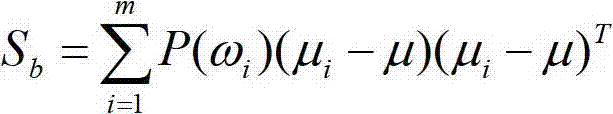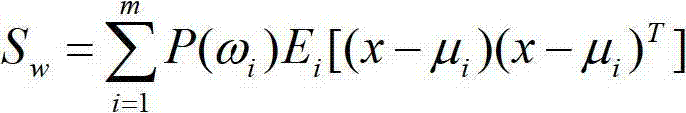Characteristic value processing method for hardware Trojan detection
A hardware Trojan detection and processing method technology, applied in the direction of electrical digital data processing, instruments, calculations, etc., can solve the problem of cost increase, and achieve the effect of saving manpower and material resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
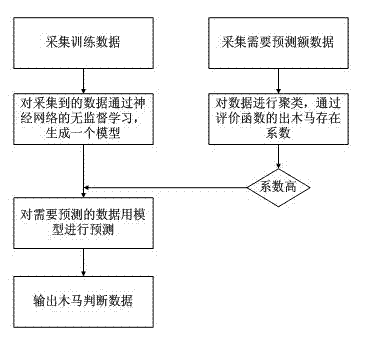
[0030] Such as figure 1 Shown:
[0031] (1) 1. First of all, the left end starts with selection step 1, modeling for the detection data: for the collected data, use the modeling algorithm to build a model, use the self-organizing competition neural network algorithm for modeling, and use the weight adjustment The learning rule is the Kohonen learning rule, the threshold value adjustment selects the threshold value learning rule, and the competition layer network is two nodes; then clustering and classification are performed;
[0032] 2. Starting from the right end is the selection step 2. No modeling is performed on the detection data, that is, the existing data is directly judged: the data to be detected is clustered and classified, and the evaluation function is used for evaluation. Through the corresponding transformation, the obtained The possible coefficient of hardware Trojans, if the number is very low, it means that this set of data is normal, and the detection of thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com