Cloud security management system of security electronic documents and method
An electronic document and security management technology, applied in the field of information security, can solve the problems of time cost and uncontrollability, and achieve the effect of high cost performance and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
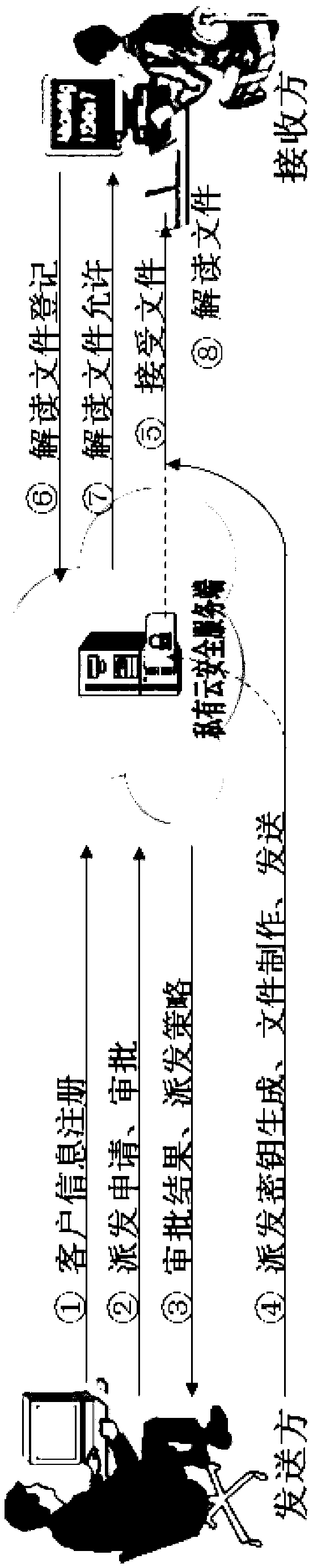
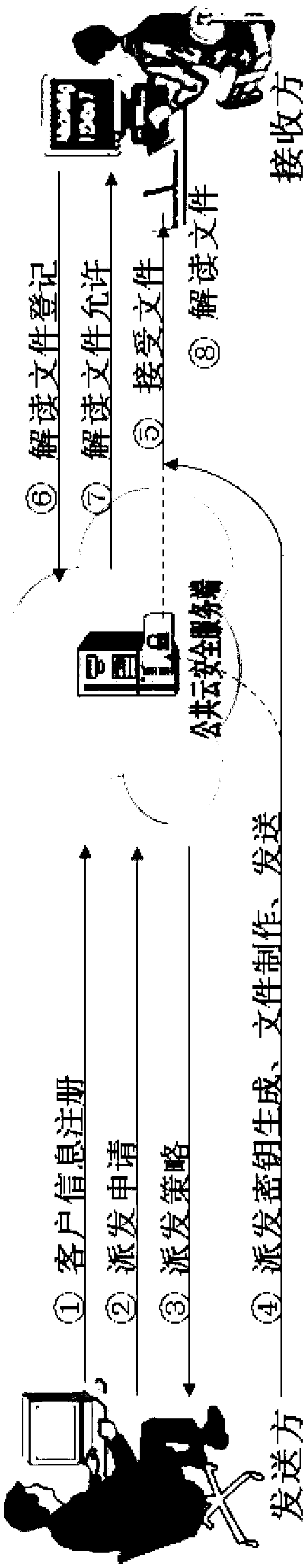
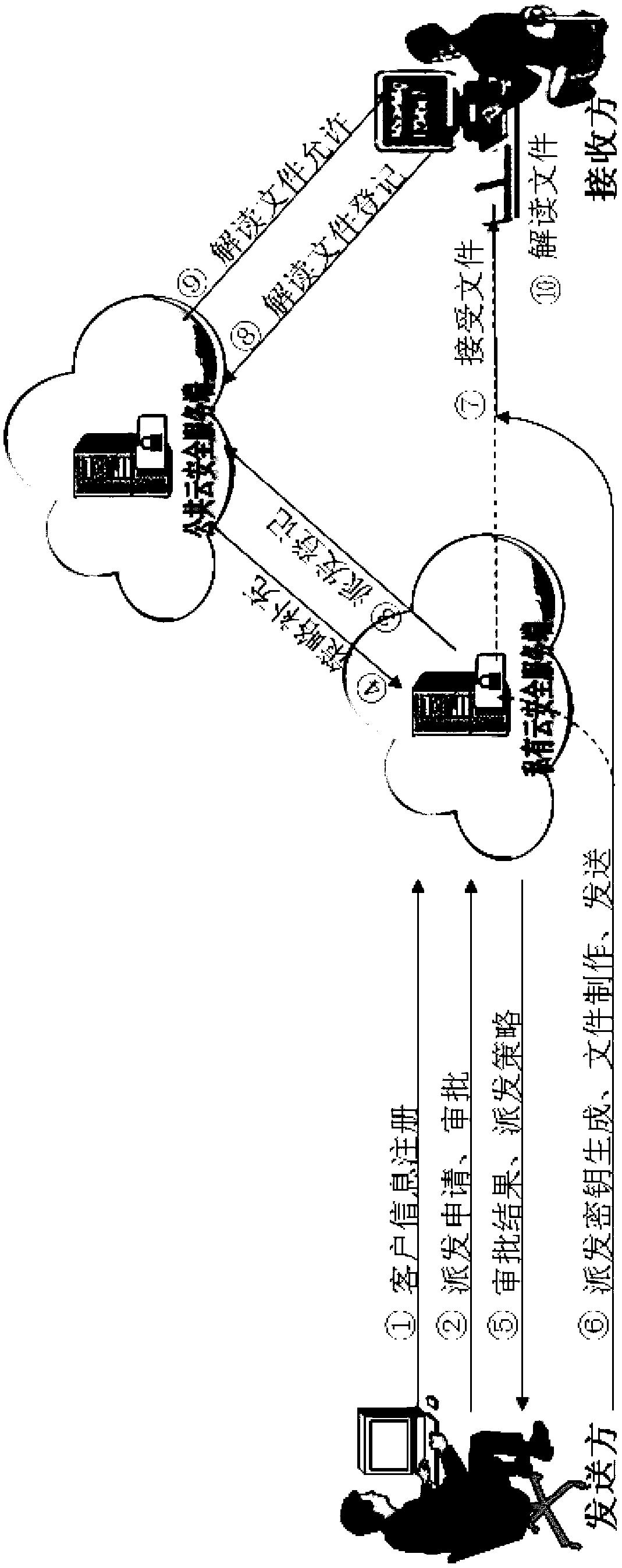
[0079] In this implementation case scenario, all design electronic files inside unit A are ciphertext electronic files, and no encryption operation is required.
[0080] If it is sent directly, even if the receiving end has installed the receiving environment, it cannot be opened.
[0081] The processing flow of the receiving end is as attached Figure 5 shown.
[0082] In this implementation case scenario, only designated terminals are allowed to browse and distribute electronic files. For the first time to distribute electronic documents, the terminal "Zhang San" device needs to be installed with a receiving environment.
[0083] There are two receiving environment installation strategies. One is to install by password. This installation mode has a higher security level, and an authorization password must be entered during installation. After successful installation, you can browse the corresponding distribution electronic files. The other is to install according to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com