A secure virtualization environment bootable from an external media device
A virtualized environment and external media technology, applied in the direction of boot programs, micro-control devices, program control devices, etc., can solve problems such as retention and endangering security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
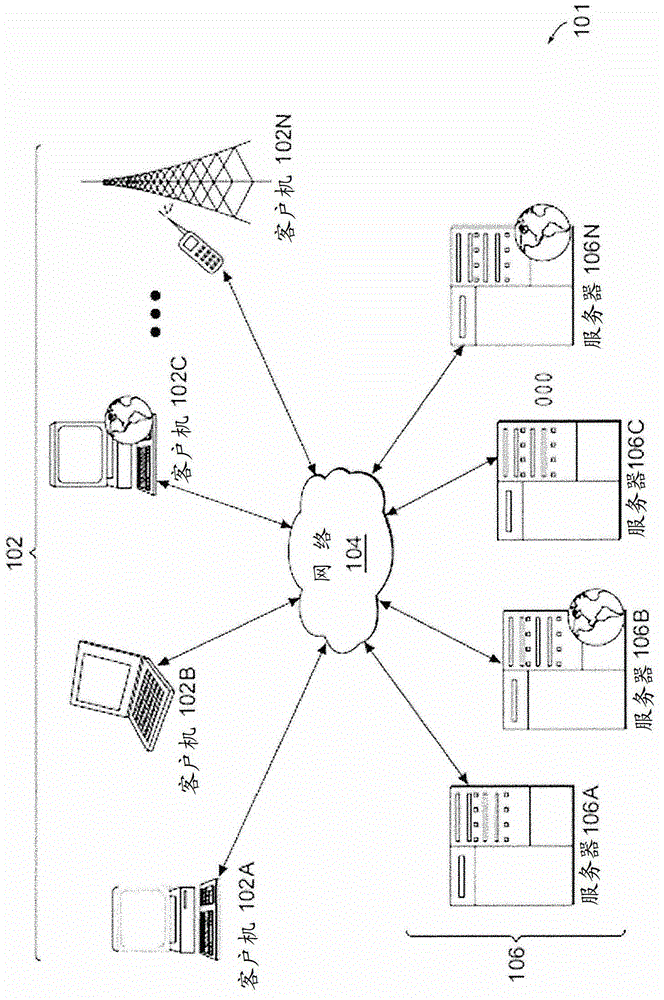
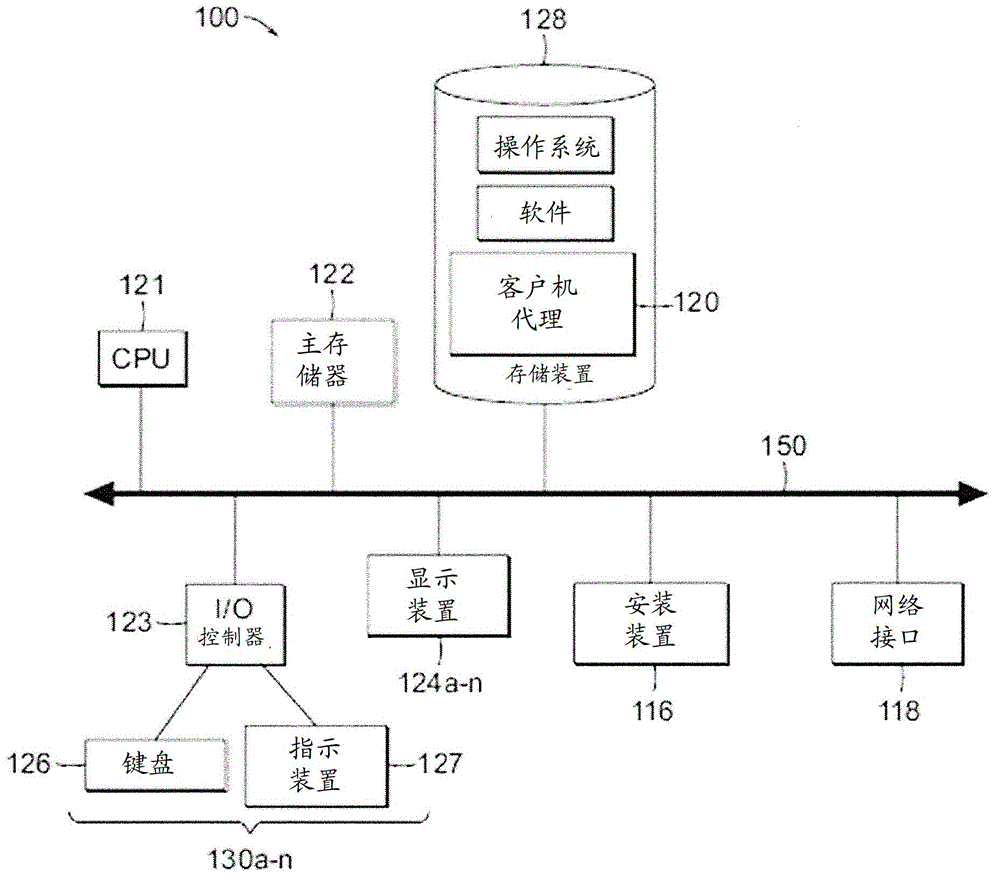
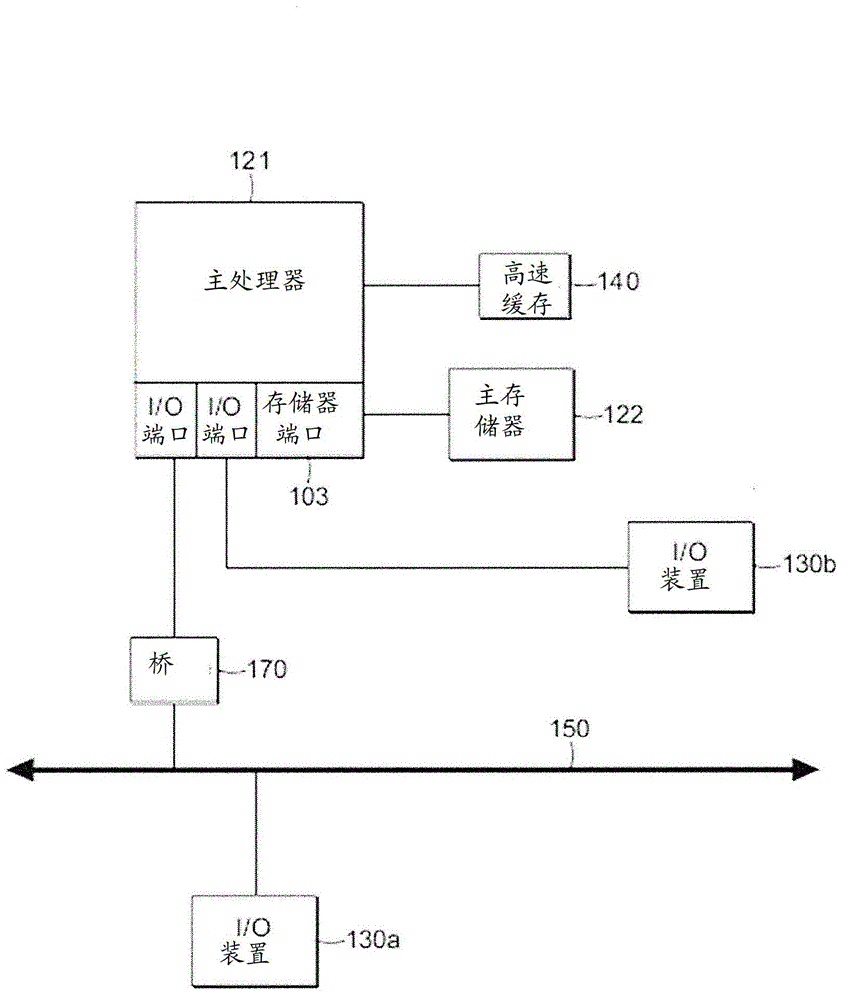
[0027] Figure 1A One embodiment of a computing environment 101 is described that includes one or more clients 102A-102N (herein collectively referred to as "client 102"). Installed between the client 102 and the server 106 is a network.
[0028] In one embodiment, computing environment 101 may include a device (not shown) installed between server 106 and client 102 . The appliance manages client / server connections and, in some cases, has the ability to load balance client connections across multiple backend servers.
[0029]In some embodiments, a client 102 may be considered a single client 102 or a single group of clients 102 and a server 106 may be considered a single server 106 or a single group of servers 106 . In one embodiment, a single client 102 communicates with more than one server 106, while in another embodiment, a single server 106 communicates with more than one client 102, and in yet another embodiment, a single client 102 communicates with a single Server 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com