Executable file processing method and device
A technology for executing files and processing methods, which is applied in the Internet field and can solve problems such as ineffective classification of executable files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
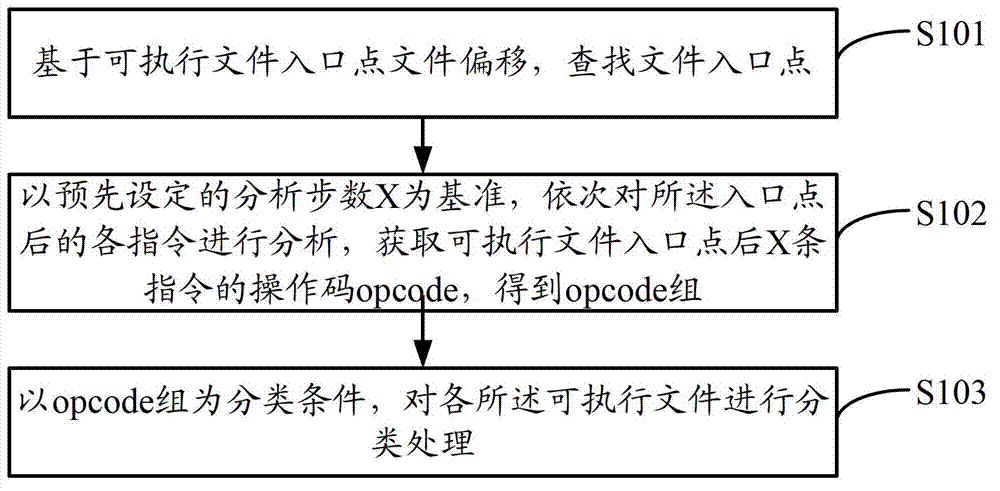
[0072] An embodiment of the present invention provides an executable file processing method, such as figure 1 shown, including:
[0073] Step S101, based on the file offset of the entry point of the executable file, search for the entry point of the executable file;
[0074] Step S102, based on the preset number of analysis steps X, analyze the instructions after the entry point in turn, obtain the opcodes of X instructions after the entry point of the executable file, and obtain an opcode group;
[0075] In this step, the preset number of analysis steps X=2 n , n is a positive integer; preferably, n is 2 or 4, that is, the number of analysis steps X is 4 or 16.
[0076] In this step, the obtained opcode group consists of the first byte of each opcode corresponding to the X instructions.
[0077] In this step, when the opcode satisfying the number of analysis steps X cannot be obtained, when forming an opcode group, the remaining bits are set to be empty; or, the currently ...
Embodiment 2
[0100] The embodiment of the present invention provides an executable file processing method. The implementation principle of this embodiment is the same as that of Embodiment 1, and it is a further detailed discussion of the technical solution described in Embodiment 1. This embodiment adopts F16 (F4) technology, specifically Involves the following:
[0101] Step 1, analyze the executable file structure and find the file offset of the entry point;
[0102] Step 2, using the disassembly engine to sequentially analyze the entry point instructions, and obtain from the disassembly engine: the length of the instruction, the instruction opcode and the instruction type;
[0103] Step 3, create an instruction stream stack to assist in the analysis of the instruction stream;
[0104] Step 4, according to the command type, perform the following actions:
[0105] Step 41, judging whether the currently analyzed instruction is a Transfer instruction, if not, execute step 42;
[0106] I...
Embodiment 3
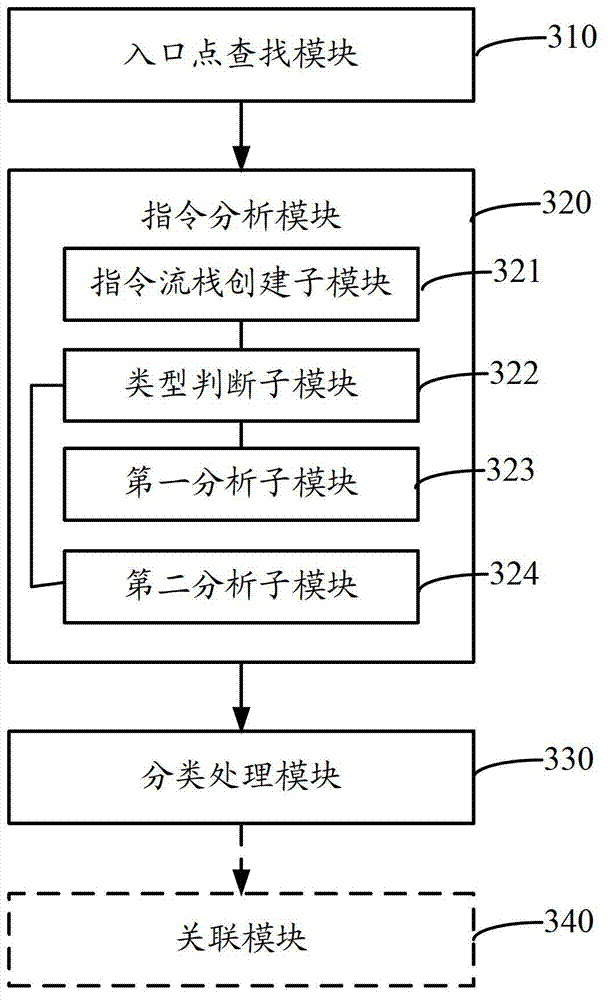
[0133] An embodiment of the present invention provides an executable file processing device, such as image 3 As shown, it includes: an entry point search module 310, an instruction analysis module 320 and a classification processing module 330;
[0134] The entry point search module 310 is configured to search for the entry point of the executable file based on the file offset of the entry point of the executable file;
[0135] The instruction analysis module 320 is used to analyze the instructions after the entry point sequentially based on the preset number of analysis steps X, obtain the opcodes of X instructions after the entry point of the executable file, and obtain the opcode group ;
[0136] The classification processing module 330 is configured to use the opcode group as a classification condition to perform classification processing on each of the executable files. Wherein, the classification module 340 specifically classifies the executable files of the same opco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com