Safe development method for application middleware of mobile internet intelligent terminal
A mobile Internet and smart terminal technology, applied in the development security of smart terminal application middleware and mobile Internet security, can solve the problems of user privacy data theft, unrevocable permissions, uncontrollable API sequence, etc., to achieve the effect of protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further described below in conjunction with the accompanying drawings.
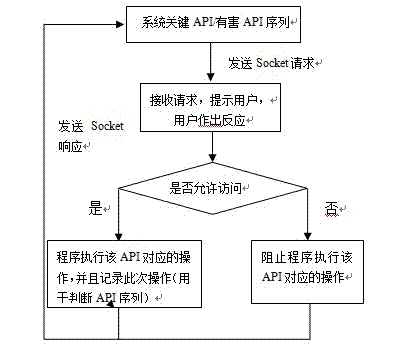
[0055] The security framework uses static code detection technology to determine the security level of the program and the program's security holes, and uses dynamic active defense technology to realize the real-time withdrawal of the permissions given to the application program during installation according to the user's choice.
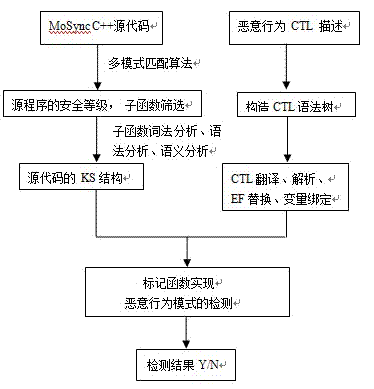
[0056] Static code detection technology is adopted on the platform side, and we have designed a security detection client (HIT_Security Guard) to realize dynamic and active defense. The overall structure of the framework is as figure 1 and 2 Shown:
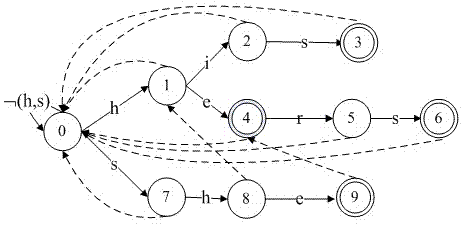
[0057] On the platform side, before the source code of MoSync is packaged, the semantic verification of the source code is firstly performed using model checking technology. First, use the multi-pattern matching algorithm to determine the security level of the program (this step is mainly to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com