Phonetic empathy Hash content authentication method capable of implementing tamper localization
A technology of perceptual hashing and authentication methods, applied in speech analysis, instruments, etc., can solve the problems that tampering and positioning cannot be realized, and the efficiency is not very high, and achieve the effect of high authentication efficiency and simple construction process
Inactive Publication Date: 2013-02-06
LANZHOU UNIVERSITY OF TECHNOLOGY
View PDF4 Cites 11 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
These algorithms can effectively detect malicious tampering, but the efficiency is not very high, and tampering cannot be achieved.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
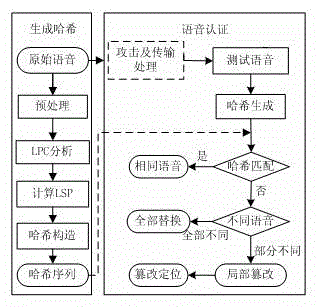
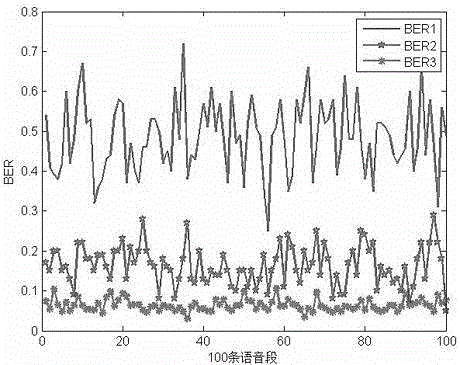
The invention relates to a phonetic empathy Hash content authentication method capable of implementing tamper localization. The method comprises the following steps: pre-processing a voice signal, carrying out 10-order linear prediction analysis on each frame of the voice signal, and acquiring an LSP (line spectral pair) coefficient through the discrete Fourier transformation as the empathy characteristics; grouping the voice data in sequence, combining LSP coefficient weighted expectations of each group of the voice data as the final authentication data, and compressing the authentication data volume through a Hash structure; and finally, quickly authenticating the voice contents through the Hash match. The method can keep robustness for the operations such as changing the sound volume, resounding and resampling, is sensitive to malicious operations such as replacement and deletion, can accurately locate the tamper area, has the characteristics of low authentication data volume and high operation efficiency, and is suitable for resource-limited voice communication terminals.
Description
technical field [0001] The invention belongs to the field of multimedia information security. Based on the voice perception hash technology, an efficient voice content authentication method capable of realizing accurate positioning of tampered areas is proposed, which can be used for content authentication in voice communication and can realize accurate positioning of tampered areas. Background technique [0002] With the rapid development of digital signal processing technology, mobile communication technology and the Internet and other technologies, the forgery of audio data tends to be concealed and can be carried out at a very low cost. Therefore, the demand for content integrity authentication of audio data is increasing. Voice is an important part of audio, and its integrity is very important in applications such as news reports, telephone communications, financial transactions, and e-government affairs. The semantics of speech can be changed by simply rearranging or ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G10L19/087G10L25/45
Inventor 张秋余邸燕君黄羿博陈海燕刘扬威省鹏飞杨仲平
Owner LANZHOU UNIVERSITY OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com