Credible security route of wireless sensor network on basis of quantum ant colony algorithm
A wireless sensor and ant colony algorithm technology, applied in the field of network security, can solve the problems of local optimal solution and slow convergence speed, and achieve the effect of reducing design complexity and energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
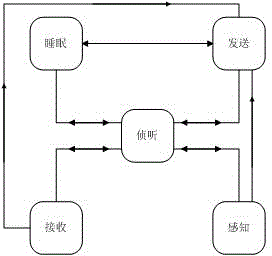
[0051] The wireless sensor network trusted security routing based on the quantum ant colony algorithm is characterized in that the specific operation steps for determining the routing are as follows:
[0052] 1) Set the initial pheromone: set the number of ants as , the sensor network space size is , the sink node is ; Initialize pheromone , the initial number of iterations , is the maximum number of iterations set; the initial shortest path ; Determine the size of the area according to the number of ants and the size of the space, and place each ant in each search area;
[0053] 2) Determining the visibility function: calculating the arrival at the sink node path of distance , visibility function, pheromone level, and transition probability;
[0054] 3) Path selection: No. Ants choose to reach the sink node according to the size of the credibility and record the path, and release pheromone at the same time, the shorter the path, the greater the possibil...
Embodiment 2
[0060] This embodiment is basically the same as Embodiment 1, and the special features are:
[0061] The method for initializing the pheromone in the described step 1) is: in the establishment of the ant colony ants, each ant carries Qubits, all possible ways from the source node to the destination node in the wireless sensor network are defined as paths in the quantum ant colony algorithm. exist destination node the path of ; Let the ant colony No. generation contains The population of individuals is , where the first initial pheromone for:
[0062] (6)
[0063] In the formula, the initial number of iterations , is the number of qubits, are the two probability amplitudes of the qubit, at the beginning average .
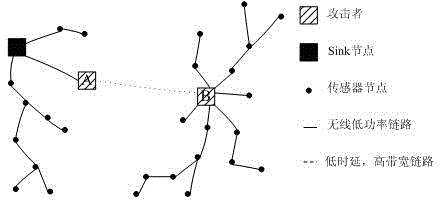
[0064] The method of calculating the visibility function in the step 2) is: the visibility function is mainly determined according to the credibility of the nodes, and according to the three basic indicator...
Embodiment 3
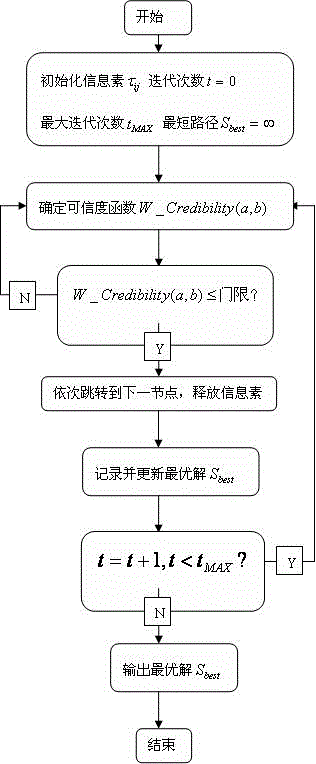
[0080] see Figure 1~Figure 3 , the present invention is based on the quantum ant colony algorithm to determine the trusted security routing of the wireless sensor network, the specific operation steps are as follows:
[0081] 1) Initialize pheromone
[0082] Let there be a total of ants, each ant carries qubits; all possible ways from the source node to the destination node in the wireless sensor network are defined as paths in the quantum ant colony algorithm, there is destination node the path of ; Let the ant colony No. generation contains The population of individuals is , where the first initial pheromone for:
[0083] (11)
[0084] In the formula, the initial number of iterations , is the number of qubits, are the two probability amplitudes of the qubit, at the beginning average .
[0085] 2) Visibility function
[0086] The relevant parameters about the idea of trusted network include the following calculations: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com