Restoring protection method for magnetic disk
A disk and disk equipment technology, applied in the direction of instruments, electrical digital data processing, computer security devices, etc., can solve problems such as long time for scanning and killing, unclean virus scanning, and virus occurrence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
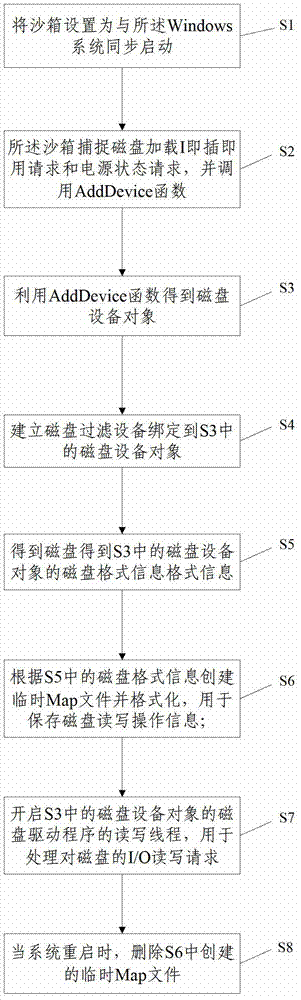
[0026] Such as figure 1 As shown, a disk recovery protection method includes the following steps:
[0027] S1: setting the sandbox to start synchronously with the Windows system;
[0028] S2: The sandbox captures the disk load I plug-and-play request and the power state request, and calls the AddDevice function; the sandbox driver software adopts the WDM driver mode. When the U disk is inserted into the computer, since the Usb bus in Windows supports PNP plug-and-play operation (PLUG AND PLAY), the insertion request of the Usb device is captured. The Usb bus driver is identified by hardware, and the corresponding driver is searched and installed, and finally the Usb dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com