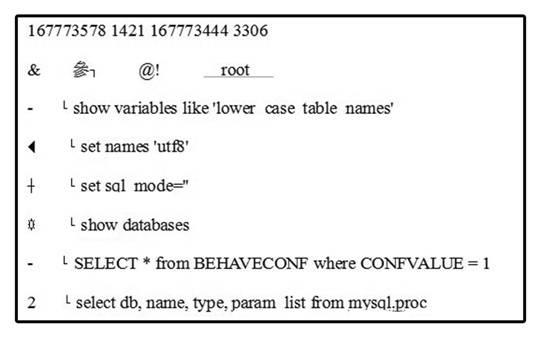
[0026] Set the network card to promiscuous mode, and use Libpcap to capture packets cyclically. Libpcap uses zero-copy technology to map user memory to the kernel. Stream write file, if there is no new data within 30 seconds for this quadruple link, the write stream file ends, and the stream file is closed, and the protocol analysis module is notified that the restore stream file has been generated, and the stream file can be read and analyzed For each row of data, obtain whether there is a database operation statement. If there is new data within 30 seconds, first judge whether the quadruple has created a file. If it has created a file, append the data to the back of the created file. If not created file, create a new file. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com